detect-secrets
detect-secrets is an aptly named module for (surprise, surprise) detecting secrets within a code base.
However, unlike other similar packages that solely focus on finding secrets, this package is designed with the enterprise client in mind: providing a backward-compatible, systematic means of:
- Preventing new secrets from entering the code base,
- Detecting if such preventions are explicitly bypassed, and
- Providing a checklist of secrets to roll, and migrate off to more secure storage.
This way, you create a separation of concern: accepting that there may currently be secrets hiding in your large repository (this is what we refer to as a baseline), but preventing this issue from getting any larger, without dealing with the potentially gargantuous effort of moving existing secrets away.
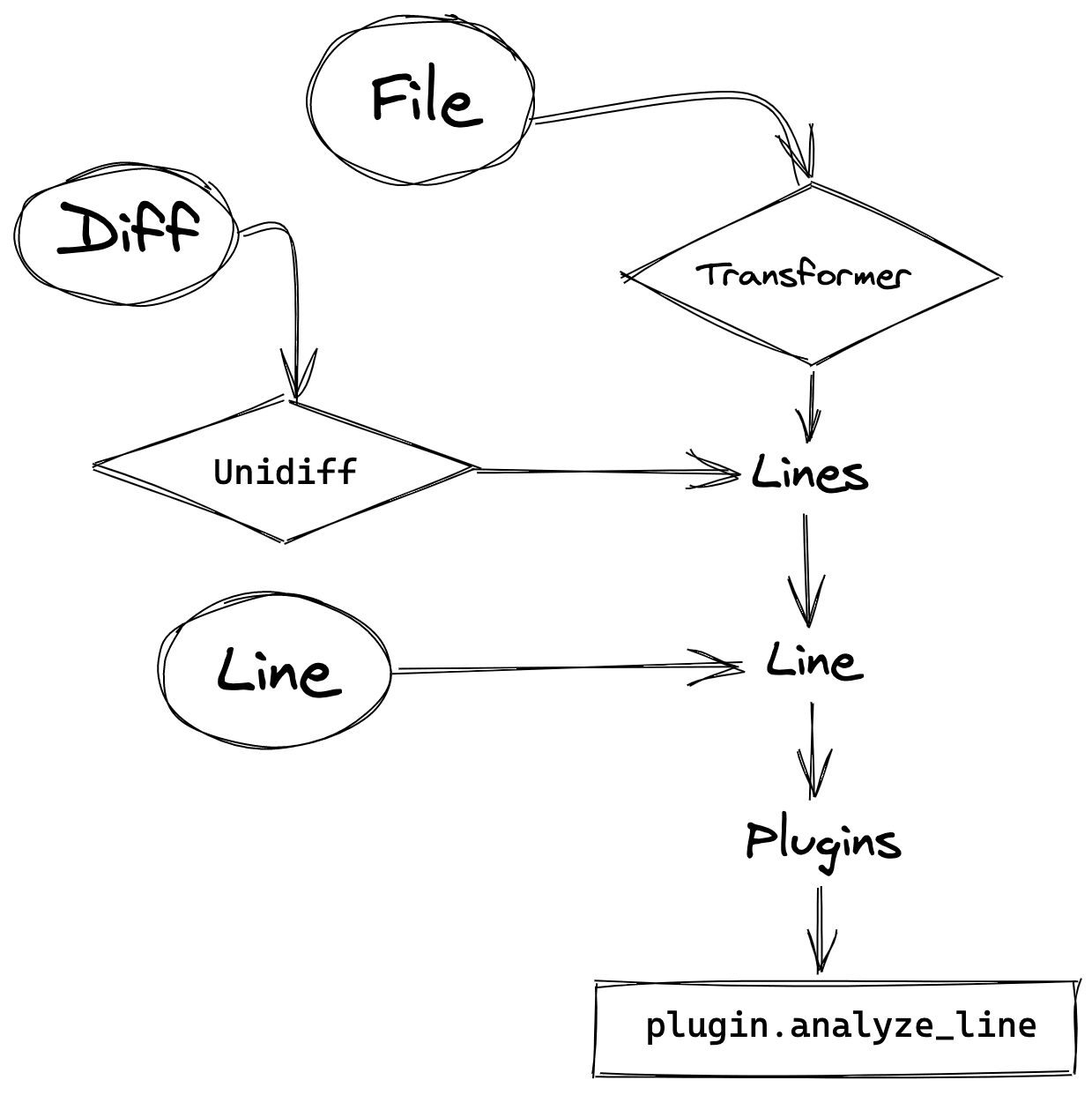
It does this by running periodic diff outputs against heuristically crafted regex statements, to identify whether any new secret has been committed. This way, it avoids the overhead of digging through all git history, as well as the need to scan the entire repository every time.

Changelog v1.4
📰 News
- We’re dropping support for Python 3.6 starting v1.5.0! Python 3.6 reached EOL on December 23, 2021 and, therefore, is currently unsupported. We hope this announcement gives you plenty of time to upgrade your project, if needed.
📣 Release Highlights
- Improved filtering by excluding secrets that have already been detected by a regex-based detector ([#612])
- Added a detector for Discord bot tokens ([#614])
- Improved the audit report to make it easier to parse programmatically ([#619])
- Added support for .NET packages.lock.json files in the heuristic filter ([#593])
Install & Use
Copyright 2017-2018 Yelp Inc.