
CrowdStrike, a leading cybersecurity firm, has issued a warning about a new information-stealing malware dubbed “Connecio” that’s being distributed by threat actors using a cunning disguise: a fake CrowdStrike Falcon sensor update. This malicious campaign, identified on July 23rd, 2024, exploits the recent disruption caused by a faulty Falcon sensor update on July 19th, which impacted Windows systems.
The threat actors are distributing a malicious ZIP file named “CrowdStrike Falcon.zip” that purports to be an official update. Once executed, the file unpacks a Python-based information stealer, Connecio. This malware is designed to harvest sensitive data from victim’s systems, including system information, IP addresses, and data from web browsers. The stolen information is then sent to the attackers’ command-and-control servers hosted on Pastebin, a popular code-sharing platform.
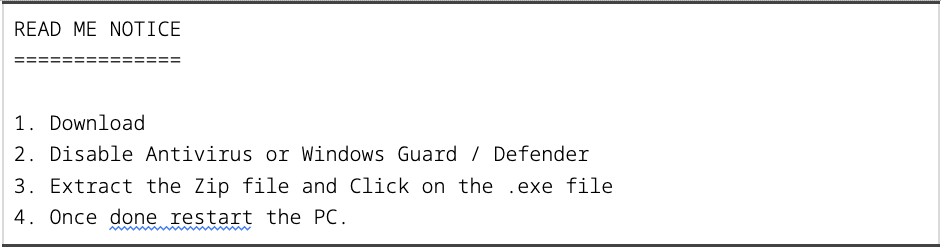
CrowdStrike’s technical analysis reveals that Connecio uses sophisticated techniques to evade detection and exfiltrate data. The malware includes instructions to disable Windows Defender, increasing its chances of success. It also employs Pastebin dead-drop URLs to dynamically obtain configuration information and a list of cryptocurrency addresses, likely for clipboard hijacking to steal digital currency.
To mitigate the risk of falling victim to this attack, CrowdStrike recommends the following:
- Accept updates only from official CrowdStrike channels. Be wary of unsolicited emails or downloads claiming to be updates.
- Educate users about the risks of executing files from untrusted sources. This includes files received via email or downloaded from unofficial websites.
- Verify website certificates before downloading software. This ensures that the software originates from a legitimate source.
- Enable browser download protection. Most browsers offer features that can warn users about potentially harmful downloads.
- Restrict network access to unknown servers and websites like Pastebin. This can help prevent malware from communicating with its command-and-control infrastructure.
Related Posts:
- Linux Users Hit by CrowdStrike Fallout: Kernel Panics Reported
- Report: 120,000 computers were infected with information-stealing malware
- Widespread Outage: CrowdStrike Update Affects 8.5 Million Windows Users
- CrowdStrike Outage: Microsoft Points Finger at EU Agreement
- CrowdStrike Global Threat Report: extortion and weaponization of data have become mainstream among cybercriminals