dismap v0.4 releases: Asset discovery and identification tool
Dismap – Asset discovery and identification tool
Dismap positioning is an asset discovery and identification tool; its characteristic function is to quickly identify Web fingerprint information and locate asset types. Assist the red team to quickly locate the target asset information, and assist the blue team to find suspected vulnerabilities
Dismap has a comprehensive fingerprint rule library, so you can easily customize new recognition rules. With the help of golang’s concurrency advantages, rapid asset detection and identification can be achieved
The scan results can be directly submitted to vulmap (>=0.8) for vulnerability scanning. Introduction to rule base in RuleLab
Use
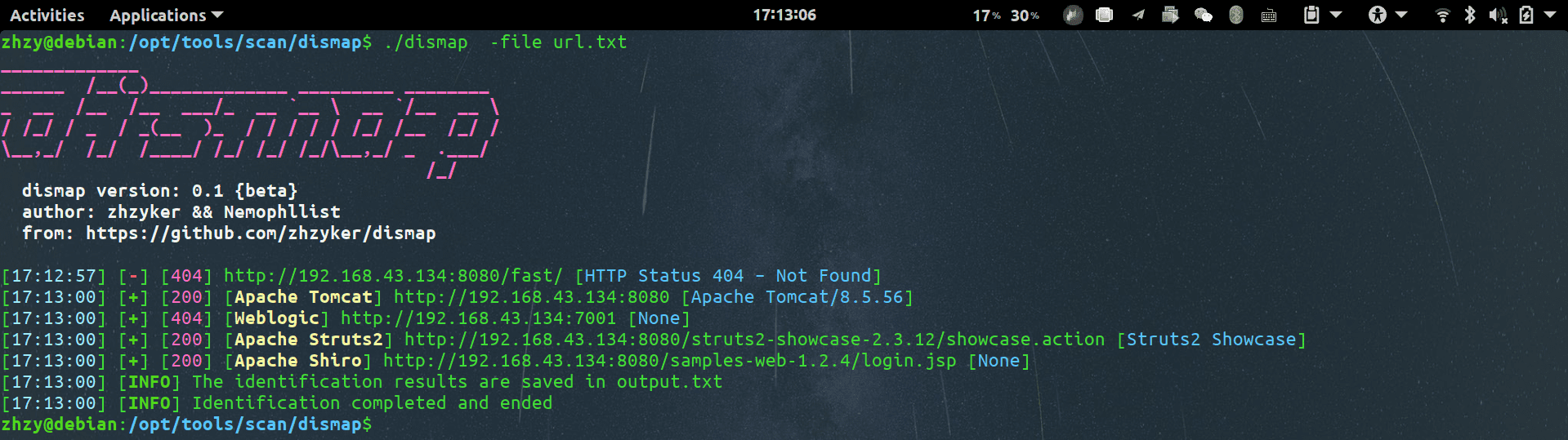
-file string
Select a URL file for batch identification
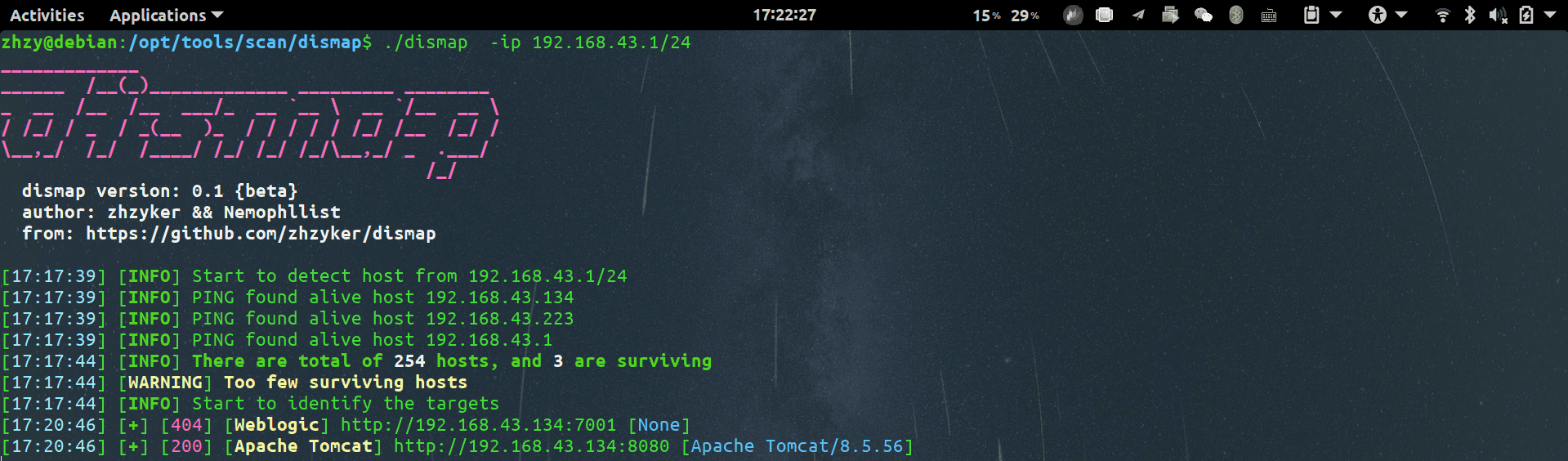
-ip string
Network segment [e.g. -ip 192.168.1.0/24 or -ip 192.168.1.1-10]
-np
Not use ICMP/PING to detect surviving hosts
-output string
Save the scan results to the specified file (default “output.txt”)
-port string
Custom scan ports [e.g. -port 80,443 or -port 1-65535]
-thread int
Number of concurrent threads, (adapted to two network segments 2×254) (default 508)
-timeout int
Response timeout time, the default is 5 seconds (default 5)
-url string
Specify a target URL [e.g. -url https://example.com]
Changelog v0.4
- Optimize concurrency strategy to improve speed (a2a779f)
- Optimize json output (a2a779f) #19
- Added giop protocol identification rules (edcf125)
- Added web fingerprinting rules