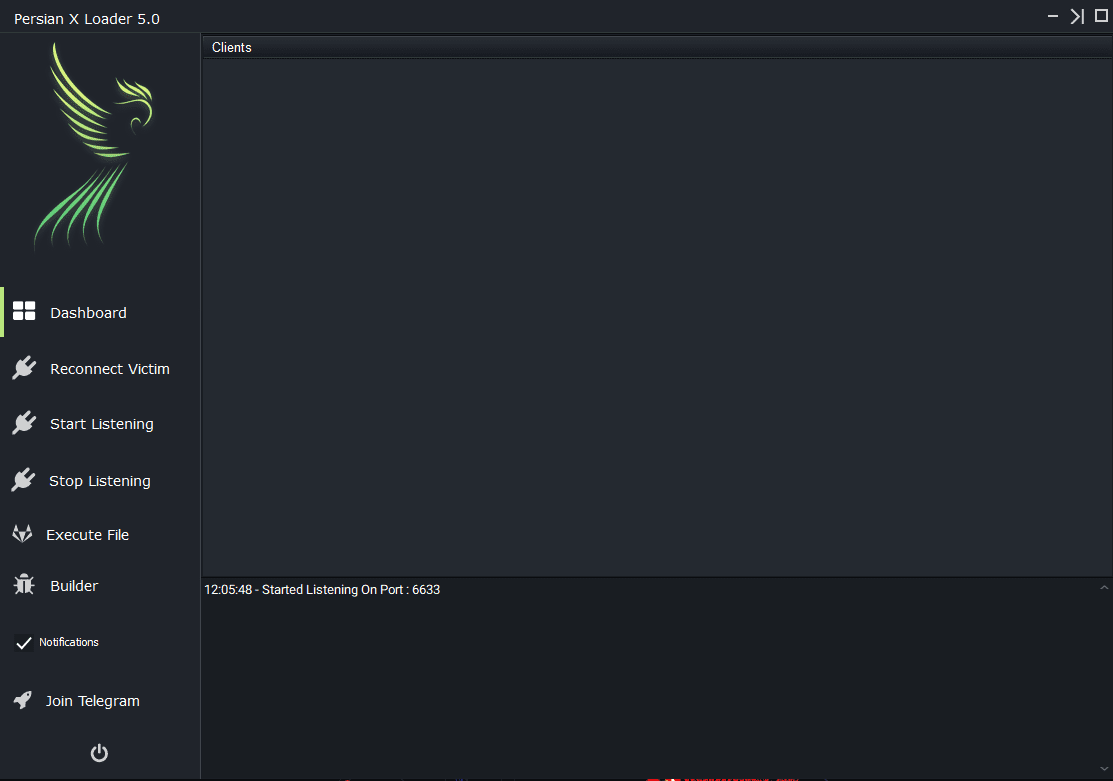
Persian X Loader 5.0 Builder Panel | Image: Cyble Research and Intelligence Labs
In a recent breakthrough, Cyble Research and Intelligence Labs (CRIL) has uncovered a website named Persian Remote World, a hub for various malicious tools, including the newly identified Persian Loader. This discovery has set off alarms across cybersecurity circles, highlighting the evolving landscape of cyber threats.
Persian Remote World stands out as a digital bazaar for illicit software, offering a range of harmful tools like Remote Access Trojans (RATs), loaders, and crypters. Despite thorough investigations, no active campaigns utilizing these tools have been detected in the wild yet.

The Persian Loader, a prominent offering on this site, boasts both a builder and a client management panel. It’s designed to ensnare victims, providing functionalities to execute files on compromised systems. This loader is sold under a monthly subscription model for $20.
Alongside the loader, the website markets a Persian RAT, complete with a panel to construct the RAT binary and control infected systems. This tool is available from a one-month subscription at $20 to a lifetime option for $200. Moreover, the Persian Security crypter, the priciest tool, aims to encrypt and obfuscate executables, ranging from $45 per month to $650 for a lifetime subscription.
The Persian RAT, a sample found on VirusTotal, demonstrates a complex structure. With a relatively large file size of 3.75 MB, it establishes a mutex named “Persian” to prevent multiple instances and enable coordination in multithreading operations.
The RAT activates critical privileges like SeShutdownPrivilege and SeDebugPrivilege, allowing it to reboot systems and modify other processes’ memory. This manual control RAT waits for command-and-control (C&C) instructions to launch its malicious activities.
1. Firewall Manipulation: The RAT can enable or disable the system firewall using netsh commands, providing a pathway for further malicious activities.
2. Keylogging and Cookie Theft: It has routines for capturing keystrokes and stealing cookies from popular browsers like Firefox, Chrome, and Edge.
3. Targeting Games and Applications: Persian RAT scans and exfiltrates files from various games and applications, ranging from Spotify to gaming giants like Fortnite and League of Legends.
4. Embedded Commands: The RAT contains embedded commands for a range of operations including disabling user account control, ransomware functions, and screen capture capabilities.
Persian Loader plays a crucial role in executing second-stage payloads. Its builder, Persian X Loader 5.0, creates a custom listener server to act as a server for the loaders. This server can execute files on infected systems and manage deployed loaders, highlighting its versatility in cyberattacks.
The emergence of Persian Remote World and its suite of malicious tools like Persian Loader and RATs underscores a significant threat in the cybersecurity landscape. These tools enable threat actors to execute commands remotely, steal sensitive data, and manipulate system settings, posing risks to user privacy and financial security. The sophistication and persistence of such RATs call for heightened awareness and robust cybersecurity measures to safeguard against these evolving cyber threats.