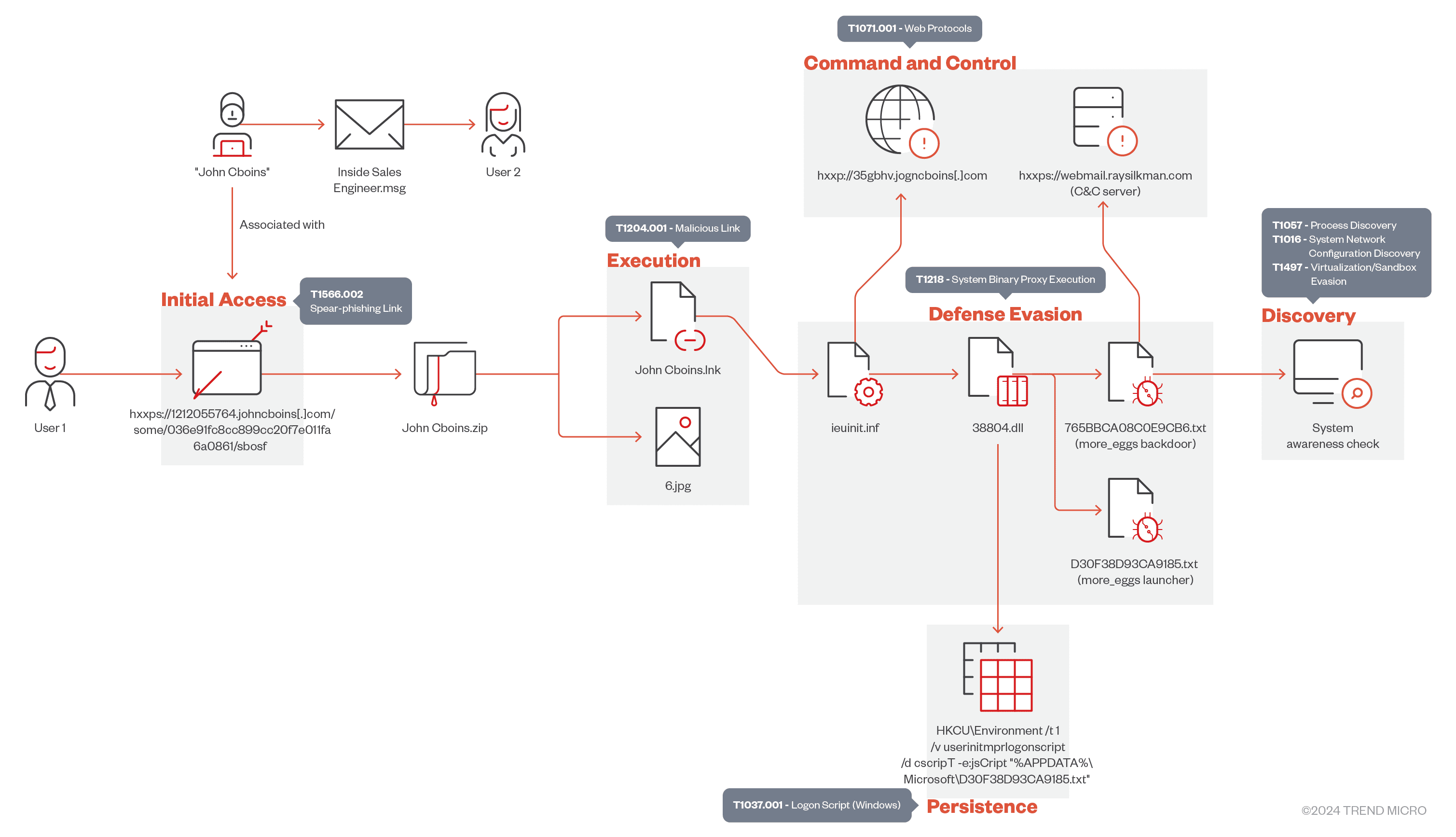
Infection diagram | Image: Trend Micro
Trend Micro researchers have uncovered a new phishing campaign targeting HR professionals. In this campaign, attackers send phishing emails disguised as job applicant inquiries, aiming to infiltrate large organizations’ networks and infect them with the More_eggs JavaScript backdoor.
This backdoor is sold as Malware-as-a-Service (MaaS) and grants cybercriminals access to sensitive information, such as banking credentials, email accounts, and administrator logins. The software is linked to the Golden Chickens group (also known as Venom Spider), which collaborates with other cybercrime groups like FIN6 (ITG08), Cobalt, and Evilnum.
Earlier, in June, eSentire uncovered a similar attack. In that instance, the attackers used LinkedIn to post fake resumes, which were in fact malicious shortcuts triggering the infection process.
The new version of the attack, identified by Trend Micro, differs in that the phishing email was specifically crafted to establish a trusted relationship. Notably, the attack targeted a recruiter at an engineering firm, who downloaded a résumé archived as “John Cboins.zip” from a suspicious site, “johncboins[.]com.”
This site offered a fraudulent résumé in the form of a ZIP archive containing an LNK file. Upon opening, it executed encrypted commands that launched a malicious DLL to deploy the More_eggs backdoor. The malware checks the user’s privilege level during execution and runs commands to collect system information before connecting to a command-and-control server for additional modules.
Researchers also discovered another variation of this campaign using PowerShell and Visual Basic Script to infect targets. Since More_eggs is sold as a service, identifying the exact perpetrator is challenging. However, the methods employed in the attack suggest possible ties to the FIN6 group.
The use of fake resumes as a means to infiltrate corporate networks necessitates heightened vigilance when handling files from unknown sources. Attackers are increasingly employing personalized approaches, making such attacks more effective and harder to detect.
Related Posts:
- eSentire Exposes Ongoing More_eggs Malware Campaign Targeting Job Seekers
- Tech Giants Vulnerable as Hackers Probe Kodex’s Defenses