Image Credit: @mitrecaldera
A newly discovered vulnerability in MITRE Caldera, tracked as CVE-2025-27364, has been assigned a critical CVSS score of 10, indicating its severe impact on affected systems. This Remote Code Execution (RCE) flaw stems from the dynamic agent compilation functionality in MITRE Caldera versions through 4.2.0 and 5.0.0 before commit 35bc06e. If successfully exploited, the vulnerability allows attackers to execute arbitrary code remotely on the server hosting Caldera, posing a significant risk to security teams and penetration testers relying on the platform.
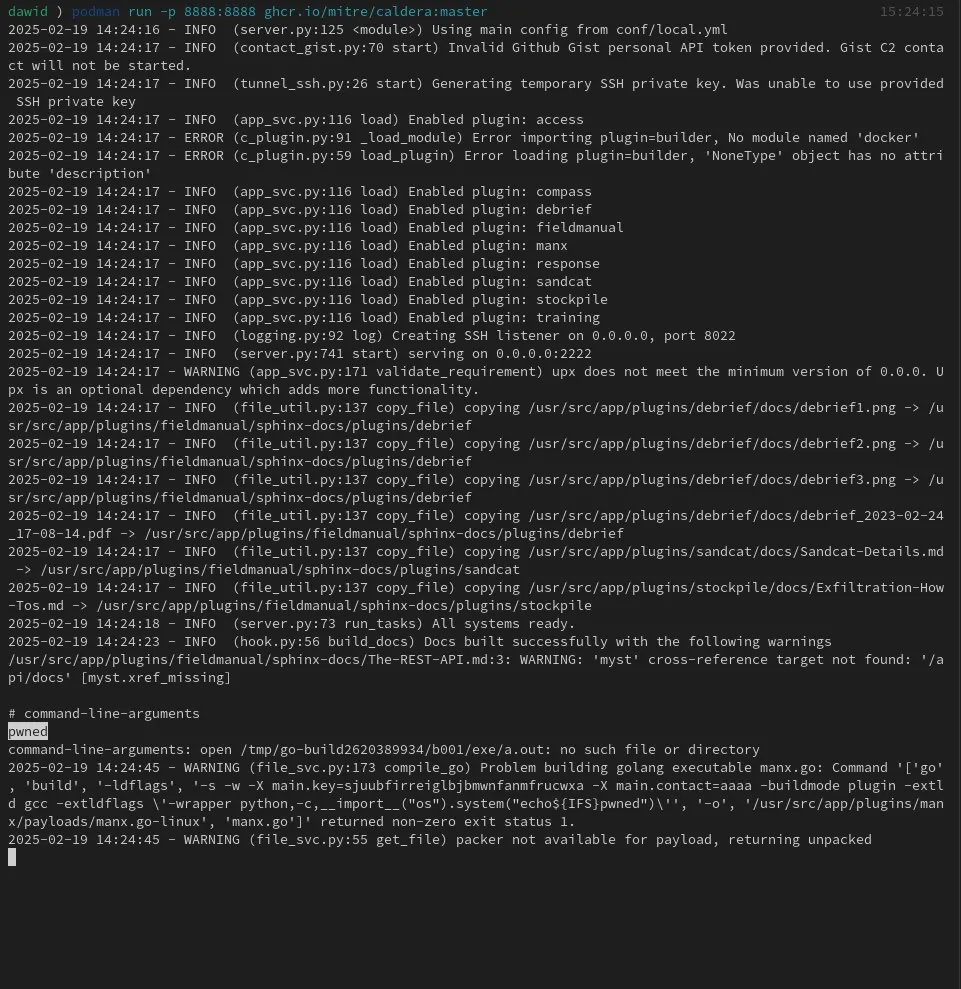
Security researcher Dawid Kulikowski detailed the exploit, providing technical insights into how attackers can craft a malicious web request to the Caldera API to compile and deploy rogue Sandcat or Manx agents (implants). The flaw exists due to the way Caldera handles compilation parameters, allowing attackers to pass arbitrary commands via the gcc -extldflags linker flag.
As Kulikowski explains in his report: “All versions of MITRE Caldera (before commit 35bc06e and going back as far as the very first versions of Caldera) are vulnerable to a remote code execution (RCE) vulnerability that can be triggered in most default configurations.”
This means that any system running a vulnerable version of Caldera is at risk, provided it has Go, Python, and GCC installed—which are default dependencies for full Caldera functionality. In many environments, these dependencies are pre-installed, making exploitation significantly easier.
The root of the issue lies in how Caldera dynamically compiles its agents for execution. Attackers can manipulate Caldera’s HTTP(S) endpoint, which handles agent downloads and execution parameters, to inject malicious commands during the compilation process.
“Looking at Caldera’s source code, the author initially took note of this compilation endpoint as it is not authenticated, meaning any vulnerability found would likely not require any knowledge of credentials,” the researcher writes.
This lack of authentication further increases the risk, as attackers do not need valid credentials to exploit the system. By leveraging the -extldflags linker flag, an attacker can execute arbitrary binaries on the target server, using a technique that abuses the GCC wrapper functionality:
“The approach was validated after the author quickly skimmed through the documentation of gcc: gcc -c t.c -wrapper gdb, — args. This will invoke all subprograms of gcc under gdb — args, thus the invocation of cc1 will be gdb — args cc1 ….”
This abuse enables attackers to execute their own payloads without any restrictions, effectively giving them full control over the compromised Caldera server.
Kulikowski published a proof-of-concept (PoC) exploit, demonstrating how an attacker can execute arbitrary commands on a vulnerable MITRE Caldera server using a simple cURL request.
While the researcher omitted key details to prevent script kiddies from easily replicating the attack, he mentioned that a Metasploit module is in development, which could further increase the weaponization of this vulnerability.
The MITRE Caldera team has patched the CVE-2025-27364 vulnerability in the latest versions of the platform (commit 35bc06e and v5.1.0+). Users are urged to immediately update their installations to prevent exploitation.