Detection Replay Framework
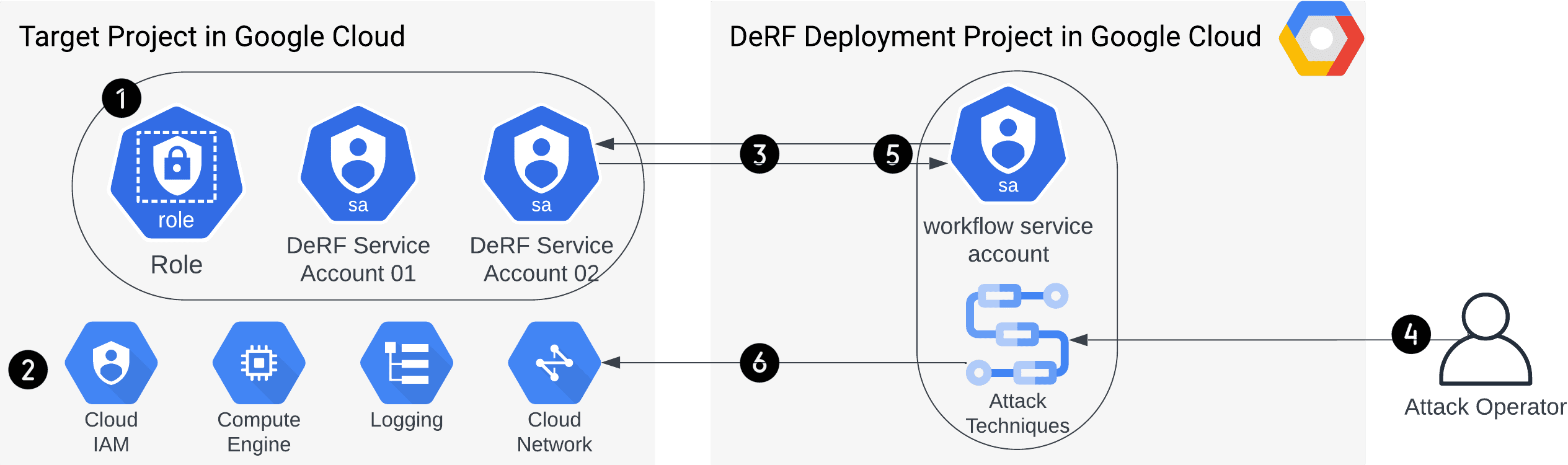
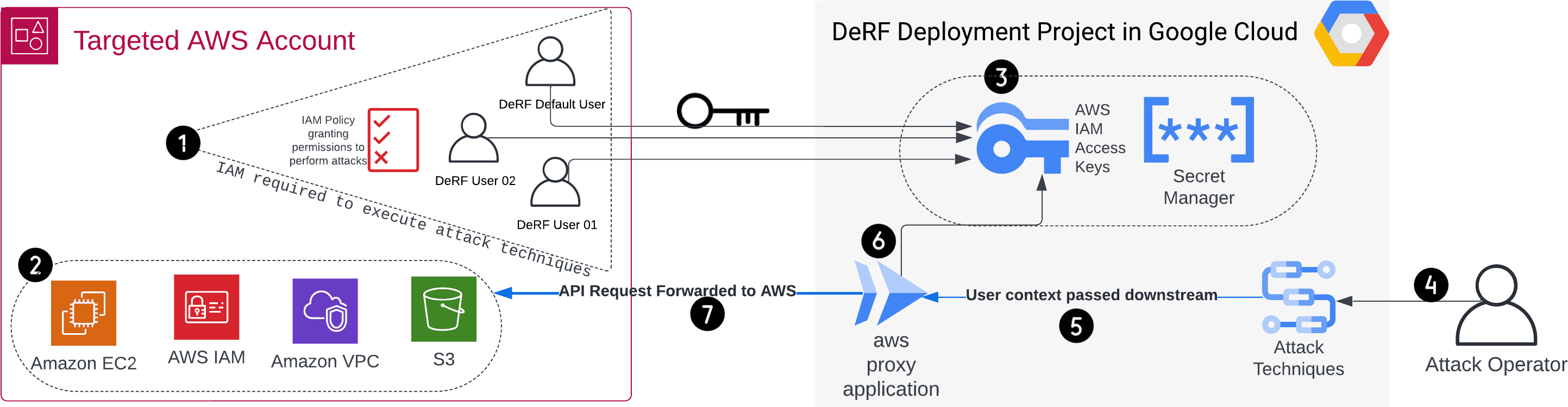
DeRF (Detection Replay Framework) is an “Attacks As A Service” framework, allowing the emulation of offensive techniques and generation of repeatable detection samples from a UI – without the need for End Users to install software, use the CLI, or possess credentials in the target environment.
The DeRF deploys and manages the target cloud infrastructure, which is manipulated to simulate attacker techniques. Terraform is used to manage all resources, deploying (and destroying) hosted attack techniques and target infrastructure in under 3 minutes.
Key features of this tool include:
• User-Friendly Interface: Since the DeRF is hosted in Google Cloud, End Users can invoke attacks through the cloud console UI without the need to install software or use the CLI.
• Accessibility for Non-Security Professionals: The DeRF caters to a broad audience of End Users, including Engineering, Sales, Support Staff, or automated processes.
• Robust OpSec: Long-Lived Credentials are not passed between operators, instead access to the DeRF and its attack techniques are controlled through GCP IAM Role-Based Access Control (RBAC)
• Extensibility at its Core: Attack sequences are written in YAML, enabling easy configuration of new techniques.
• Turn-Key deployment: Deploying (and destroying!) the DeRF is a fully automated process, completed in under 3 minutes.
High-Level Architecture
The DeRF’s unique architecture is wholly deployed via terraform. It consists of resources spread across AWS and GCP.
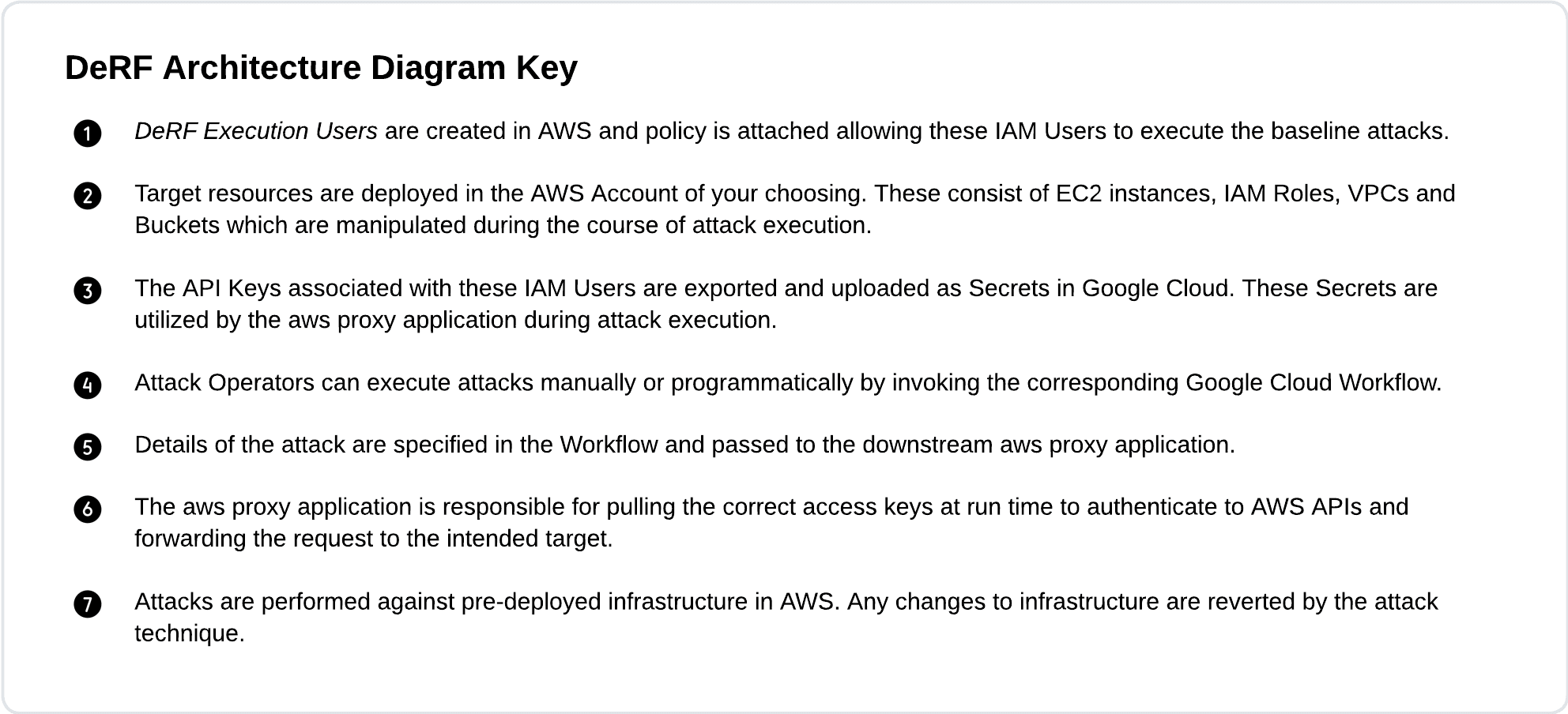
DeRF Attack Architecture for AWS
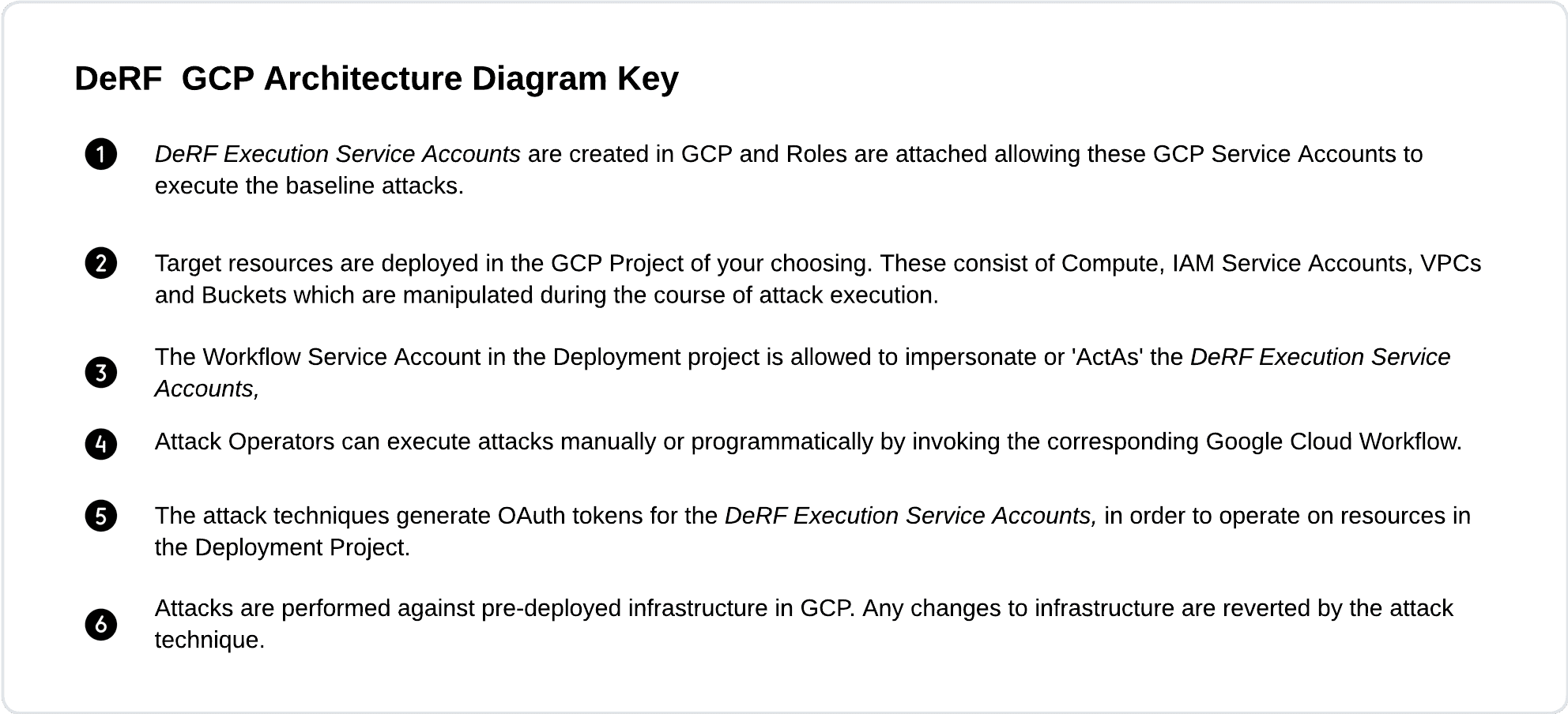
DeRF Attack Architecture for GCP

Install & Use
Copyright (C) 2023 vectra-ai-research