Decoding NodeStealer: How Facebook Ads Became Malware Vessels
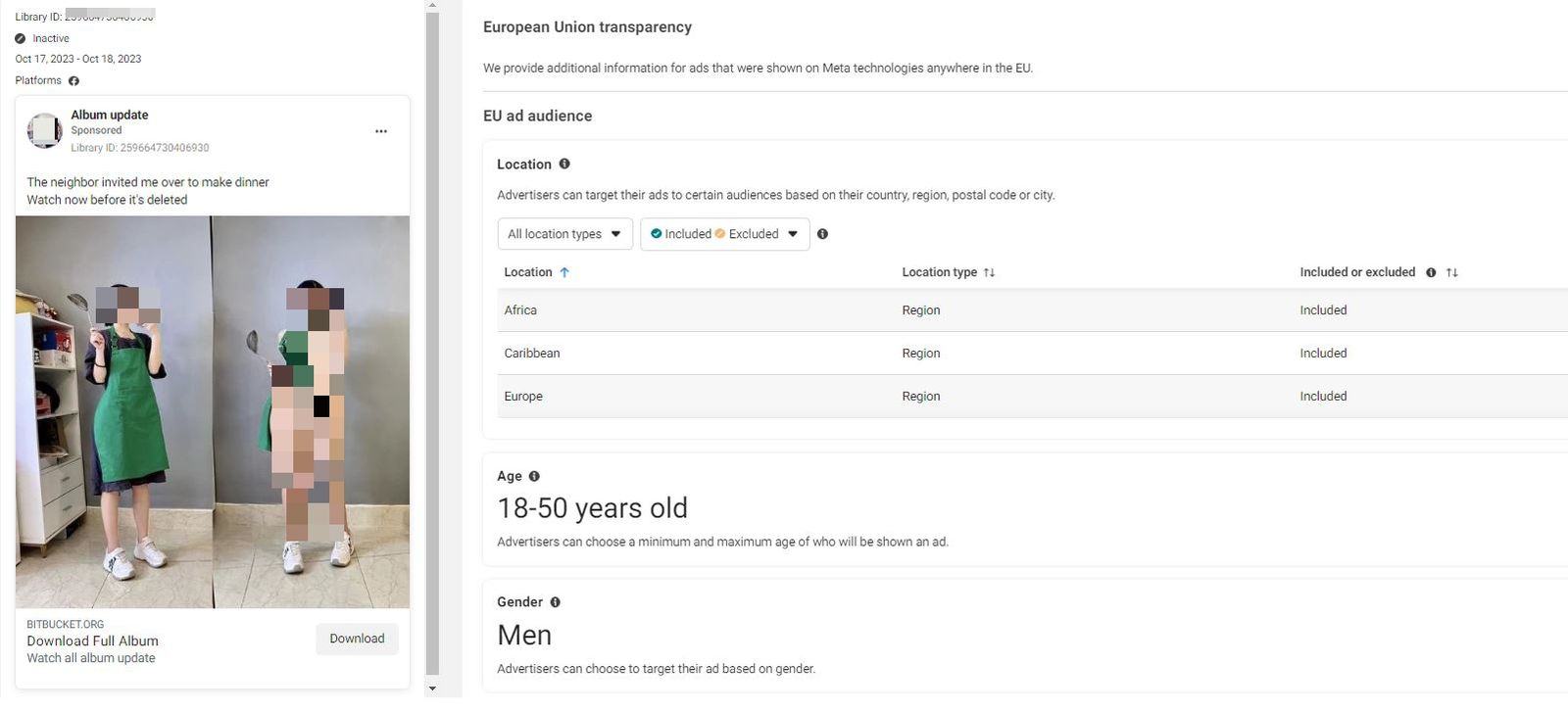
Security researchers at Bitdefender have unveiled that cybercriminals are exploiting Facebook advertising to disseminate malware and usurp users’ social network accounts.
In this malign campaign, perpetrators harness legitimate online advertising tools to broadcast typical adverts interspersed with malicious links. The campaign conspicuously employs the imagery of women to captivate users’ attention.
The researchers reveal that the campaign’s objective is to deliver a novel iteration of the pernicious NodeStealer malware onto victims’ devices. Some of the photographs embedded in the advertisements appear to have been manipulated or artificially generated using advanced artificial intelligence techniques.
In the detected operation, malefactors have utilized at least ten compromised business accounts to orchestrate the ad campaign, disseminating the malware among the regular Facebook populace—predominantly men over 40 from Europe, Africa, and the Caribbean Basin.

Image: Bitdefender
A single click on these advertisements precipitates the immediate download of the malicious executable file onto the victim’s device. It is estimated that nearly 100,000 users downloaded this malware within a mere span of ten days. The identity of the hacking syndicate behind this campaign remains obscure, though initial NodeStealer assaults were attributed to Vietnamese threats targeting business accounts via Facebook Messenger.
NodeStealer is a relatively new info-stealer that, among other capabilities, enables felons to purloin browser cookies and commandeer Facebook accounts. The iteration of NodeStealer malware discovered in this latest campaign has evolved with new features that allow hackers to penetrate Gmail and Outlook platforms and introduce additional malignant payloads.
Once cybercriminals acquire access to a user’s browser cookies through NodeStealer’s elementary functions, they can seize control of Facebook accounts and gain entry to sensitive information.
The hackers may then proceed to alter passwords and institute supplementary security measures on the accounts to entirely preclude access by the rightful owner, thereby gaining the means to perpetrate fraud with impunity.





