DIVULGE STEALER
CYFIRMA has recently exposed a trio of malicious stealers—Divulge, Dedsec, and Duck Stealers—highlighting their proliferation across GitHub, Discord, and Telegram. These stealers, leveraging advanced anti-analysis tactics and targeting sensitive data, are part of a broader trend of “marketplace” malware designed to harvest browser credentials, cryptocurrency wallets, and personal data.
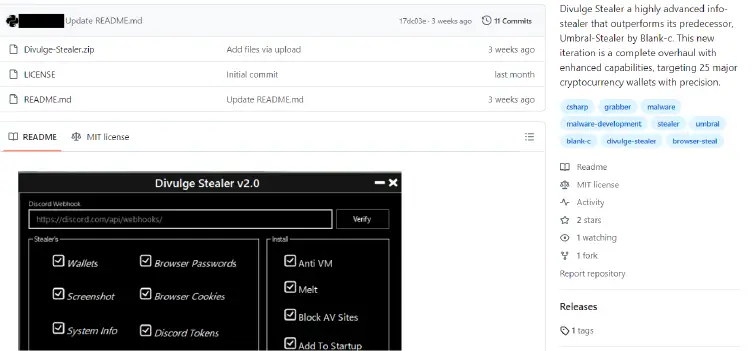
Divulge Stealer has gained traction on underground forums like HackForums, Cracked, and GitHub. Described by threat actors as the successor to Umbral Stealer, it specializes in exfiltrating data from browsers. “The Divulge Stealer is designed to target browser and cookie credentials,” CYFIRMA reported. This stealer’s code features robust anti-VM measures, including checks against blacklisted UUIDs and computer names, such as “john-pc” and “frank,” rendering it particularly difficult for analysts to study its behavior.
Notably, Divulge blocks infected machines from accessing security sites like VirusTotal and Bitdefender by modifying the hosts file, effectively preventing victims from obtaining security solutions.

Unlike Divulge, Dedsec Stealer is primarily promoted on Telegram and GitHub, where it is accessible for download and customization. CYFIRMA’s analysis revealed, “Dedsec Stealer is essentially a copy of Doenerium, a dual-hook stealer,” and is equipped with anti-VM capabilities, making it particularly evasive. This stealer gathers autofill data, payment card details, and credentials from browsers, saving them in a concealed directory at C:/ProgramData/Steam/Launcher/**.
What sets Dedsec apart is its integration of a Base32 encoded clipper designed to intercept and alter cryptocurrency addresses. Upon decoding the string, analysts found regex patterns specifically targeting Bitcoin, Ethereum, and Dogecoin.
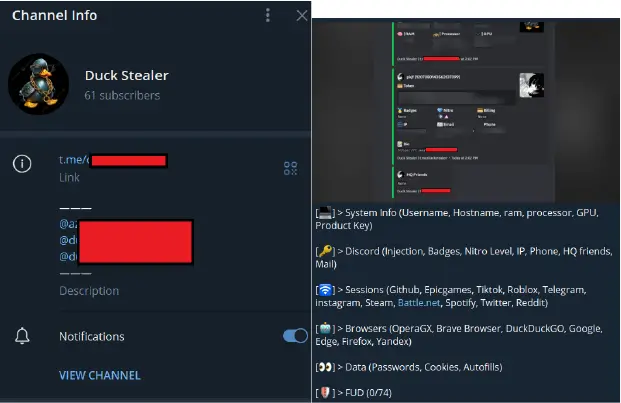
Duck Stealer, which bears a strong resemblance to AZStealer, employs familiar tactics to capture an extensive range of data, from cookies and browsing history to cryptocurrency wallet information. CYFIRMA noted, “The Duck Stealer shares similar functionalities with other stealers discussed in this report,” and supports the theft of over 30 cryptocurrency wallets, including Metamask, Coinbase, and Binance. Enhanced by a clipper function, Duck Stealer allows attackers to intercept cryptocurrency transactions on an even broader scale.
These stealers aren’t simply isolated threats but part of a larger ecosystem of malicious tools thriving on popular platforms. According to CYFIRMA, “Divulge Stealer is primarily promoted on hacker forums and GitHub, while the other two are mainly advertised on GitHub or Telegram.” Developers of these stealers often promote free or trial versions, enabling users to infect systems with malware, which CYFIRMA warns may be dual-hook variants, capable of infecting both the intended targets and the users themselves.
With their advanced evasion techniques and focus on high-value targets, the Divulge, Dedsec, and Duck Stealers signal an escalating threat to cryptocurrency holders and developers. As CYFIRMA concludes, “these malware variants are designed to evade detection and effectively operate in the background,” creating a growing community for their distribution and usage.
Related Posts:
- Domain Takeover: 35,000+ Victims of Sitting Ducks Attack
- Professional Goods & Services at Risk: Decoding CYFIRMA’s Cybersecurity Report
- Cybersecurity firm warns of actively exploited Windows IKE RCE (CVE-2022-34721) flaw
- Mekotio Trojan: A PowerShell-Based Threat Targeting Victims with Stealth and Persistence