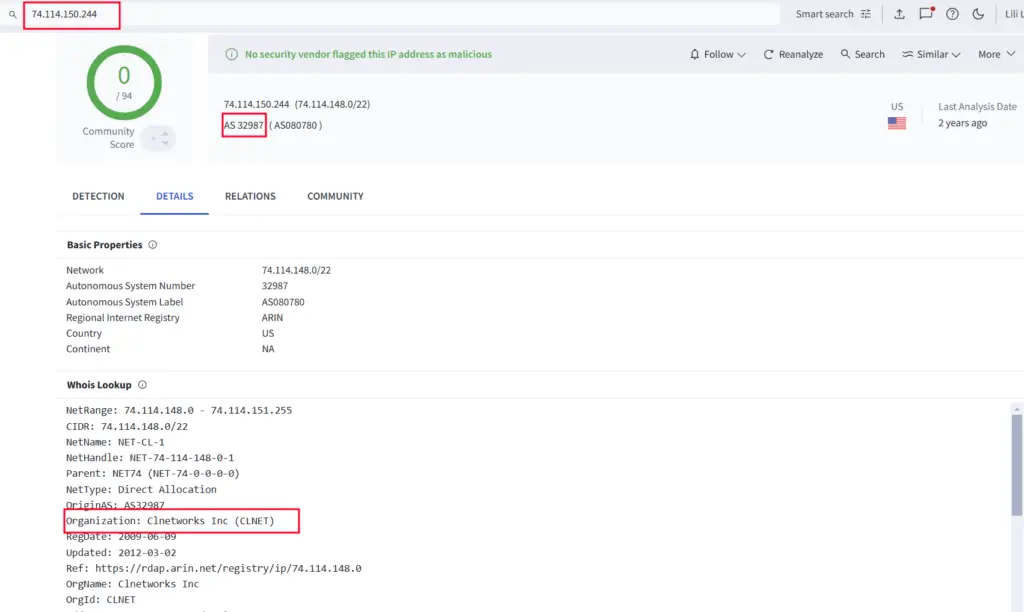
IP Details for 74.114.x.x | Image: JUMPSEC
A new report from JUMPSEC’s Detection and Response Team (DART) uncovers a disturbing trend: cybercriminals are increasingly exploiting health-related fears to carry out sophisticated phishing attacks. The report details an incident where attackers used a series of phishing emails with a common theme: health products.
“These emails were designed to trick victims potentially concerned about their health, into clicking malicious links,” the report states.
The emails employed a variety of lures to entice potential victims. Some of the subject lines included:
-
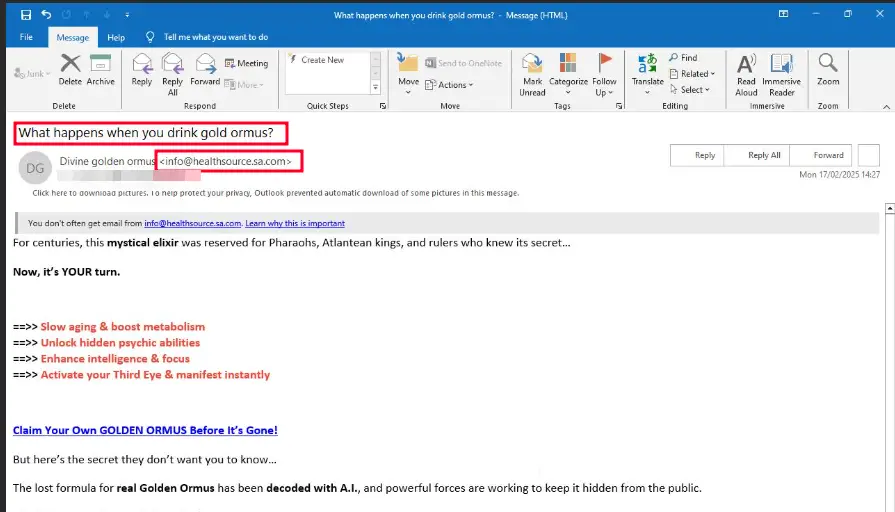
“What happens when you drink gold ormus?”
-
“Weird Sudanese Sugar Trick Drops A1C & Melts Fat”
-
“Conquer neuropathy pain by sleeping in this position (Cleveland Clinic research)”
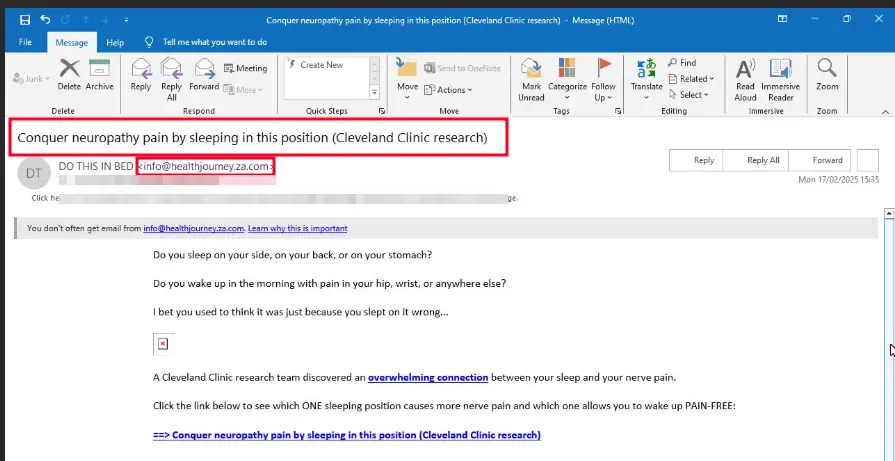
These subject lines illustrate the attackers’ attempts to capitalize on common health concerns and anxieties.
The phishing campaign was not a simple one-off attempt. It followed a multi-stage process aimed at deceiving victims and extracting sensitive information such as bank details and account credentials.
The process involved:
-
Sending health-related emails with malicious links.
-
Redirecting victims to a “Human Verification Check” page designed to appear legitimate.
-
Redirecting victims again to a shopping website for phishing purposes.
-
Tricking victims into entering payment details on a payment page hosted on ClickBank, a legitimate online marketplace often used by scammers.
JUMPSEC’s DART team went beyond just responding to the immediate threat; they also investigated the infrastructure used by the attackers.
“Unlike reactive security measures that wait for alerts to trigger, high-quality threat hunting is proactive, seeking to identify threats before they cause significant damage,” the report emphasizes.
Their investigation revealed that multiple sender domains were likely operated by the same threat actor. Researchers were able to connect the dots by analyzing shared host keys, IP addresses, and network behaviors.
The report highlights the use of Cloudflare’s services to mask phishing attempts. “Using CLOUDFLARENET for hosting phishing websites shows how hackers are widely using legitimate platforms to carry out attacks,” the report states.
The investigation also uncovered a repeat offender using similar tactics. Furthermore, many of the identified IP addresses belonged to AS-36352, a network with a poor reputation and a history of malicious activity. “This network was associated with multiple malicious activities, making it a key focus of our investigation,” the report notes.
The report concludes with a call for companies to prioritize security awareness training for users and enhance email security measures to combat these increasingly sophisticated phishing attacks.