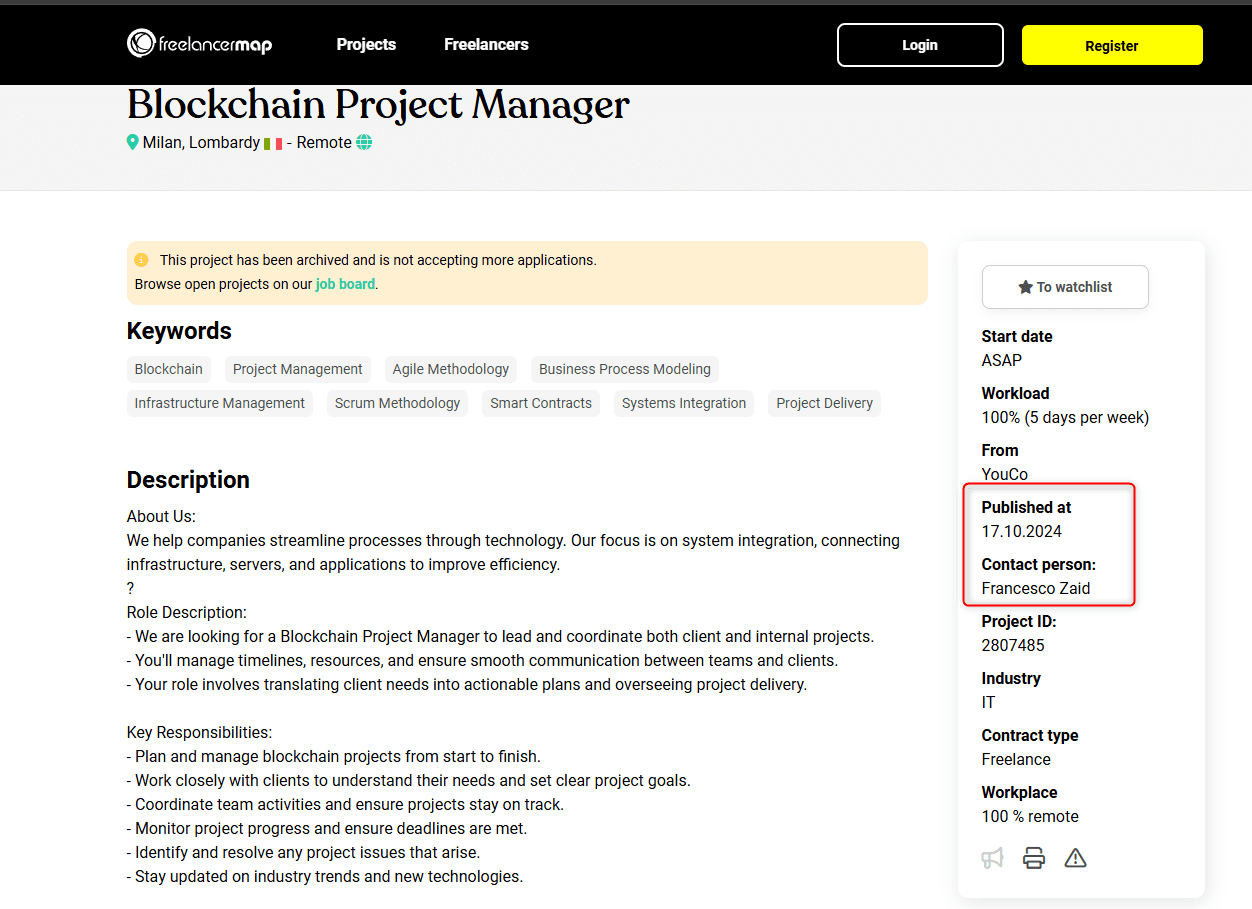
Possible Fake Job posting associated with the Contagious Interview Campaign. | Image: TRU
The eSentire Threat Response Unit (TRU) recently uncovered a sophisticated attack involving the BeaverTail and InvisibleFerret malware strains. These tools, linked to North Korean threat actors, exemplify the evolving tactics cybercriminals use to compromise software developers and their systems.
In October 2024, eSentire’s TRU team responded to an incident where a software developer unknowingly executed BeaverTail malware by installing a JavaScript project through NPM. This initial infection acted as a gateway, deploying InvisibleFerret malware via a Python script. As eSentire describes, “The InvisibleFerret malware was executed through a Python command, which fingerprinted the host’s information and stole the browser’s credentials“.
The infection began with a ZIP file, “task-space-eshop-aeea6cc51a7c.zip,” downloaded from a fraudulent BitBucket repository. The malicious project, allegedly uploaded by “francesco zaid,” aligns with tactics used in previous Contagious Interview campaigns where threat actors lure victims with fake job postings.
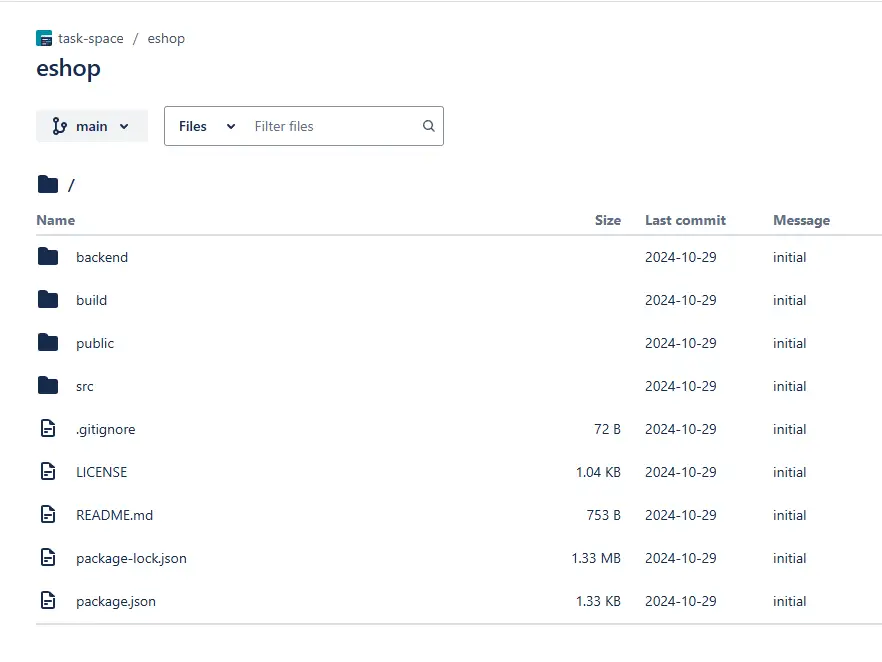
The BeaverTail malware used the infected system to download and execute InvisibleFerret components. The initial Python script, saved as .sysinfo, acted as a loader, initiating multiple malicious payloads targeting the victim’s machine.
These components included:
- Browser Credential Theft: Targeting Chrome, Brave, and other browsers, BeaverTail exfiltrated credentials and crypto wallet configurations.
- Crypto Wallet Enumeration: The malware scanned for extensions like Exodus and Solana, stealing sensitive wallet data.
- Payload Deployment: InvisibleFerret’s three main components — pay, brow, and mlip — executed fingerprinting, credential theft, and clipboard logging
InvisibleFerret is a modular, multi-platform malware designed to extract valuable data while evading detection. Its pay component focused on host fingerprinting and remote access, while brow targeted browser credentials, and mlip acted as a keylogger and clipboard stealer.
One of the key functionalities involved scanning for and exfiltrating private keys and mnemonic phrases, particularly from crypto wallets. As eSentire notes, “Any system found infected with InvisibleFerret should assume these keys are compromised and take appropriate action.”
As threat actors like North Korea’s Lazarus Group expand their tactics, vigilance, and robust security practices are paramount. For developers and organizations alike, the message is clear: trust, but verify. Always scrutinize the source before opening the door to your digital workspace.
Related Posts:
- North Korean Hackers Launch Job Interview Scam to Deploy BeaverTail and InvisibleFerret Malware
- Developers Targeted: North Korean Hackers Deploy “BeaverTail” Malware via NFTs
- North Korean Threat Actors Targeting Tech Job Seekers with Contagious Interview Campaign
- Contagious Interview & WageMole: North Korea’s New Cyber Espionage Campaigns
- Fake Browser Updates Drop Dangerous FakeBat Malware – Don’t Be Fooled