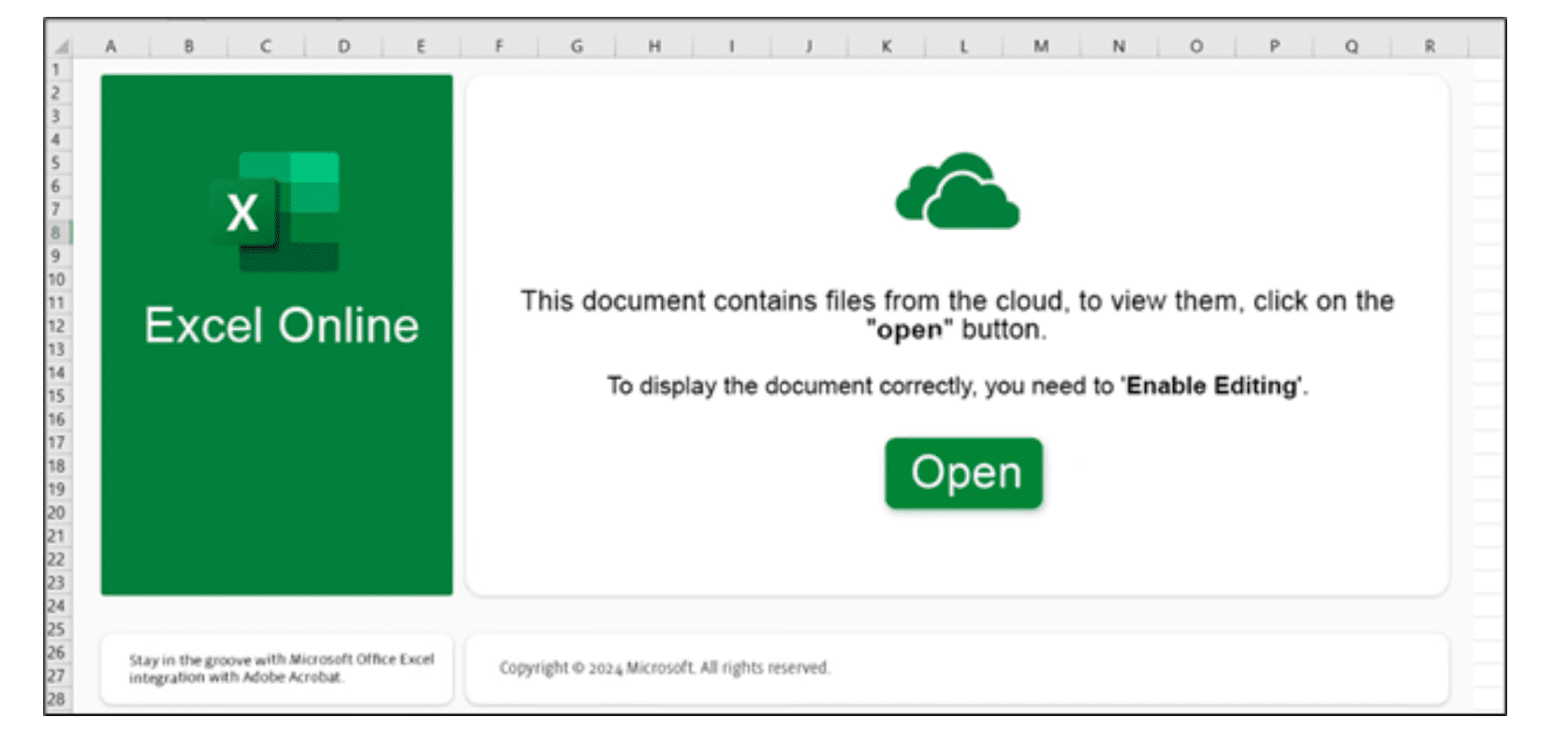
Template used by .xlsx files used in this DarkGate campaign | Image: Unit 42
The notorious DarkGate malware, once dormant after the Qakbot takedown, has reemerged, leveraging a clever combination of Microsoft Excel files and public Samba shares to distribute its malicious payload. This sophisticated campaign, as revealed in a recent report by the Unit 42 Incident Response team, has targeted unsuspecting users across North America, Europe, and Asia.
The attackers employ deceptive Excel files with seemingly official names, often using nomenclature like “paper<NUM>-<DD>-march-2024.xlsx” or “ACH-<NUM>-<DD>March.xlsx,” to lure victims into opening them. Upon doing so, the malicious files initiate a chain of events that ultimately lead to the download and execution of the DarkGate malware package.
The attack chain begins with the retrieval and execution of code from publicly accessible Samba shares. This code, hidden within VBS or JS files, then downloads and runs a PowerShell script, which ultimately installs the AutoHotKey-based DarkGate malware on the victim’s system.
DarkGate itself is a highly advanced malware with a range of anti-analysis features designed to evade detection. These features include checks for CPU information, the presence of anti-malware programs, and virtual environments. The malware also decrypts its configuration data based on gathered information, making it even harder to detect and analyze.
The attackers have even employed evasion techniques to bypass security software like Kaspersky. The use of public Samba shares as a distribution mechanism adds another layer of complexity to the attack, making it more difficult to trace and mitigate.
DarkGate communicates with its command and control (C2) servers via unencrypted HTTP requests, using Base64-encoded and further obfuscated data. This technique helps mask the nature of the data being exfiltrated, complicating detection efforts.
The resurgence of DarkGate and its evolving attack techniques pose a significant threat to individuals and organizations alike. Users are strongly urged to exercise caution when opening email attachments, even those that appear to be from trusted sources. It’s also crucial to keep security software updated and to be vigilant for any suspicious activity on their systems.
Organizations should review and strengthen their security measures to protect against these advanced threats. This includes implementing robust email filtering solutions, monitoring network traffic for unusual activity, and educating employees about the dangers of phishing and social engineering attacks.