
Nova, a newly discovered fork of the infamous Snake Keylogger family, is a growing challenge in cybersecurity.
According to research conducted by ANY.RUN, this variant employs advanced techniques to steal sensitive data while evading detection, marking another step in the evolution of credential-stealing malware.
Let’s dive deeper into how Nova operates and what makes it so dangerous.
To discover all the technical details of this malware, let’s have a look at its analysis session inside the ANY.RUN sandbox.
Victim Information Collection
One of Nova’s primary objectives is to gather detailed information about its victims. This process is evident in its network behavior.
In the HTTP Requests tab of the analysis session, Nova sends requests to hxxp[://]checkip[.]dyndns[.]org/. This domain provides the public IP address of the victim’s device, which can be used to determine their location and network details.
Such information is often critical for attackers to understand the victim’s environment and customize their malicious operations.
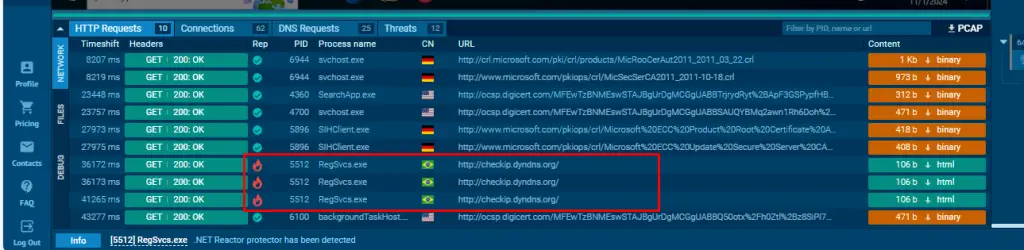
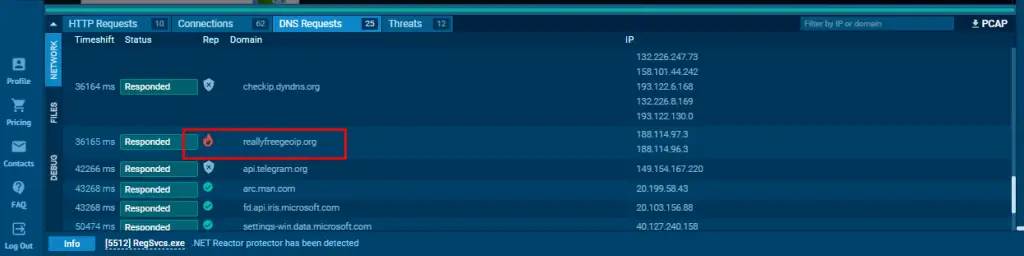
The DNS Requests tab reveals that Nova queries reallyfreegeoip[.]org. This domain helps the malware retrieve the country name associated with the victim’s device.
By knowing the victim’s geographical location, attackers can tailor their campaigns or avoid regions where cybersecurity defenses are stronger.
The collected data also includes the PC name, date and time, and other system-specific information. This information is compiled into a formatted string for further use, often aiding attackers in organizing stolen data or profiling targets for subsequent attacks.
| Sign up now for a free 14-day trial and analyze unlimited malware with ANY.RUN’s interactive sandbox. |
Credential Theft Across Platforms
Nova targets popular web browsers like Google Chrome, Mozilla Firefox, Brave, and Microsoft Edge to steal saved login credentials.
The process begins with Nova identifying the exact location of the Login Data SQLite file in Chrome’s user data directory. This file serves as a repository for saved usernames and encrypted passwords.
Once located, Nova analyzes the database to extract entries containing critical information such as:
- website URL (origin_url),
- username (username_value),
- encrypted password (password_value).
To decrypt these stored passwords, Nova employs sophisticated techniques tailored to the browser’s encryption methods. For modern versions of Chrome, it accesses the Local State file, which contains the encrypted master key used for protecting stored credentials. Nova then decrypts this key and uses it to retrieve plaintext passwords from the SQLite database.
In cases where older versions of Chrome are targeted, Nova switches to alternative decryption methods like its custom Decrypttttt function.
Email Client Credential Theft
Nova also targets email clients like Outlook, Foxmail, and Thunderbird by exploiting Windows registry keys where profile information is stored.
For instance, when targeting Outlook, the process begins with Nova initializing a list to store recovered account details and preparing a set of search parameters for locating password-related data in the Windows registry. It then scans specific registry keys known to store Outlook profile information, such as:
- Software\\Microsoft\\Office\\15.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676
- Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows Messaging Subsystem\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676
- Software\\Microsoft\\Windows Messaging Subsystem\\Profiles\\9375CFF0413111d3B88A00104B2A6676
- Software\\Microsoft\\Office\\16.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676
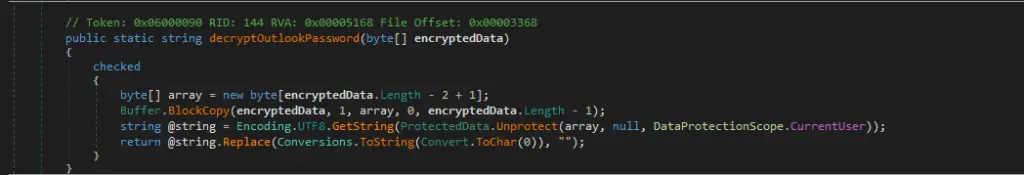
Once the relevant entries are identified, Nova iterates through the registry keys and subkeys, extracting encrypted email credentials. The decryption process involves the decryptOutlookPassword function, which takes the encrypted password as a byte array, removes unnecessary elements, and converts it into a readable string using advanced decryption techniques.
After stripping any null characters, Nova retrieves additional details such as the email address and SMTP server information, consolidating this data into a complete account profile.
Extracting Windows Product Key
Nova is equipped with the ability to extract and decode the Windows product key, a unique identifier associated with the operating system installation. This capability can assist attackers in replicating system environments or bypassing software licensing restrictions.
To achieve this, Nova accesses the Windows registry key located at:
Software\Microsoft\Windows NT\CurrentVersion.
Within this key, it retrieves the DigitalProductID as a byte array, which contains the necessary data for generating the product key. Nova isolates a specific portion of this array starting at index 52, copying it into a new byte array.
The decoding process involves running a nested loop to convert the extracted bytes into the alphanumeric characters that form the product key. The outer loop iterates 25 times, generating each character in the key, while the inner loop processes the bytes in reverse order to complete the decoding. Once fully decoded, the product key is returned in a standard format, such as: XXXXX-XXXXX-XXXXX-XXXXX-XXXXX.
Extracting Clipboard Data
According to the analysis carried out by ANY.RUN, Nova also monitors and extracts clipboard content, an effective way to capture sensitive information such as passwords, payment details, or other copied text. The process includes:
- Checking if the clipboard contains text in Unicode format using IsClipboardFormatAvailable.
- Opening the clipboard with OpenClipboard to access its contents.
- Retrieving the data handle in the specified format through GetClipboardData.
This seemingly simple functionality is a powerful tool for intercepting private information that users temporarily store in their clipboard.
Data Exfiltration via Nova
Nova employs three primary methods for data exfiltration, FTP, SMTP, and Telegram, depending on the configuration set by its creators. The choice of method is determined by specific flags within the malware’s code, specifically the value of UltraSpeed.QJDFjPqkSr. If one of the following flags is true, the corresponding method is activated:
- #FTPEnabled: Exfiltration via FTP servers.
- #SMTPEnabled: Exfiltration via email.
- #TGEnabled: Exfiltration via Telegram.
In our ANY.RUN analysis sample, Telegram is identified as the exfiltration method. This can be observed in the process tree within the ANY.RUN sandbox, displayed on the right side of the screen.

Analyze Malware Securely with ANY.RUN Sandbox
The advanced techniques employed by Nova prove the increasing sophistication of modern malware. To combat threats like this effectively, professionals need a reliable and secure platform for detailed analysis. The ANY.RUN Interactive Sandbox offers exactly that—a real-time environment designed to help uncover critical malware behavior, from credential theft methods to data exfiltration tactics.
With its advanced capabilities, ANY.RUN allows security teams to efficiently analyze and respond to emerging threats, ensuring stronger defenses and better-informed strategies.
Start your free 14-day trial today and experience the power of ANY.RUN for professional malware analysis.