
DarkGate infection chain abusing Skype.
In a recent revelation by security researchers at Trend Micro, the notorious DarkGate malware campaign, dormant for a few years, has resurfaced with a renewed threat matrix. From July to September, the campaign exploited instant messaging platforms to disperse its malicious payload to unsuspecting victims. Trend Micro provides an overview of the new tactics deployed by DarkGate, the geography of its recent attacks, and its potential implications.
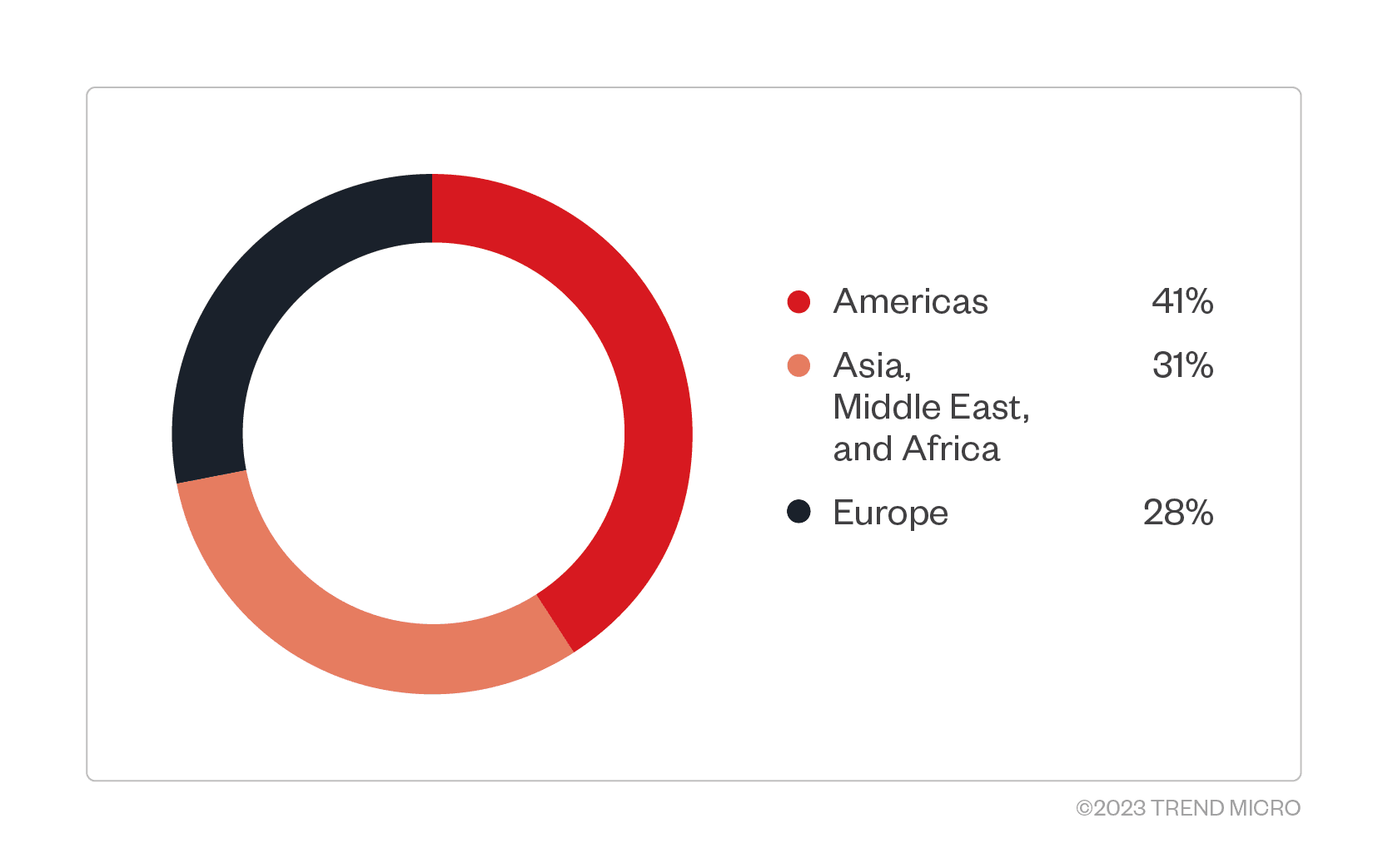
Previously inactive for some time, DarkGate has seen a resurgence, especially targeting the Americas, followed by Asia, the Middle East, and Africa. This malware, first identified in 2017 and recently advertised on the Russian forum eCrime since May 2023, acts primarily as a loader. Its capabilities span a wide range, including:
- Executing discovery commands
- Self-updating and management
- Implementing remote access software
- Cryptocurrency mining
- Keylogging
- Information theft from browsers
- Privilege escalation
What makes DarkGate particularly challenging to deal with is its use of AutoIt, a legitimate Windows-specific automation tool. Historically, mainstream loaders such as IcedID and Emotet haven’t used it, allowing security teams to easily link it to the DarkGate campaign.

Researchers noted that the malware employs deceptive techniques by abusing the trust between organizations. For instance, by accessing the victim’s Skype account, the attacker mimics an ongoing messaging thread and sends a deceptive VBS script. This script, masked as a PDF with the filename “<filename.pdf> www.skype[.]vbs”, tricks the user into executing it, thinking it’s a harmless document.
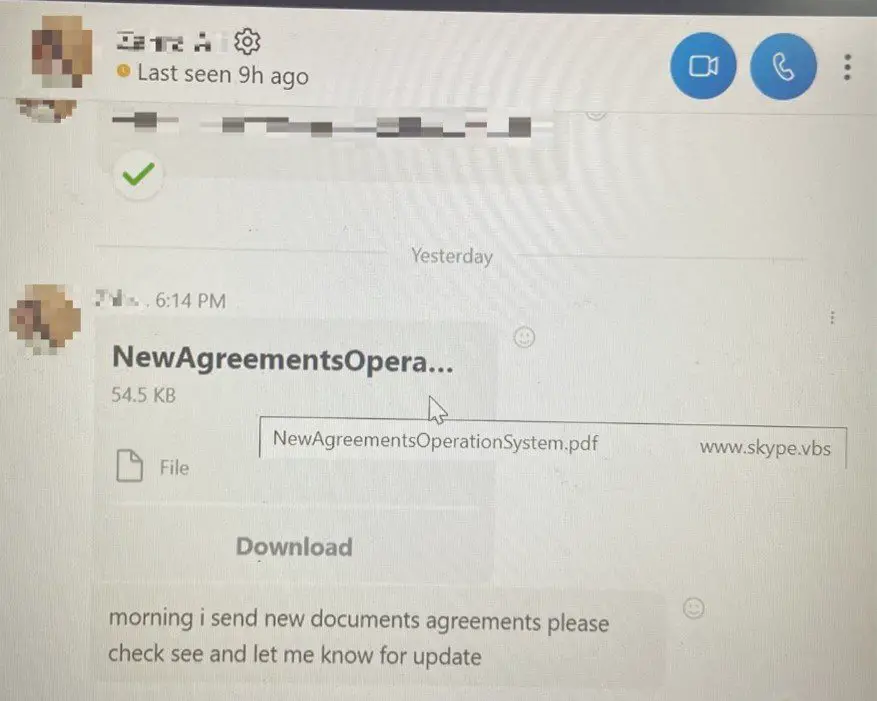
Once executed, the VBA script initiates a series of actions, creating a directory, downloading an AutoIt3 executable, and preparing the ground for the DarkGate malware.
Researchers observed another attack method via Microsoft Teams. The attacker sends a deceptive link in a message from an external source, sometimes posing as a PDF document, effectively tricking the user. A similar technique was also documented using SharePoint, where victims are led to download malicious files under the pretense of company changes or transformations.
The DarkGate script has a structured execution sequence. Before it loads, it checks for specific conditions such as the existence of the %Program Files%, and ensures the username isn’t “SYSTEM”. It then searches for the “.au3” extension to decrypt and executes the DarkGate payload.
Upon execution, the malware employs surrogate processes like iexplore.exe and GoogleUpdateBroker.exe and injects them with malicious code. It secures its persistence by randomly placing an LNK file in the Windows User Startup folder, ensuring the malware activates at every system startup. For further probing into DarkGate’s activities, tools provided by Telekom Security can be useful.
After a successful installation, DarkGate acts as a downloader for additional payloads. It discreetly places files in directories such as <C:/Intel/> and <%appdata%/Adobe/>, further masquerading its activities. Some detected files associated with this malware include “Folkevognsrugbrd.exe” and “Vaabenstyringssystem.exe”.
The resurgence of DarkGate underscores the evolving nature of cyber threats. While cybersecurity researchers continue to monitor and combat these threats, it is crucial for organizations and individuals to remain vigilant, ensuring that they are equipped with the latest cybersecurity tools and practices.