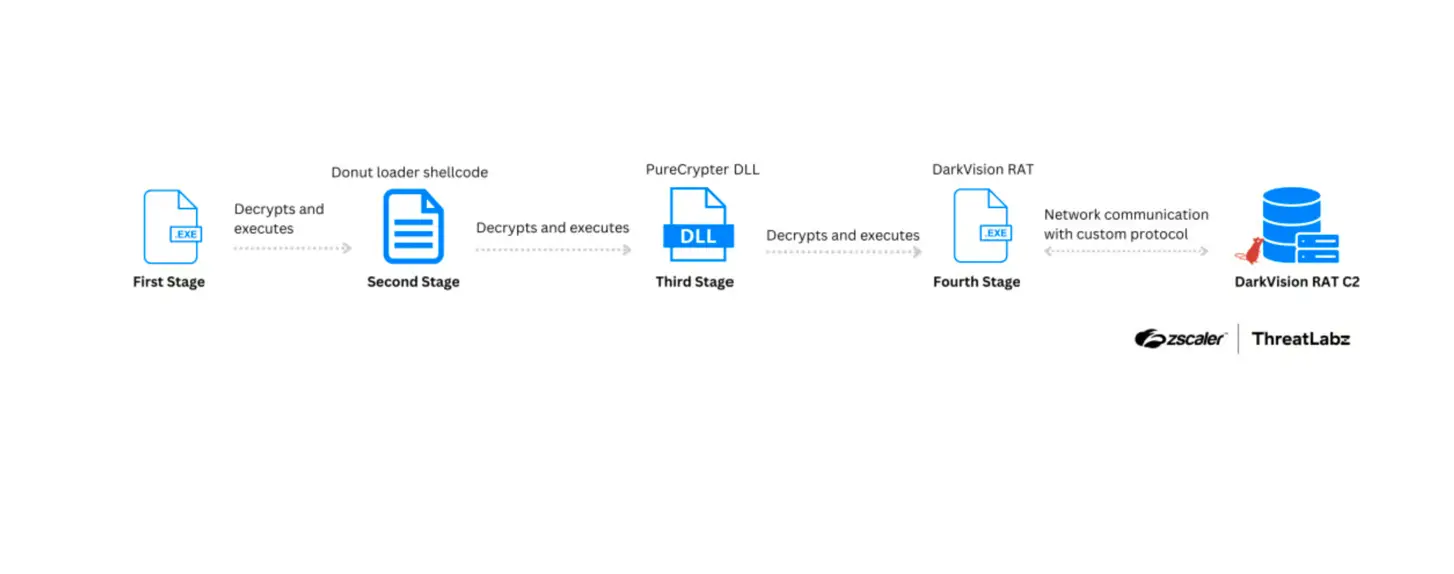
An example attack chain distributing DarkVision RAT as the payload in the final stage | Image: ThreatLabz
A detailed technical analysis of DarkVision RAT by security researcher Muhammed Irfan V A at ThreatLabz has shed light on the evolution and growing sophistication of this remote access trojan (RAT). First emerging in 2020, DarkVision RAT has become increasingly popular among cybercriminals due to its low cost and robust feature set. According to the analysis, “DarkVision RAT is a highly customizable remote access trojan (RAT) offered on Hack Forums and their website for as little as $60,” making it accessible even to low-skilled attackers.
The analysis reveals that DarkVision RAT is equipped with an extensive range of capabilities, including keylogging, file manipulation, process injection, password theft, and remote code execution. Its affordability and wide array of features have made it a popular tool for attackers seeking to infiltrate systems and steal sensitive data. Most recently, in July 2024, ThreatLabz observed DarkVision being distributed alongside another piece of malware, PureCrypter, in a new campaign.
The attack chain analyzed by ThreatLabz provides critical insights into how DarkVision is deployed. The campaign typically begins with a .NET executable protected using .NET Reactor. Once executed, the file initiates a series of steps to decrypt and execute subsequent stages, ultimately leading to the installation of DarkVision RAT.
The report notes, “DarkVision RAT communicates with its command-and-control (C2) server using a custom network protocol via sockets,” allowing it to receive commands and exfiltrate data from infected systems.
One of DarkVision RAT’s strengths lies in its evasion tactics. The RAT uses DLL hijacking, process injection, and auto-elevation techniques to bypass security defenses and gain elevated privileges on targeted systems. Additionally, the RAT uses Windows Defender exclusions to avoid detection, as well as multiple persistence mechanisms to ensure it remains active even after system reboots.
DarkVision RAT employs three persistence methods: placing scripts in the Windows startup folder, using autorun registry keys, and scheduling tasks via Task Scheduler. According to the report, the RAT is highly adaptable, with flags that allow attackers to choose which persistence method to use, making it difficult to detect.
The report details DarkVision RAT’s support for a wide variety of commands, enabling attackers to perform actions such as file manipulation, process termination, password theft, and DLL hijacking. Moreover, DarkVision RAT can load encrypted plugins that add further malicious capabilities. The analysis states, “Most of the DarkVision RAT’s features are implemented through plugins. These plugins remain as plain text only in memory, while they are stored as encrypted data on disk and in the registry.”
These plugins can be used to capture keystrokes, webcam footage, audio recordings, and even manipulate system processes. For example, one plugin allows attackers to retrieve and set the desktop wallpaper, while others can perform remote access using Virtual Network Computing (VNC) or reverse proxy operations.
The resurgence of DarkVision RAT in recent malware campaigns underscores its growing popularity and adaptability. With its low price and highly customizable nature, DarkVision RAT is likely to remain a staple in the toolkits of cybercriminals. As noted in the report, “DarkVision RAT represents a potent and versatile tool for cybercriminals, offering a wide array of malicious capabilities, from keylogging and screen capture to password theft and remote execution.”
Related Posts:
- Stealthy New Android Trojan Disguised as Popular Apps Steals Your Data
- npm’s Hidden Threat: The Covert Trojan Lurking in Your Windows System
- Beware of Word: Remcos RAT Lurks in Malicious Documents
- Remcos RAT: Hackers Target Ukrainian Government with Surveillance Tool
- Tax Extension Malware Campaign Exploits Trusted GitHub Repositories to Deliver Remcos RAT