
Cybersecurity researchers from Netskope have uncovered a new side-loaded backdoor, dubbed Yokai, targeting Thai officials through decoy documents and a legitimate application. This campaign highlights the continued use of DLL side-loading to bypass detection and exploit trusted executables.
The attack begins with a malicious RAR archive containing two shortcut (LNK) files disguised as official documents written in Thai. The filenames translate to:
- “United States Department of Justice.pdf”
- “Urgently, United States authorities ask for international cooperation in criminal matters.docx”
Upon execution, these shortcuts trigger the use of esentutl, a legitimate Windows utility often abused by attackers, to extract content hidden in Alternate Data Streams (ADS). Netskope explains: “Clicking the shortcut files triggers the copying of content from an alternate data stream (ADS) named ‘file.exf’ into decoy PDF and Word documents.”
The shortcuts then open decoy documents to maintain the illusion of harmlessness while executing a hidden malicious payload.
The malicious payload, extracted from a second data stream, executes an executable named file.exe, which drops three files into:
C:\ProgramData\police
- IdrInit.exe – A legitimate iTop Data Recovery executable
- ProductStatistics3.dll – The Yokai backdoor
- IdrInit.exe.data – Data used for communication with the attacker’s Command and Control (C2).
Here, IdrInit.exe acts as the loader for the backdoor, abusing DLL side-loading to call a function in the malicious DLL. Netskope states: “Upon execution, IdrInit.exe side-loads the Yokai backdoor (ProductStatistics3.dll) and calls the ‘SetStatParam3’ function… a wrapper around the malicious ‘pfc_init’ function.”
Once active, Yokai demonstrates advanced persistence and communication mechanisms:
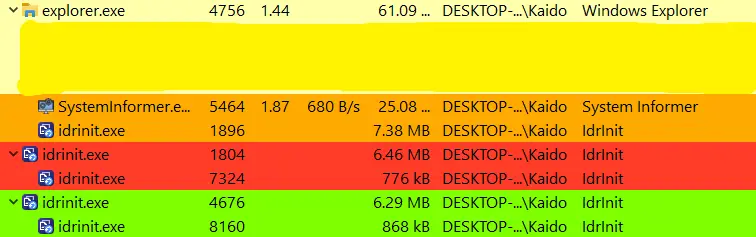
- Scheduled Tasks: When run as a non-admin user, it creates a scheduled task named MicrosoftTSUpdate to re-execute itself every five minutes.
- Process Duplication: As an admin, it repeatedly spawns copies of itself, potentially degrading system performance and increasing detection risk.
Yokai also avoids redundant execution by checking for a mutex named: “Mutex_Local_Windows_1547. If it exists, control returns to IdrInit.exe and it terminates itself.”
Yokai collects key system information, including the username and hostname, formatting the data into a structured block for transmission. The malware uses a simple XOR-based encryption algorithm with a hardcoded key, “ExtensionsWindow,” for both transmission and reception: “The encrypted data is transmitted to the first available C2, which includes IPs like 122.155.28[.]155:80 and 154.90.47[.]77:80.”
The backdoor also supports various C2 commands, including:
- Spawning cmd.exe and executing shell commands.
- Exfiltrating system data.
- Maintaining persistent communication using sequence numbers and encryption keys.
Netskope’s researchers note that the use of sequence numbers ensures reliability in communication and reduces the chance of detection due to errors.
The Yokai backdoor is a clear example of how threat actors continue to exploit trusted software through DLL side-loading. By leveraging legitimate tools like iTop Data Recovery and Windows utilities such as esentutl, attackers can maintain stealth and persistence in targeted systems.
Netskope concludes: “While one of them had a decoy PDF document embedded in its alternate data stream, the other embedded a decoy DOCX document and a malware dropper executable. It dropped a legitimate iTop Data Recovery application along with the side-loaded Yokai backdoor, offering console access to the threat actor.”
As DLL side-loading remains a favored technique, organizations must implement advanced detection mechanisms and monitor for anomalous behaviors like process duplication and suspicious scheduled tasks.
Related Posts:
- Warning: DLL Hijacking in Modern Malware Campaigns
- New Phishing Campaign Utilizes IObit Antivirus to Deliver AsyncRAT Malware
- Researchers Uncovers Sophisticated Phishing Campaigns Leveraging Cloudflare Workers
- Hidden in Plain Sight: Nim Backdoor Lurks, Netskope Exposes Cyber Game
