
The Dark Angels Ransomware Group has emerged as one of the most sophisticated and stealthy ransomware groups in recent years, focusing on highly targeted attacks against large enterprises. According to a detailed analysis by Zscaler’s ThreatLabz, Dark Angels has been operating quietly since April 2022, and despite their low-profile approach, the group has made headlines with a record-breaking ransom payment of $75 million in 2024, the largest known ransom in history.
Unlike many ransomware groups that rely on third-party initial access brokers, Dark Angels conducts their own operations, allowing them to target specific organizations with precision. This highly selective approach enables the group to avoid mass attention while still demanding substantial ransoms. Zscaler’s analysis notes: “Dark Angels attempt to remain in the shadows by performing attacks that do not cause significant business disruptions.”
This tactic not only minimizes the chances of detection but also gives the group more control over their operations. Rather than crippling entire organizations with file encryption, Dark Angels frequently focus on data exfiltration, stealing vast amounts of sensitive information and using it as leverage to demand payments in exchange for not leaking the stolen data.
Dark Angels initially used ransomware payloads based on the Babuk source code, one of the most widely used ransomware families. However, by 2023, they transitioned to leveraging RTM Locker for encrypting Windows systems and RagnarLocker for attacking Linux and VMware ESXi systems. RTM Locker, which itself is based on Babuk, includes modifications like using ChaCha20 instead of HC-128 for encryption, enhancing its ability to securely encrypt files.
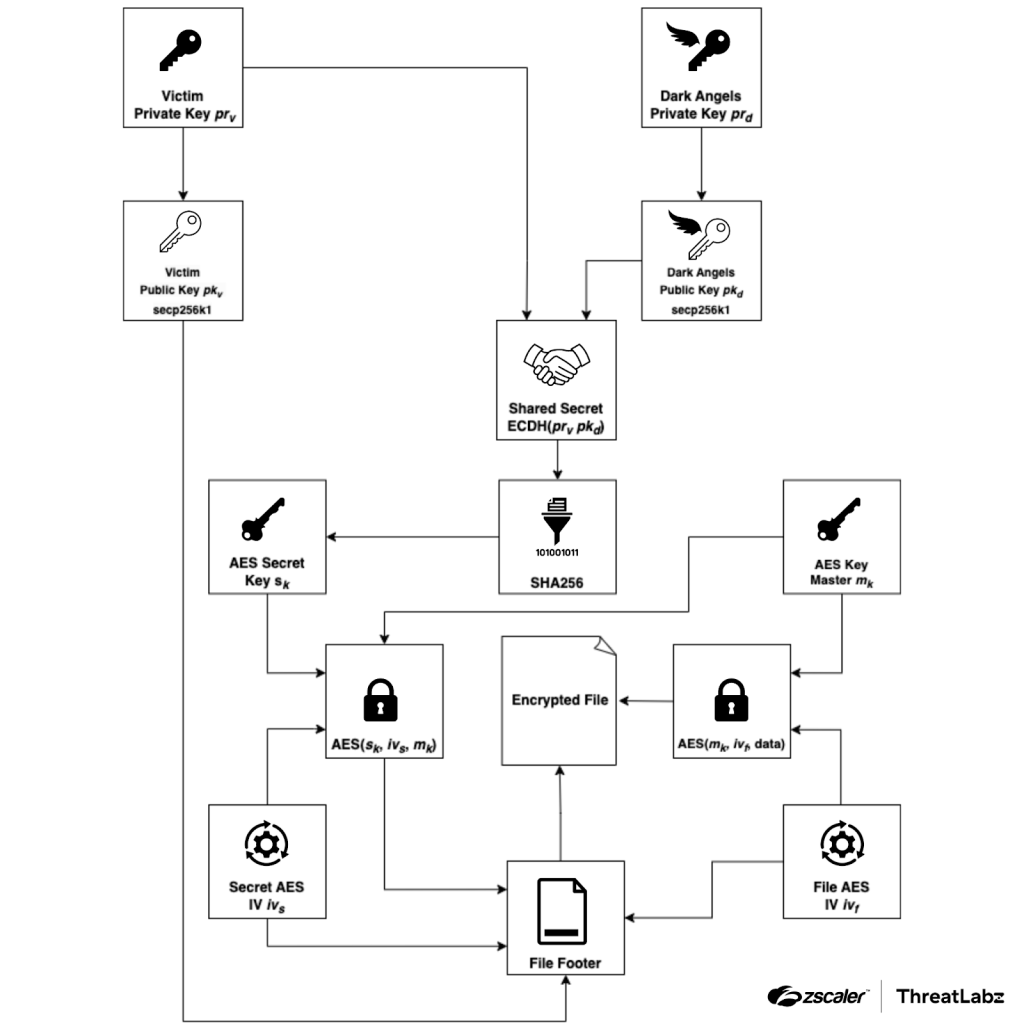
The group’s file encryption techniques demonstrate their technical sophistication. For example, the RTM Locker variant uses Elliptic Curve Cryptography (ECC) with Curve25519 to perform key exchanges, ensuring robust encryption. However, one notable flaw in their implementation arises if the encryption process is interrupted, which can prevent decryption of certain files.
For Linux and ESXi systems, Dark Angels uses a RagnarLocker variant that employs ECC with secp256k1 and 256-bit AES in CBC mode for encryption. This highly efficient encryption method allows the group to optimize file encryption for large files, enabling faster encryption processes that reduce the risk of being detected mid-attack.
Dark Angels’ ability to remain under the radar while extorting massive ransom payments sets them apart from other ransomware groups. Their strategy focuses on targeting large enterprise organizations and making calculated decisions about whether to deploy ransomware based on the potential disruptive impact of file encryption. “The group selectively chooses whether to deploy ransomware based on how much impact file encryption will have on the targeted organization.”
In some cases, the group opts to steal data without encrypting files, demanding a ransom purely to prevent the release of sensitive information. This dual-extortion model has allowed them to remain effective while avoiding the massive operational disruptions that often trigger media and law enforcement attention.
In January 2023, Dark Angels began releasing stolen data through a Telegram channel named @leaksdirectory, marking a shift toward more public-facing operations. By April 2023, they launched their own data leak site, Dunghill Leak, hosted as a Tor hidden service. On this site, the group ironically markets itself as offering “professional information security services,” framing its extortion activities as a way to make the world more secure.
Related Posts:
- Dark Angels Ransomware Gang Reaps Record $75 Million Payout
- Dark Angels vs. RagnarLocker: SentinelOne Decodes the 2023 Ransomware Attack