DLLirant v0.5 releases: automatize the DLL Hijacking research on a specified binary
DLLirant
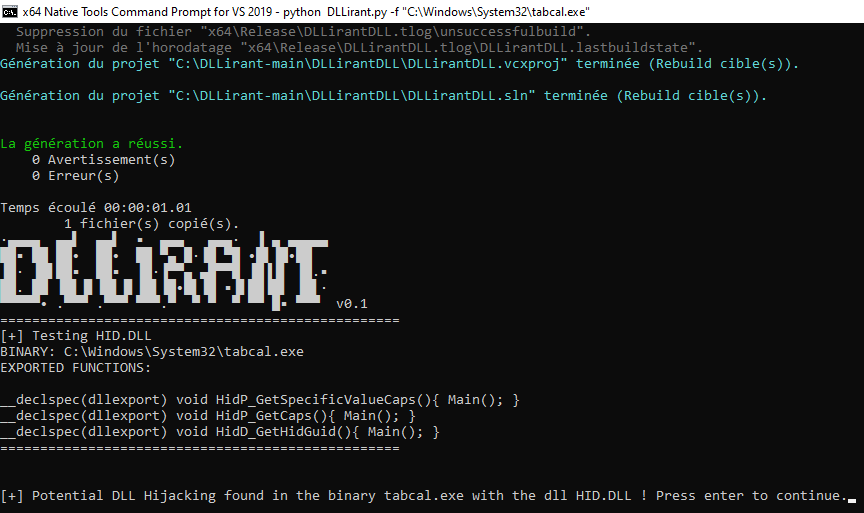
DLLirant is a tool to automatize the DLL Hijacking research on a specified binary.

How it works
The script will create an output directory in the same directory of DLLirant.py, copy the targeted binary to the output directory.
Via the dumpbin tool from Visual Studio, the script will extract the dll names required by the binary, and test each imports functions available one by one by compilate a custom DLL with the required exported functions.
If a function required by the binary is executed, the custom DLL will create a C:\\DLLirant\\output.txt file and display a MessageBox to be sure that a DLL Hijacking is possible.
A results.txt will be also created in the DLLirant directory with all potential DLL Hijacking available.
A file admin-required.txt will also be available for the potential DLL Hijacking who require specific privileges.
If a binary requires a DLL from the system or another one, you can create an import directory in the same directory of DLLirant.py the script will copy all your DLL files in the output directory with your targeted binary.
Download & Use
Copyright (c) 2022 Sh0ckFR





