DarkFinger-C2: Windows TCPIP Finger Command / C2 Channel and Bypassing Security Software
DarkFinger-C2
Windows TCPIP Finger Command / C2 Channel and Bypassing Security Software.
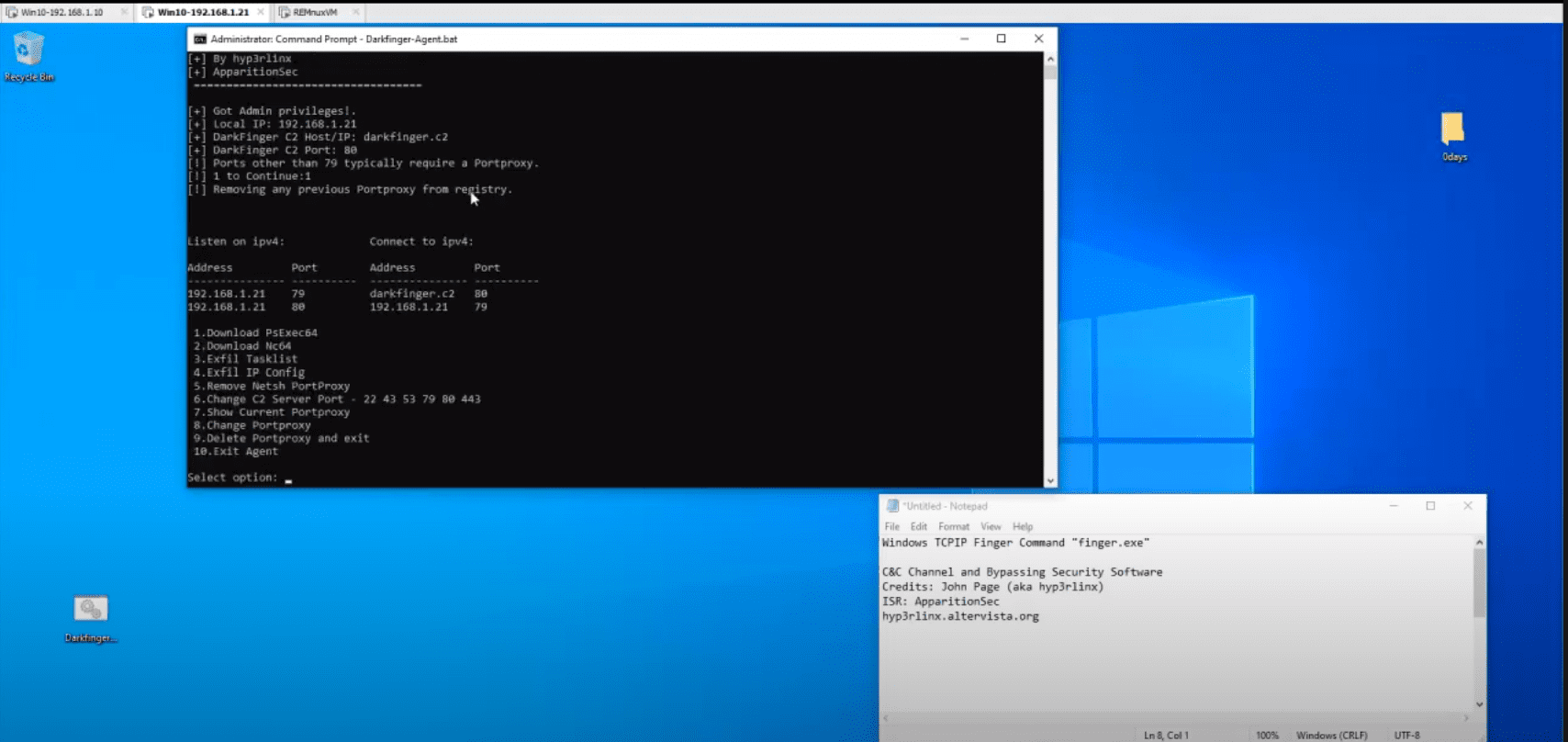
Microsoft Windows TCPIP Finger Command “finger.exe” that ships with the OS can be used as a file downloader and makeshift C2 channel. The legitimate use of Windows Finger Command is to send Finger Protocol queries to remote Finger daemons to retrieve user information. However, the finger client can also save the remote server response to disk using the command line redirection operator “>”.
Intruders who compromise a computer may find it is locked down and “unknown” applications may be unable to download programs or tools. By using built-in native Windows programs, it’s possible they may be whitelisted by installed security programs and allowed to download files.
Red teams and such using LOL methods have made use of “Certutil.exe”, a native Windows program for downloading files. However, Certutil.exe is recently blocked by Windows Defender Antivirus and logged as event “Trojan:Win32/Ceprolad.A” when it encounters http/https://.
Therefore, using Windows finger we can bypass current Windows Defender security restrictions to download tools, send commands, and exfil data. The Finger protocol as a C2 channel part works by abusing the “user” token of the FINGER Query protocol “user@host”. C2 commands masked as finger queries can download files and or exfil data without Windows Defender interference.
Download
git clone https://github.com/hyp3rlinx/DarkFinger-C2
Use
Demo
Copyright (c) 2020 John Page (aka hyp3rlinx)