DeleFriend Vulnerability: Google Denies Design Flaw
Google disputes claims of a design flaw in Google Workspace uncovered by Hunters Security researchers. Hunters Security believes that the error allows an attacker to steal email from Gmail, exfiltrate data from Google Drive, and perform other unauthorized actions in Google Workspace APIs.
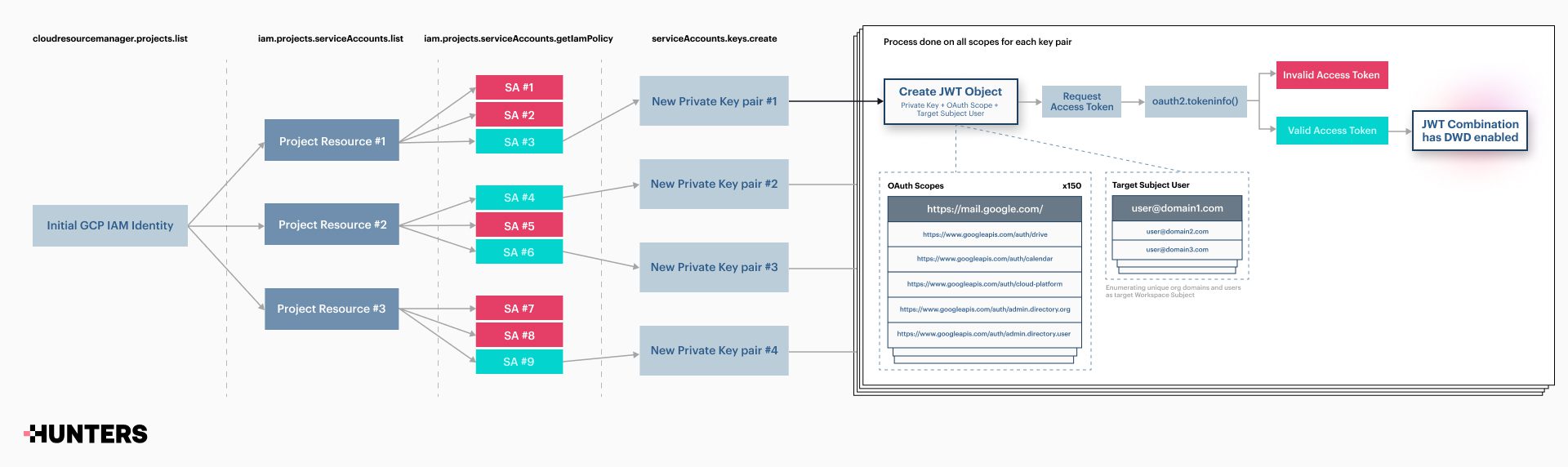
Hunters researchers dubbed the vulnerability “DeleFriend”. The error enables an attacker to manipulate existing delegations in Google Cloud Platform (GCP) and Google Workspace without the superadministrator status that is typically required to create new delegations. The flaw provides the opportunity to search for Google service accounts with global delegations and escalate privileges.

The issue stems from the fact that domain delegation configuration is determined by the service account resource identifier (OAuth ID), not by specific private keys associated with the service account identity object. In addition, no limits on JSON Web Token (JWT) combination fuzzing are implemented at the API level, which allows a cybercriminal to create numerous JSON web tokens with different OAuth scopes — or pre-defined access policies — to attempt to identify accounts with domain-wide delegation enabled.
However, Google claims that there are no security issues in its products and recommends that users use the minimum possible privileges to protect themselves from such attacks. Hunters researchers published a Proof-of-Concept (PoC) exploit on GitHub that demonstrates how an attacker can use DeleFriend vulnerability to perform a variety of malicious actions. These include unauthorized access to data and services, data modification, user impersonation, and monitoring of meetings in Google Calendar.
Hunters Security proposed several solutions to the problem, including limiting the number of JWT requests using the same key and revising the permissions associated with the Editor role. The company reported the issue to Google in August, but Google has not yet addressed the vulnerability.





