DLL Hijack SCanner: assist with the discovery of suitable candidates for DLL Hijacking
DLLHSC
DLL Hijack SCanner – A tool to generate leads and automate the discovery of candidates for DLL Search Order Hijacking.
This repository hosts the Visual Studio project file for the tool (DLLHSC), the project file for the API hooking functionality (detour), the project file for the payload, and last but not least the compiled executables for x86 and x64 architecture (in the release section of this repo). The code was written and compiled with Visual Studio Community 2019.
If you choose to compile the tool from the source, you will need to compile the projects DLLHSC, detour and payload. The DLLHSC implements the core functionality of this tool. The detour project generates a DLL that is used to hook APIs. And the payload project generates the DLL that is used as a proof of concept to check if the tested executable can load it via search order hijacking. The generated payload has to be placed in the same directory with DLLHSC and detour named payload32.dll for x86 and payload64.dll for x64 architecture.
Modes of operation
The tool implements 3 modes of operation which are explained below.
Lightweight Mode
Loads the executable image in memory, parses the Import table, and then replaces any DLL referred in the Import table with a payload DLL.
The tool places in the application directory only a module (DLL) the is not present in the application directory, does not belong to WinSxS, and does not belong to the KnownDLLs.
The payload DLL upon execution creates a file in the following path: C:\Users\%USERNAME%\AppData\Local\Temp\DLLHSC.tmp as proof of execution. The tool launches the application and reports if the payload DLL was executed by checking if the temporary file exists. As some executables import functions from the DLLs they load, error message boxes may be shown up when the provided DLL fails to export these functions and thus meet the dependencies of the provided image. However, the message boxes indicate the DLL may be a good candidate for payload execution if the dependencies are met. In this case, additional analysis is required. The title of these message boxes may contain the strings: Ordinal Not Found or Entry Point Not Found. DLLHSC looks for windows that contain these strings, closes them as soon as they showed up, and reports the results.
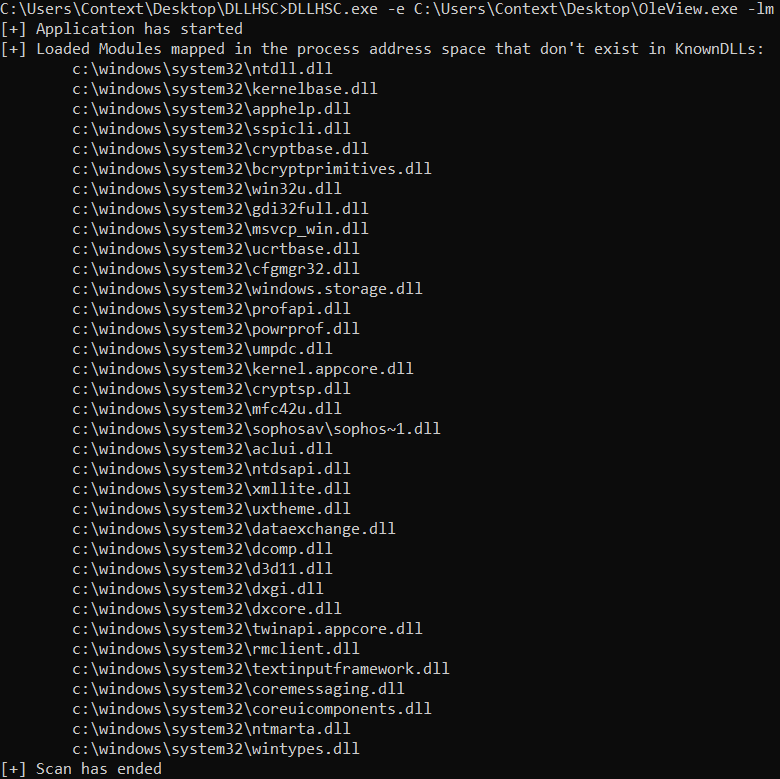
List Modules Mode
Creates a process with the provided executable image, enumerates the modules that are loaded in the address space of this process, and reports the results after applying filters.
The tool only reports the modules loaded from the System directory and does not belong to the KnownDLLs. The results are leads that require additional analysis. The analyst can then place the reported modules in the application directory and check if the application loads the provided module instead.
Run-Time Mode
Hooks the LoadLibrary and LoadLibraryEx APIs via Microsoft Detours and reports the modules that are loaded in run-time.
Each time the scanned application calls LoadLibrary and LoadLibraryEx, the tool intercepts the call and writes the requested module in the file C:\Users\%USERNAME%\AppData\Local\Temp\DLLHSCRTLOG.tmp. If the LoadLibraryEx is specifically called with the flag LOAD_LIBRARY_SEARCH_SYSTEM32, no output is written to the file. After all, interceptions have finished, the tool reads the file and prints the results. Of interest for further analysis are modules that do not exist in the KnownDLLs registry key, modules that do not exist in the System directory and modules with no full path (for these modules loader applies for the normal search order).
Install & Use
Copyright (c) 2020 Context Information Security





