“Dirty Stream” Vulnerability Pattern Uncovered: New Threat Imperils Popular Android Apps
Security researchers at Microsoft Threat Intelligence have revealed a critical vulnerability pattern affecting a wide array of popular Android applications. Dubbed “Dirty Stream,” this vulnerability presents a new method for malicious apps to subvert legitimate applications, potentially leading to full device compromise and data theft. The discovery impacts multiple popular Android apps with over four billion installations collectively.
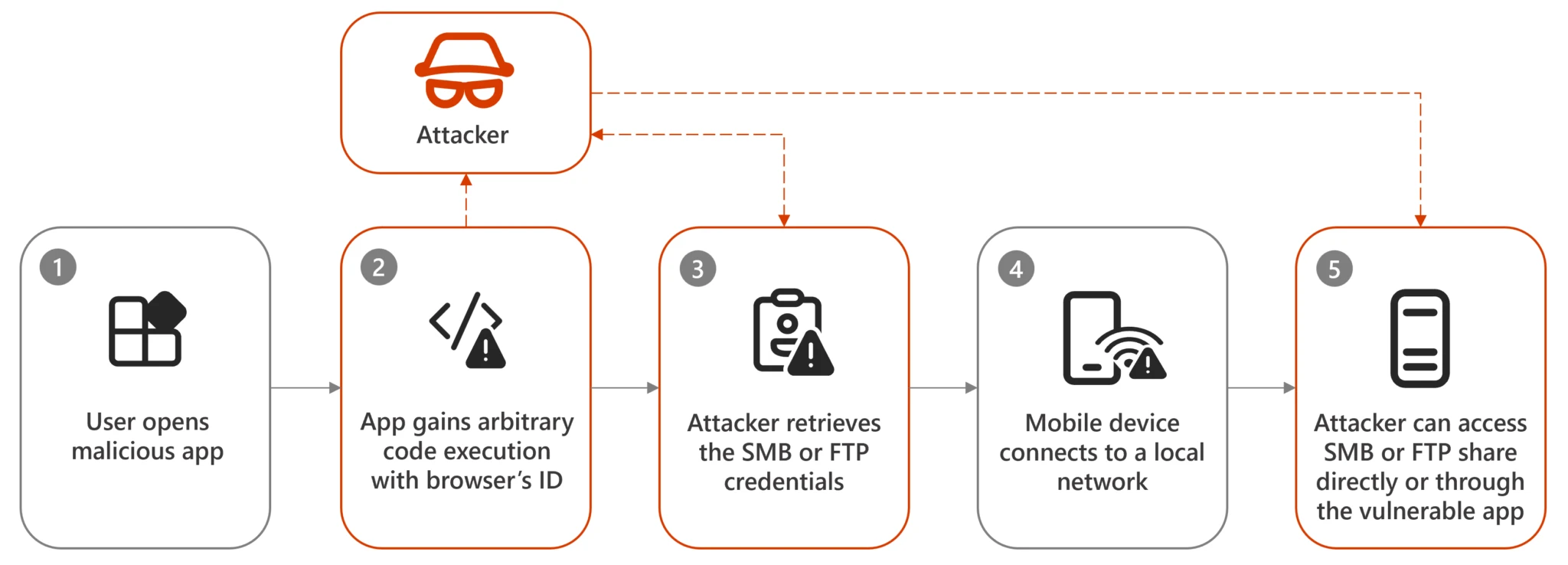
The vulnerability stems from improper implementation of file sharing and handling mechanisms in Android. Specifically, it exploits path traversal vulnerabilities when applications share data using Android’s ContentProvider components. Microsoft identified that when a file is sent to another app, the receiving application might not properly verify the file’s contents or its origin, assuming the file name provided by the sending app is trustworthy. This assumption can lead to critical files being overwritten within the app’s private data space.
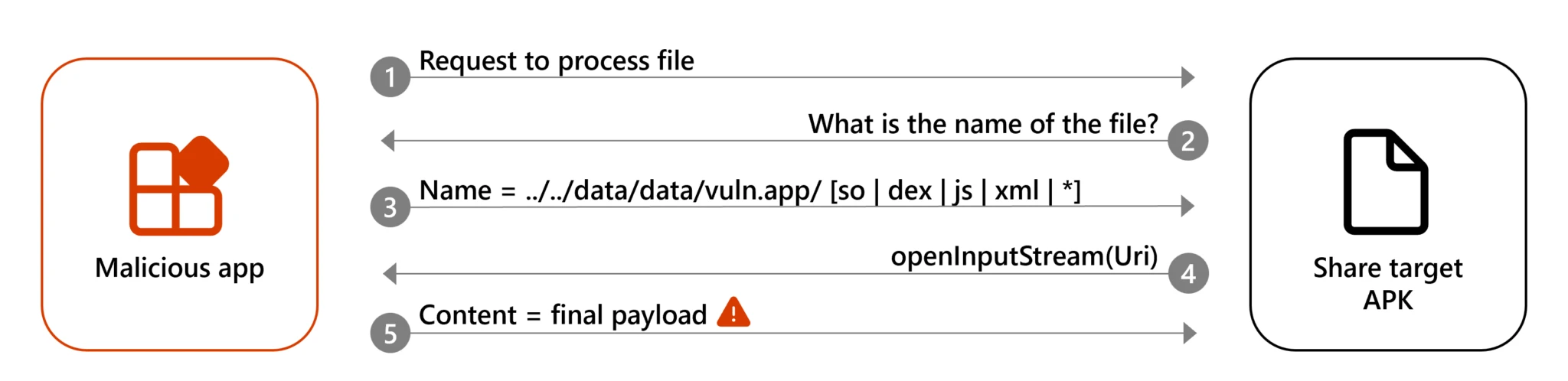
Dirty stream attack | Image: Microsoft
Among the affected applications, some notable ones include Xiaomi Inc.’s File Manager and WPS Office, each boasting hundreds of millions of installations. These vulnerabilities were disclosed responsibly to the developers, and patches have been issued. However, the potential implications of such vulnerabilities are vast, ranging from unauthorized access to sensitive user data to complete control over the affected device.
In a detailed case study of Xiaomi Inc.’s File Manager, Microsoft demonstrated how a malicious app could exploit this vulnerability to execute arbitrary code. The malicious app could replace a native library file used by the file manager, leading to the execution of arbitrary code with the same permissions as the file manager itself. This could allow attackers to access or modify files, install additional malicious software, or steal user data.

Getting remote access to local shares | Image: Microsoft
Following the discovery, Microsoft collaborated with Google and affected app developers to address the issues. They also published detailed guidance on the Android Developers website to help other developers identify and mitigate similar vulnerabilities in their applications.
For developers, Microsoft recommends employing more robust file handling and validation mechanisms to prevent similar vulnerabilities. Developers should avoid trusting file names provided by external sources and should use sandbox environments to test file handling securely. They also suggest using tools like Android Lint and GitHub’s CodeQL to identify potential security flaws in code.
For users, the advice is straightforward: keep your apps updated. Ensuring that you are running the latest versions of your apps can protect against known vulnerabilities. Users should also be cautious about the permissions they grant to apps and avoid downloading apps from untrusted sources.