
Wiz Threat Research revealed a new malware campaign orchestrated by the Romanian-speaking threat group Diicot, also known as Mexals. This campaign targets Linux environments with advanced malware techniques, marking a significant escalation in their capabilities. The group has a history of exploiting Linux systems for cryptojacking, employing tools like XMRig and sophisticated self-propagating mechanisms.
According to Wiz Research, the updated malware demonstrates an alarming level of sophistication compared to its earlier iterations, highlighting the attackers’ ability to adapt and refine their tactics. “The malware we analyzed includes notable improvements that reflect a deeper level of sophistication,” the report states. Key advancements include the introduction of new command-and-control (C2) infrastructure, the transition from Discord-based C2 to HTTP, and the adoption of the Zephyr protocol alongside Monero mining.
The malware also features improved obfuscation techniques. For instance, the modified UPX headers now include corrupted checksums, rendering standard unpacking tools ineffective. Such changes indicate an ongoing effort to bypass modern security measures and thwart automated detection.
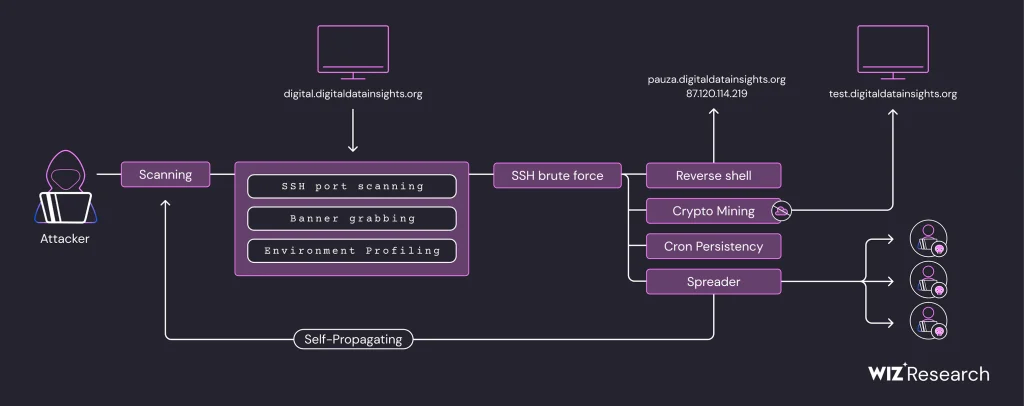
A standout feature of this campaign is its ability to tailor its behavior to the environment. In cloud setups, the malware prioritizes spreading to other hosts, while in traditional environments, it deploys cryptomining payloads. “Cloud detection logic,” the report explains, “is based on the remote machine’s Linux distribution and version,” showcasing the group’s meticulous attention to their targets.
Payloads uncovered during the investigation include:
- Brute-Spreader: The main payload that spreads across networks and maintains persistence.
- Reverse Shell (client.go): Grants attackers full remote control of compromised machines.
- SSH Banner Scanner: Identifies weak SSH credentials to gain initial access.
The campaign poses a significant risk to Linux-based systems running OpenSSH. Weak credentials and misconfigured security settings can easily become entry points for this advanced malware. Wiz researchers emphasize, “If your systems rely on SSH and aren’t properly secured, they could easily become targets.”
Cryptojacking remains a central motive behind Diicot’s operations. The attackers have earned over $16,000 from Monero mining, with additional, harder-to-trace earnings from the Zephyr protocol. Beyond financial losses, organizations face risks of data exfiltration, system compromise, and potential operational disruptions.
As the Diicot group evolves, so must defense strategies. Wiz Research recommends strengthening SSH configurations, enforcing strong passwords, and deploying advanced detection mechanisms capable of identifying obfuscated payloads.
Related Posts:
- New Phishing Campaign Targets AWS Accounts: Security Experts Warn
- No Deal: Wiz Rejects Google, Sets Sights on IPO
- Spring Boot Actuator Misconfigurations: The Hidden Security Risks in Cloud Environments
- Scattered Spider Spins a New Web: Detecting 0ktapus Phishing Domains
