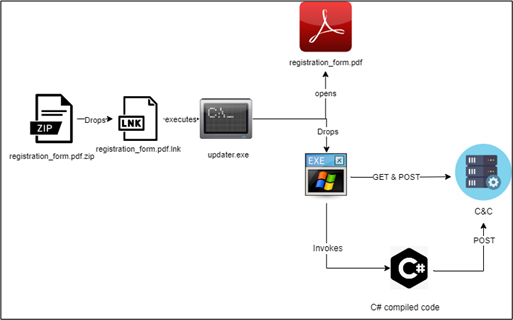
Infection chain | Image: CRIL
In a concerning development, Cyble Research and Intelligence Labs (CRIL) has uncovered a sophisticated cyberattack aimed at individuals associated with the upcoming US-Taiwan Defense Industry Conference. This stealthy campaign employs a fileless malware strain that leverages social engineering and advanced in-memory execution techniques to evade detection.
The attack begins with a malicious archive file sent to potential victims via email, likely as part of a larger phishing campaign. The archive, named “registration_form.pdf.zip,” contains an LNK file disguised as a PDF document, tricking users into believing they are interacting with a harmless registration form. Once opened, this LNK file triggers a series of covert actions that deploy the attack without leaving typical traces on the system’s disk.
The LNK file extracts two key components: a legitimate-looking PDF to further deceive the user and a base64-encoded executable, both designed to run in the background. This executable, protected by .NET’s Confuser tool to evade detection, is then placed in the system’s startup folder to ensure persistence. Upon execution, it retrieves additional malicious content, including a DLL file encrypted with XOR to obscure its true purpose.
What sets this attack apart is its fileless nature. Instead of writing malicious code to the disk—where it might be caught by traditional antivirus tools—the malware uses the .NET “Assembly.Load” function to load the decrypted DLL directly into memory. This method allows the attackers to bypass many of the security mechanisms that scan files stored on disk, making the attack much harder to detect.
The ultimate goal of this campaign appears to be the exfiltration of sensitive information. After deploying the DLL, the malware downloads encrypted C# code from the attacker’s server, compiles it in memory, and executes it without leaving a trace on the hard drive. The compiled code interacts with Windows Management Instrumentation (WMI) to gather system information and may also allow the attackers to access confidential files, network configurations, and more.
Data exfiltration is performed using a web-based method that mimics normal traffic. The stolen data is uploaded via a POST request to the attacker’s server, hidden under seemingly benign headers and simulating standard form data submission. This clever technique ensures that the data is siphoned off quietly, without raising alarms in the victim’s network monitoring systems.
Based on the contents of the lure document and the context of the attack, CRIL has reason to believe that the attackers are specifically targeting individuals connected to the US-Taiwan Defense Industry Conference, scheduled for September 22-24, 2024. This event is expected to gather key defense officials, government representatives, industry executives, and other stakeholders involved in US-Taiwan defense collaborations.
The timing and sophistication of this attack suggest that the attackers are aiming to exploit the event for espionage purposes, potentially seeking to steal sensitive defense-related information or disrupt discussions surrounding US-Taiwan military cooperation.
While the specific threat actors behind this campaign have not yet been identified, CRIL notes that Chinese threat actors have a history of targeting Taiwan during significant political or defense-related events. However, the tactics, techniques, and procedures (TTPs) observed in this campaign have not been conclusively linked to any known advanced persistent threat (APT) group.