DetectionLabELK
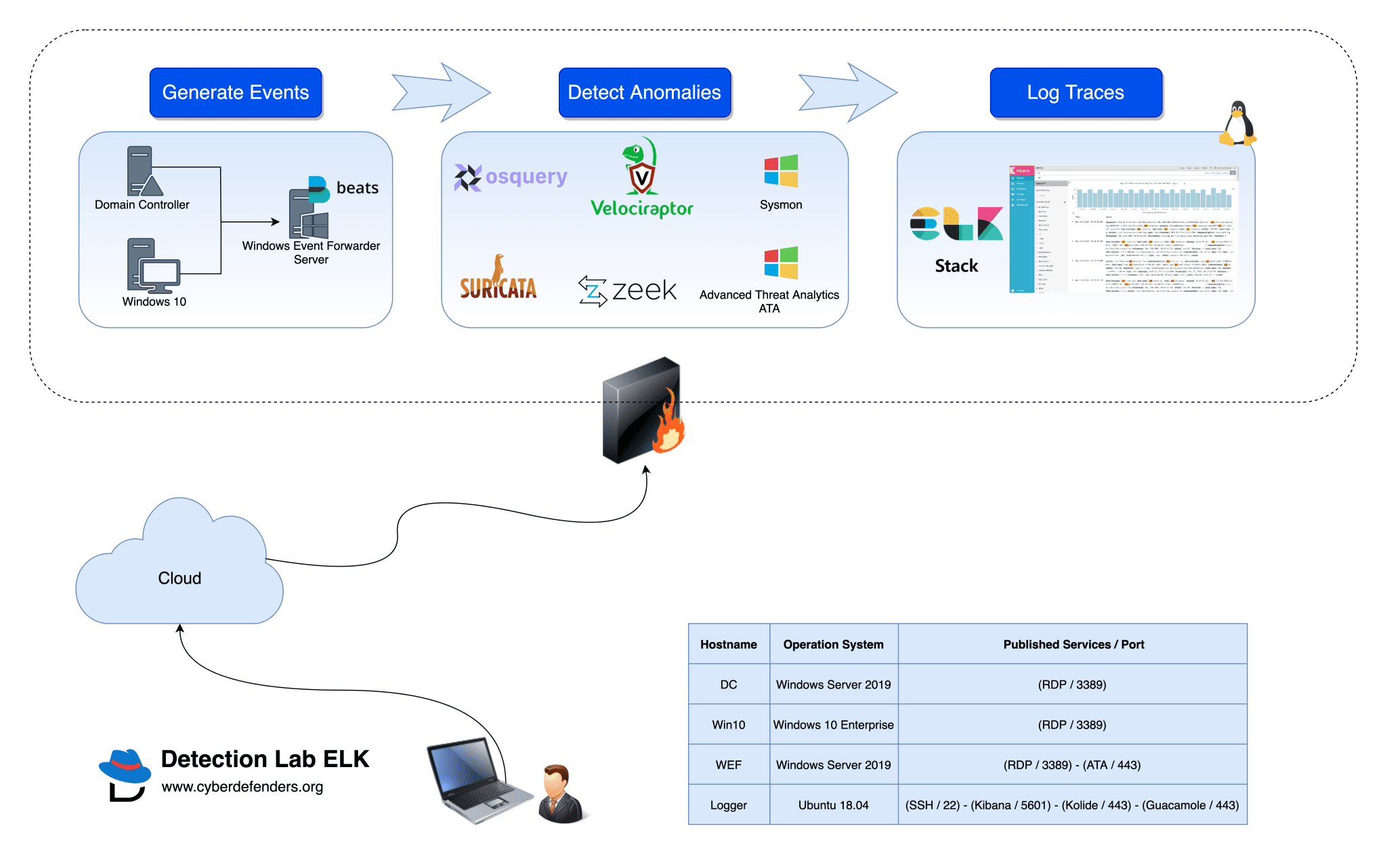
DetectionLabELK is the perfect lab to use if you would like to build effective detection capabilities. It has been designed with defenders in mind. Its primary purpose is to allow blueteams to quickly build a Windows domain that comes pre-loaded with security tooling and some best practices when it comes to system logging configurations. It can easily be modified to fit most needs or expanded to include additional hosts.

Use cases:
A popular use case for DetectionLabELK is when you consider adopting the MITRE ATT&CK framework and would like to develop detections for its tactics. You can use DetectionLabELK to quickly run atomic tests, see what logs are being generated, and compare them to your production environment. This way you can:
- Validate that your production logging is working as expected.
- Ensure that your SIEM is collecting the correct events.
- Enhance alerts quality by reducing false positives and eliminating false negatives.
- Minimize coverage gaps.
Lab Information:
- Domain Name: windomain.local
- Windows Admininstrator login: vagrant:vagrant
- Fleet login: https://192.168.38.105:8412 – vagrant:vagrant
- Kibana login: http://192.168.38.105:5601 – vagrant:vagrant
- Microsoft ATA login: https://192.168.38.103 – vagrant:vagrant
- Guacamole login: http://192.168.38.105:8080/guacamole – vagrant:vagrant
- Velociraptor: https://192.168.38.105:9999 – vagrant:vagrant
Primary Lab Features:
- Microsoft Advanced Threat Analytics is installed on the WEF machine, with the lightweight ATA gateway installed on the DC
- Windows Event forwarder along with Winlogbeat are pre-installed and all indexes are pre-created on ELK. Technology add-ons for Windows are also preconfigured.
- A custom Windows auditing configuration is set via GPO to include command-line process auditing and additional OS-level logging
- Palantir’s Windows Event Forwarding subscriptions and custom channels are implemented
- Powershell transcript logging is enabled. All logs are saved to \\wef\pslogs
- osquery comes installed on each host and is pre-configured to connect to a Fleet server via TLS. Fleet is preconfigured with the configuration from Palantir’s osquery Configuration
- Sysmon is installed and configured using Olaf’s open-sourced configuration
- All autostart items are logged to Windows Event Logs via AutorunsToWinEventLog
- SMBv1 Auditing is enabled
Lab Hosts:
- DC – Windows 2016 Domain Controller
- WEF Server Configuration GPO
- Powershell logging GPO
- Enhanced Windows Auditing policy GPO
- Sysmon
- osquery
- Elastic Beats Forwarder (Forwards Sysmon & osquery)
- Sysinternals Tools
- Microsft Advanced Threat Analytics Lightweight Gateway
- WEF – Windows 2016 Server
- Microsoft Advanced Threat Analytics
- Windows Event Collector
- Windows Event Subscription Creation
- Powershell transcription logging share
- Sysmon
- osquery
- Elastic Beats Forwarder (Forwards WinEventLog & Powershell & Sysmon & osquery)
- Sysinternals tools
- Win10 – Windows 10 Workstation
- Simulates employee workstation
- Sysmon
- osquery
- Sysinternals Tools
- Logger – Ubuntu 18.04
- Kibana
- Fleet osquery Manager
- Bro
- Suricata
- Elastic Beats Forwarder (Forwards Bro logs & Suricata & osquery)
- Guacamole
- Velociraptor
Install
Copyright (c) 2017 Chris Long