CSIRT-Collect
A PowerShell script to collect memory and (triage) disk forensics for incident response investigations.
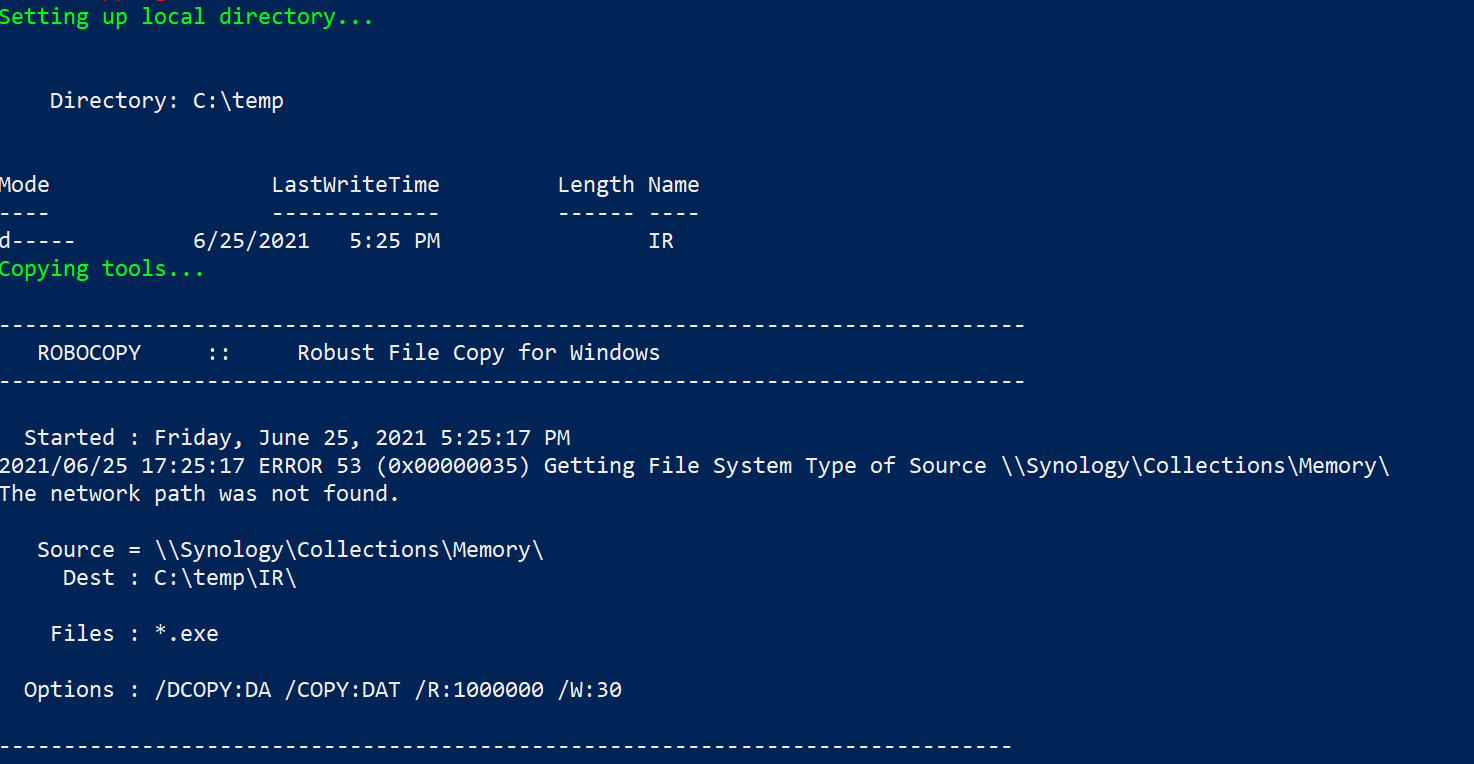
The script leverages a network share, from which it will access and copy the required executables and subsequently upload the acquired evidence to the same share post-collection.
Permission requirements for the said directory will be dependent on the nuances of the environment and what credentials are used for the script execution (interactive vs. automation)
In the demonstration code, a network location of \Synology\Collections can be seen. This should be changed to reflect the specifics of your environment.
The collections folder needs to include:
- subdirectory KAPE; copy the directory from the existing install
- subdirectory MEMORY; 7za.exe command line version of 7zip and winpmem.exe
CSIRT-Collect
- Maps to an existing network drive –
-
- Subdir 1: “Memory” – Winpmem and 7zip executables
-
- Subdir 2: ”KAPE” – directory (copied from the local install)
- Creates a local directory on asset
- Copies the Memory exe files to the local directory
- Captures memory with Winpmem
- When complete, ZIPs the memory image
- Renames the zip file based on hostname
- Documents the OS Build Info (no need to determine the profile for Volatility)
- Compressed image is copied to network directory and deleted from the host after transfer complete
- New temp Directory on the asset for KAPE output
- KAPE !SANS_Triage collection is run using VHDX as output format [$hostname.vhdx]
- VHDX transfers to network
- Removes the local KAPE directory after completion
- Writes a “Process complete” text file to network to signal investigators that collection is ready for analysis.
CSIRT-Collect_USB
Essentially the same functionality as CSIRT-Collect.ps1 with the exception that it is intended to be run from a USB device. The extra compression operations on the memory image and KAPE .vhdx have been removed. There is a slight change to the folder structure for the USB version. On the root of the USB:
- CSIRT-Collect_USB.ps1
- folder (empty to start) titled ‘Collections’
- folders for KAPE and Memory – same as above
Changelog v5.0
- Functions:
🐏 Capture a memory image with MAGNET DumpIt for Windows, (x32, x64, ARM64), or MAGNET RAM Capture on legacy systems;
💻 Create a Triage collection* with MAGNET Response;
🔐 Check for encrypted disks with Encrypted Disk Detector;
🔑 Recover the active BitLocker Recovery key;
💾 Save all artifacts, output, and audit logs to USB or source network drive.
Download
git clone https://github.com/dwmetz/CyberPipe.git
Use
Copyright (c) 2021 Doug Metz
Source: https://github.com/dwmetz/