
Image: Sentinelone
The pro-Russian hacktivist collective CyberVolk, also known as GLORIAMIST, has emerged as a significant threat in a rapidly evolving cybercrime ecosystem. A recent report by SentinelOne delves into the group’s activities, tools, and alliances, painting a complex picture of a group using advanced cyber capabilities to align with Russian geopolitical interests.
CyberVolk’s roots trace back to India, with its current form emerging in May 2024. Initially known by names such as GLORIAMIST India and Solntsevskaya Bratva, the group shifted to ransomware-as-a-service (RaaS) operations in June 2024. SentinelOne describes CyberVolk as “a politically motivated hacktivist collective… The group uses both DDoS and ransomware attacks in its efforts to undermine and disrupt the operations of those opposed to Russian interests.”
CyberVolk has adopted and modified existing malware to suit its purposes, using ransomware like DoubleFace, HexaLocker, and Parano. The group’s branded ransomware, developed by a prominent member known as @ghostdoor_maldev, is built on the AzzaSec codebase. Early iterations employed AES encryption, but recent versions have integrated “ChaCha20-Poly1305 + AES + RSA + Quantum resistant algorithms,” making detection and mitigation increasingly challenging.
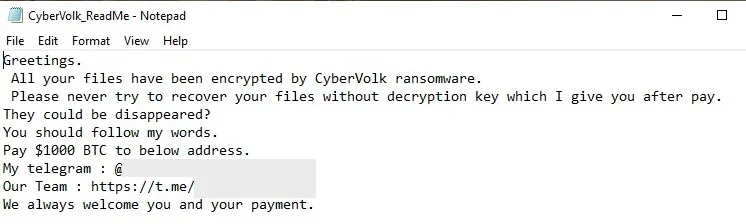
One of the more concerning aspects of CyberVolk ransomware is its use of advanced tactics, such as terminating key processes like Task Manager and MMC and setting tight deadlines for ransom payments. “CyberVolk ransomware supports BTC and USDT payments,” notes SentinelOne, with ransom demands typically set at $1,000 and a decryption timer of five hours.
The group’s activities are not limited to ransomware attacks. CyberVolk has launched targeted campaigns such as #OpJP, which focused on Japanese entities including the Japan Foundation and the Japan Meteorological Agency. These campaigns reflect the group’s alignment with Russia’s strategic interests in the Asia-Pacific region.
CyberVolk has also established alliances with various hacktivist groups, including NONAME057(16) and LAPSUS$. However, internal tensions and infighting frequently lead to fragmentation and reshaping of the threat landscape. The report highlights that “infighting, threats, and inflated political posturing are common, leading to fragmentation and the rapid reshaping of the hacktivist threat landscape.”
Beyond ransomware, CyberVolk distributes infostealers and webshells. The recently announced “CyberVolk Stealer” is based on the LBX-Grabber code and targets sensitive data such as browser credentials, Discord accounts, and cryptocurrency wallets. Additionally, their PHP-based webshell provides attackers with powerful capabilities, including file manipulation and directory traversal.
CyberVolk’s ability to rapidly adapt its tools and tactics underscores the challenges faced by cybersecurity defenders. SentinelOne emphasizes that “as groups like CyberVolk leverage openly-available commodity tools with high potential for causing damage, they continue to add more layers of complexity.”
Related Posts:
- CyberVolk: From Hacktivism to Ransomware – Researcher Exposes New Threat
- CyberVolk Ransomware: A New and Evolving Threat to Global Cybersecurity
- SentinelOne Unveils: The Hidden Dangers of npm in Business Security
- BlueNoroff’s New MacOS Threat: “Hidden Risk” Targets Crypto Enthusiasts
- Dark Angels vs. RagnarLocker: SentinelOne Decodes the 2023 Ransomware Attack