Cybercriminals Escalate Attacks Exploiting Microsoft SmartScreen Flaw (CVE-2024-21412)
A concerning report from Cyble Research and Intelligence Labs (CRIL) has revealed a surge in cyberattacks exploiting the patched Microsoft Defender SmartScreen vulnerability (CVE-2024-21412). This flaw, initially leveraged in sophisticated campaigns by the DarkGate and Water Hydra threat groups, is now being widely abused by cybercriminals to deploy information-stealing malware like Lumma and Meduza Stealer.
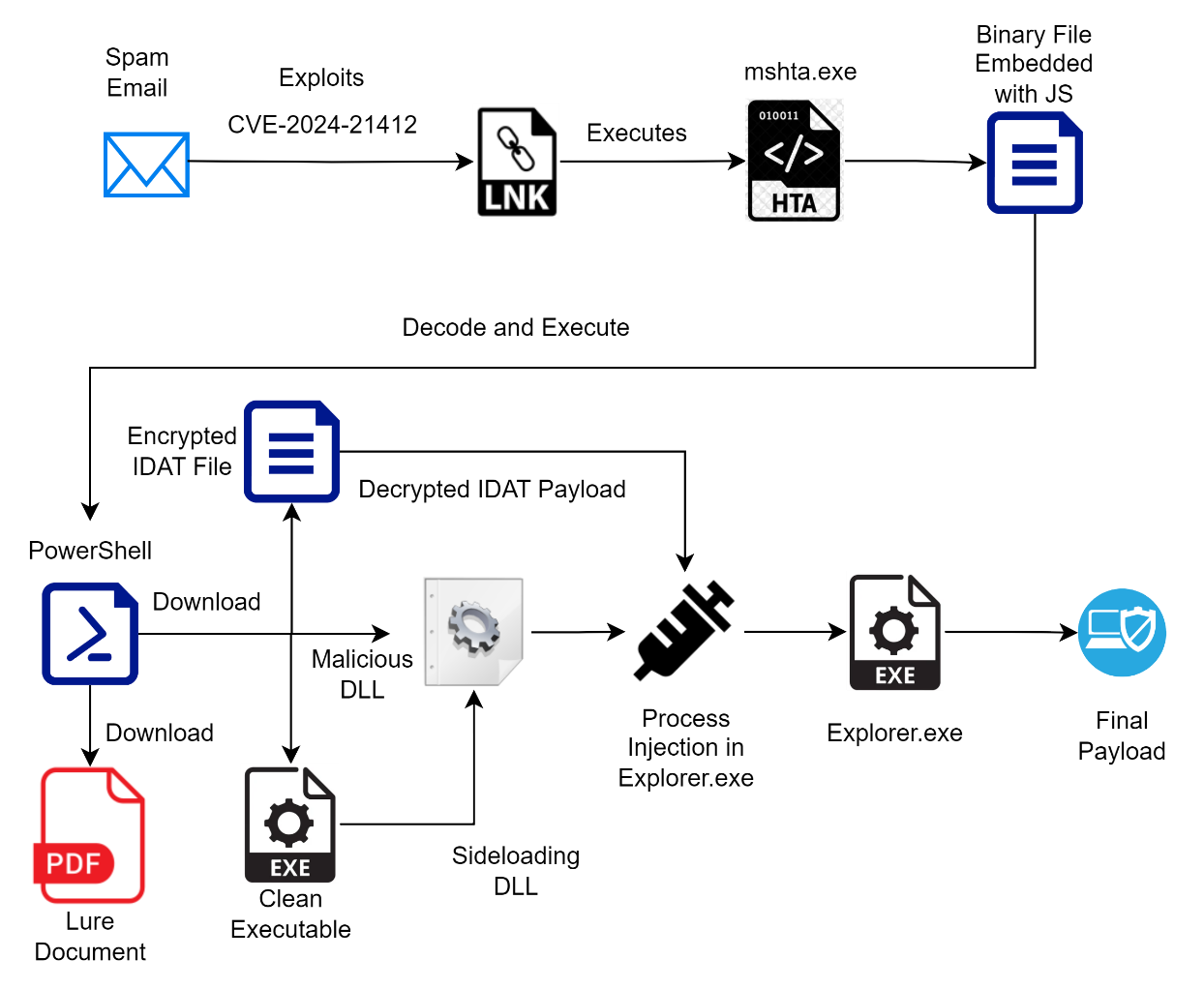
CRIL has uncovered an active campaign exploiting CVE-2024-21412. Attackers use spam emails that appear to come from trusted sources, enticing recipients to click on links that lead to internet shortcut files hosted on remote WebDAV shares. Upon interaction, these shortcuts exploit the vulnerability to execute malicious payloads, bypassing Microsoft Defender SmartScreen.

Overview of the Infection Chain | Image: CRIL
Infection Process
- Initial Spam Email: The attack begins with a spam email designed to appear legitimate, luring victims into clicking a link.
- Internet Shortcut File: The link directs users to a WebDAV share hosting a malicious internet shortcut (.url) file.
- Exploit Execution: When the user opens the .url file, it exploits CVE-2024-21412, triggering another LNK file on the same WebDAV share.
- Multi-Stage Attack: The LNK file executes a series of scripts, including PowerShell and JavaScript, to deploy final payloads like Lumma and Meduza Stealer.
This sophisticated attack sequence employs various legitimate Windows utilities and scripting techniques to evade detection and execute its malicious payload.
The attack leverages several key techniques:
- Forfiles Utility: Utilized to locate the “win.ini” file and execute a PowerShell command if found.
- MSHTA.exe: Used to run a malicious file (“dialer.exe”) containing embedded JavaScript.
- String.fromCharCode(): Employed to decode and execute additional PowerShell scripts.
- DLL Sideloading: The final stage involves launching a legitimate file that loads a malicious DLL, leading to the execution of the Lumma and Meduza Stealer.
The campaign targets a wide array of sectors and regions, including:
- Spanish Taxpayers: Using lure documents related to tax matters.
- Transportation Companies: Posing as the US Department of Transportation.
- Australian Individuals: Mimicking official Medicare enrollment forms.
The exploitation of the Microsoft SmartScreen vulnerability underscores the critical importance of proactive and comprehensive cybersecurity measures. As cybercriminals continue to refine their tactics and leverage new tools, individuals and organizations must remain informed, adaptable, and steadfast in their commitment to protecting sensitive data and digital assets.