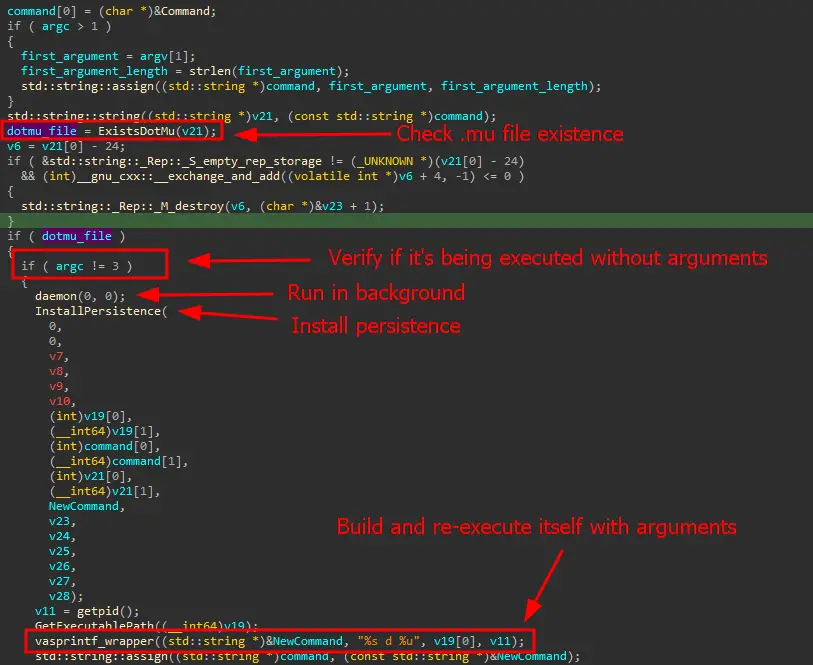
Backdoor main code
Security researchers at Kaspersky Labs have uncovered a dangerous new variant of the DinodasRAT malware that targets Linux operating systems. This latest version represents a significant expansion in the threat actor’s capabilities as the malware was previously known to focus on Windows machines.
DinodasRAT, also known as XDealer, is a sophisticated backdoor trojan programmed in C++ that gives attackers extensive control over infected systems. It allows them to monitor activity, steal sensitive information, and potentially execute further malicious code.
Linux in the Crosshairs

Kaspersky’s discovery comes shortly after ESET researchers exposed a Windows-based DinodasRAT operation targeting government entities in Guyana. This newly uncovered Linux version suggests an ongoing campaign from a well-resourced and determined threat group.
The Linux variant of DinodasRAT primarily targets Red Hat-based distributions and Ubuntu Linux. It employs a multi-step process to gain initial access, establish persistence on infected devices, and communicate with command-and-control (C2) servers.
Advanced Evasion and Persistence
Before dialing home to its command and control (C2) server, DinodasRAT embarks on gathering intelligence about its host. Notably, it steers clear of personal user data, focusing instead on hardware-specific information to craft a unique identifier (UID) for each victim. This UID becomes the cornerstone of the implant’s stealth, as it carefully archives this data along with other system specifics in a concealed configuration file, ensuring its operations remain under the radar.
The malware is designed to be stealthy and evade detection. It employs a ‘mutex’ technique to prevent multiple instances from running and uses Linux’s service managers, such as SystemV or Systemd, to ensure it automatically restarts each time the system boots. The attackers also carefully manipulate file timestamps to mask their activity.
Shared Tactics and Infrastructure
The backdoor maintains communication with its C2 server mirroring the methodology of its Windows counterpart, albeit with tailored nuances for Linux systems. It employs a mix of TCP and UDP communications, encrypted using the Tiny Encryption Algorithm (TEA) to safeguard its exchanges. The encryption keys, shared with the Windows version, underscore the interconnected nature of these threats.
Countries Affected
Kaspersky telemetry data reveals China, Taiwan, Turkey, and Uzbekistan as the countries most affected by the Linux variant of DinodasRAT.
Protect Your Linux Systems
Organizations relying on Linux systems must take this threat seriously. Implement robust security measures including:
- Regular system updates and patching: Address known vulnerabilities quickly.
- Endpoint protection: Deploy reputable antivirus and anti-malware solutions
- Network monitoring: Look for unusual traffic patterns or connections.
- User awareness training: Educate employees about phishing and social engineering tactics often used for initial infection.
Stay Vigilant
The DinodasRAT campaign highlights the evolving threat landscape and the importance of cross-platform security. Security professionals should stay informed of the latest threat intelligence to protect critical systems effectively.
For more information and indicators of compromise (IOCs), refer to the full Kaspersky Labs report.