dalton v3.2.4 releases: Suricata & Snort IDS rule and pcap testing system
Dalton is a system that allows a user to quickly and easily run network packet captures (“pcaps”) against an intrusion detection system (“IDS”) sensor of his choice (e.g. Snort, Suricata) using defined rulesets and/or bespoke rules. It also includes a wizard-like web interface for Flowsynth to facilitate custom pcap creation.
Use Cases
These are the most common use cases for Dalton:
-
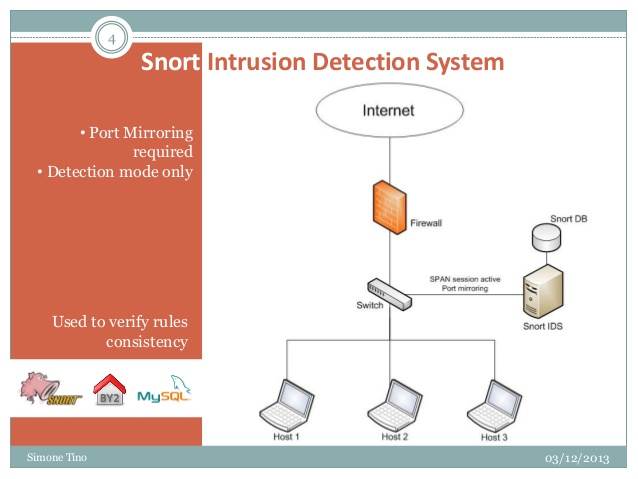
Testing Rulesets/Ruleset CoverageUser-provided pcaps can be run thru an IDS engine loaded with a particular ruleset.
-
Troubleshooting and Developing SignaturesUser-provided pcaps can be tested against user-provided ad hoc IDS rules to quickly and easily see the IDS alerts and/or test for rule syntax errors.
-
Testing Variable ChangesThe ruleset variables used by the engine can easily be modified for submitted jobs; this can be used to determine the impact that a variable change may have on a specific detection.
-
Testing Configuration ChangesCustomized engine configuration files can include with submitted jobs; this can be used to determine the impact that an engine configuration change may have on a specific detection.
-
Testing specific IDS engine behaviorIt supports the ability to apply the above use cases on specific sensors. The Dalton architecture is designed to accommodate and support sundry sensor engines and engine versions.
-
Crafting custom packet capturesAs part of the Web interface, it has a module that provides a wizard-like web interface for Flowsynth. This allows for quick and easy network flow definition and pcap creation for popular protocols and traffic patterns.
It consists of a “controller” (dalton.py) and “agents” (dalton-agent.py). The controller provides a web interface as well as an HTTP API for agent communication and programmatic job results retrieval. From a web interface, a user submits a job to be run on a particular agent or agent platform. A Dalton job consists of one or more pcaps, a pre-defined ruleset and/or custom rules, agent engine configuration options (e.g. configuration to apply to Suricata when running a job), and a manifest file specifying other options for the job (e.g. return rule performance logs).
The Dalton Agent code (dalton-agent.py) runs on an IDS sensor and provides an interface between the Dalton controller and an IDS engine. Dalton agents grab pending jobs from the Dalton controller, run them locally, and report the results back. These results are then displayed in the web GUI provided by the Dalton controller. Jobs are submitted to specific sensor engines (e.g. Suricata) and versions (e.g. 4.0.0).
Code for the Dalton agent and controller webapp are written in Python and leverage Flask and Jinja2. On the Dalton controller, Redis is used to manage the job queue, store results, and maintain a list of active Dalton agents.
The Dalton controller includes a Flowsynth WebUI module that provides a user interface to assist with rapid Flowsynth language prototyping and development of network flow definitions that are then compiled into network pcaps by the Flowsynth script. This is basically a GUI to facilitate input and output to Flowsynth. There is the option to easily send Flowsynth WebUI-generated pcaps to Dalton for testing.
While all the above systems could be independent physical (or virtual) machines (and in fact, this setup has been done), for ease of install and use, everything has also been architected as a group of Docker containers. The Dalton codebase includes Dockerfiles, “docker-compose.yaml”, and associated configuration files to facilitate easy application launch using a set of Docker containers.
Changelog v3.2.4
- New URL for downloading Suricata source code





