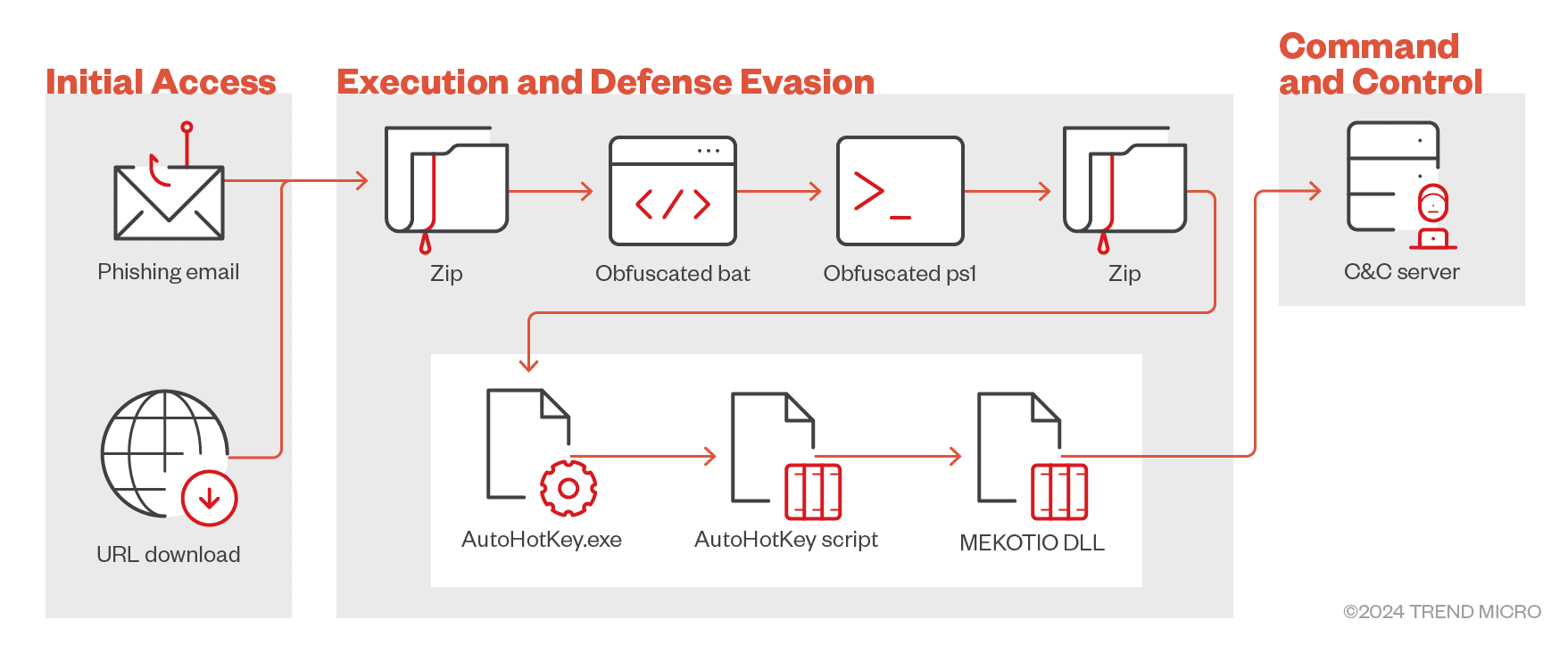
Mekotio’s observed infection chain | Image: Trend Micro
Phishing scams are rapidly evolving in Latin America, bringing back notorious banking Trojans like Mekotio, BBTok, and Grandoreiro. According to a recent report from Trend Micro, these cybercriminal campaigns have ramped up, using new and innovative phishing tactics that lure victims into downloading malware aimed at stealing sensitive banking credentials.
In recent months, cybercriminals have increasingly targeted Latin America with phishing campaigns designed to deploy banking Trojans. Mekotio, BBTok, and Grandoreiro—Trojans known for their financial fraud capabilities—are at the forefront of these operations. Traditionally, these Trojans focused on regions like Brazil and Argentina, but new intelligence suggests that their reach is expanding beyond the region.
The primary targets? Employees in industries like manufacturing, retail, and financial services. Manufacturing companies accounted for 26% of the attacks, followed by retail at 18%, technology at 16%, and financial services at 8%.
Cybercriminals are utilizing two main phishing lures to trick victims:
- Business transaction scams: Emails posing as official business communication trick users into clicking on malicious links or downloading harmful attachments, such as PDFs or ZIP files. Once downloaded, the Trojans infect the user’s device, enabling attackers to steal sensitive banking data or execute unauthorized transactions.
- Judicial-related phishing scams: This tactic preys on the fear of legal repercussions. Victims receive fake traffic violation emails that urge them to click on a link to resolve the issue. Clicking the link leads to a counterfeit website, where malware is surreptitiously downloaded onto the victim’s system.
By exploiting the urgency of financial and legal matters, cybercriminals bypass a user’s usual security precautions, leading to devastating consequences for the victims.
Originally discovered in 2018, Mekotio has primarily targeted Brazil and Spanish-speaking countries like Mexico, Chile, and Argentina. However, recent reports indicate that Mekotio is now broadening its geographical reach, with a new variant designed to evade detection in a wider range of locations, including parts of Southern Europe.
In its latest variant, Mekotio uses a more sophisticated PowerShell script to evade detection. When a victim clicks on a phishing link, a ZIP file is downloaded. This ZIP file contains an obfuscated batch file, which triggers a PowerShell script that acts as a second-stage downloader. The script performs reconnaissance checks to gather information about the compromised system, such as the public IP address, the user’s geographical location, and details about installed antivirus software.
Unlike previous versions, this new variant of Mekotio does not restrict its actions based on the country of the compromised system, suggesting that cybercriminals are looking to expand their attack base globally. Once the reconnaissance phase is complete, the malware downloads a final ZIP file containing the payload, which is then executed on the victim’s machine, allowing the malware to persistently steal financial data.
First detected in 2020, BBTok focuses on the Latin American financial sector and employs highly advanced techniques for credential theft and data exfiltration. In recent campaigns, BBTok has started abusing legitimate Windows utility commands to evade detection.
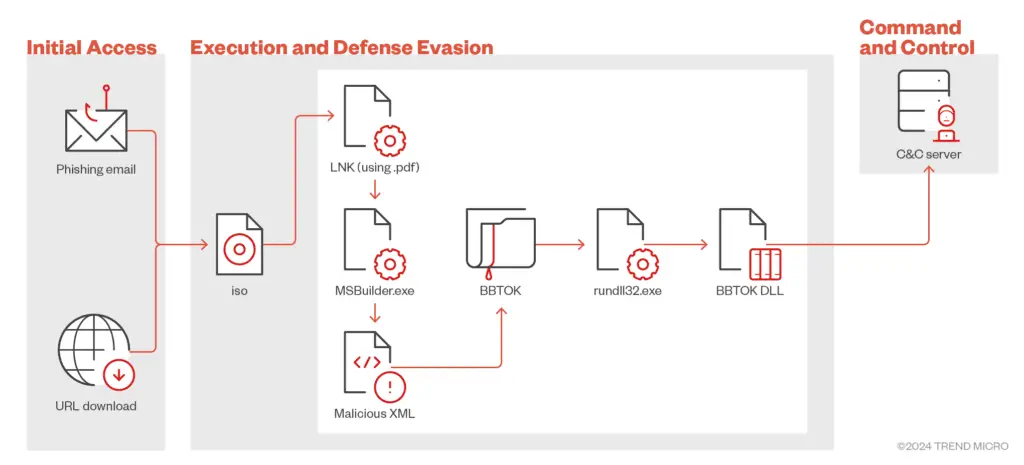
When a victim clicks on a malicious link in a phishing email, an ISO file is downloaded, which contains malicious components including LNK files that initiate the infection chain. The Trojan cleverly uses MSBuild.exe, a legitimate Windows tool, to load its malicious payload from an XML file. By using trusted Windows utilities, BBTok can execute its attack without triggering antivirus alarms.
Once the infection process begins, the Trojan connects to the attacker’s command-and-control server, allowing the attacker to control the compromised system, exfiltrate data, and initiate further stages of the attack. This makes BBTok one of the most formidable threats in the region.
The resurgence of banking Trojans like Mekotio, BBTok, and Grandoreiro highlights the growing sophistication of phishing attacks in Latin America. As these campaigns evolve, the need for robust cybersecurity defenses becomes ever more critical.
Related Posts:
- Mekotio Banking Trojan Resurges, Targeting Latin American Financial Systems
- Mekotio Trojan: A PowerShell-Based Threat Targeting Victims with Stealth and Persistence
- Brazilian Banking Malware Targets Spain: An Emerging Cyber Threat Landscape
- Threat Actors Weaponize Google Cloud Run for Global Payload Delivery