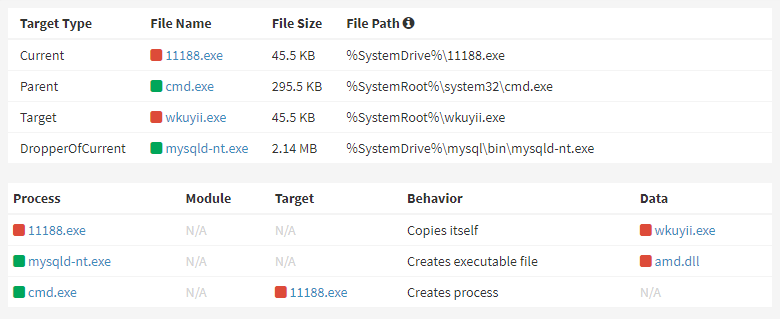
Ddostf DDoS bot being installed via MySQL service
AhnLab has discovered attacks on vulnerable MySQL servers using the Ddostf bot for DDoS assaults. First identified in 2016, Ddostf supports both Windows and Linux and is presumably developed in China. AhnLab has been monitoring persistent attacks on MySQL servers operating in the Windows environment.
The Ddostf DDoS bot is formatted as ELF for Linux environments and PE for Windows. A notable feature of Ddostf is the presence of the string “ddos.tf” in its binary code. Upon activation, Ddostf replicates itself into the “%SystemRoot%” directory under a random name and registers itself as a service.

Once connected, the bot collects basic data from the infected device and transmits it to the Command and Control (C2) server. The C2 server, in return, sends data including URLs for downloading and commands for specific DDoS attack methods.
Ddostf employs attack methods such as SYN flood, UDP flood, and HTTP GET/POST flood. Additionally, Ddostf can establish connections with new addresses obtained from the C2 server and execute commands over a set period, indicating the potential for widespread system infections and the subsequent offering of DDoS attacks as a service.
Typically, attackers use scanning to identify potential targets, especially systems utilizing port 3306/TCP, used by MySQL servers. Cybercriminals may then assault the system using brute force or dictionary attacks.
If a system poorly manages user credentials, attackers can gain access to administrator accounts. Vulnerabilities in outdated software versions may also be exploited.