Breach flowchart
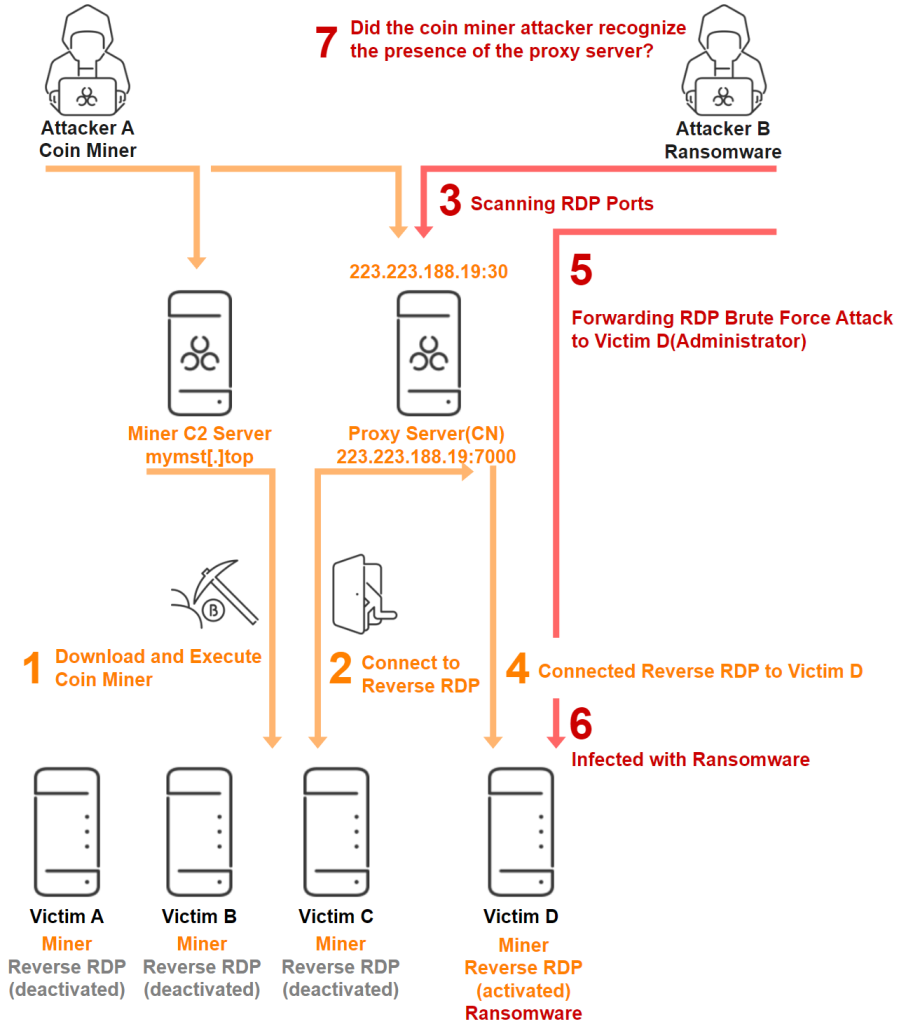
In an unexpected twist of cybercrime, security researchers at AhnLab Security Intelligence Center (ASEC) have revealed a bizarre case of one criminal gang inadvertently aiding another. A CoinMiner, a type of malware that hijacks systems to mine cryptocurrency, unwittingly left a backdoor open, allowing a ransomware gang to infiltrate and infect their network.
This unprecedented scenario unfolded as the CoinMiner, utilizing a proxy server to control its botnet, unknowingly exposed the server’s Remote Desktop Protocol (RDP) port. This vulnerability was quickly exploited by the ransomware group, who were scanning the internet for open RDP ports to launch brute force attacks.

The ransomware actors were then able to gain access to the CoinMiner’s botnet, effectively taking control of a vast network of already compromised machines. It remains unclear if this was intentional or a lucky break for the ransomware gang.
The ASEC report posits two hypotheses regarding the ransomware attack on the CoinMiner’s proxy server:
Hypothesis 1: Pure Accident
The ransomware attacker may have unintentionally targeted the CoinMiner’s proxy server. This hypothesis is supported by the fact that the attacker did not use the existing administrator account created by the CoinMiner attacker but instead launched a general scan attack.
Hypothesis 2: Intentional Attack
Alternatively, the ransomware attacker might have realized they were targeting another threat actor’s infrastructure and exploited it deliberately. The report suggests that the ransomware attacker may have noticed repeated control over different systems connected to the same proxy server, indicating an understanding of the CoinMiner operation.
This incident sheds light on a concerning trend: cybercriminals are not only targeting individuals and organizations but also exploiting vulnerabilities in each other’s infrastructure. The collateral damage of this digital turf war could potentially impact a far larger number of victims.
“This case is different from other attack cases,” warned ASEC researchers. “If the cases of similar attacks in which a threat actor uses other threat actors’ infrastructures accumulate, more and more threat actors may purposefully breach into other threat actors’ infrastructure and use them to launch different kinds of attacks.”
This development underscores the escalating complexity and unpredictability of the cybersecurity landscape. As threat actors become more sophisticated and opportunistic, even those involved in illicit activities are not immune to attacks.