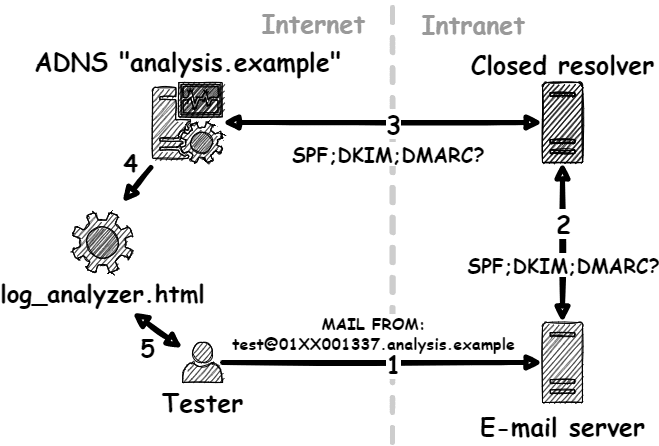
DNS Analysis Server
Tools to assess DNS security.
This is an updated and more generic version of the DNS Reset Checker.
Background
DNS security?
The DNS (Domain Name System) is a central part of the Internet and allows us to, for example, resolve domain names like “google.com” into IP addresses like “142.250.180.206”.
But what happens, if this DNS name resolution is vulnerable?
In this case, an attacker can manipulate the mapping between domain names and associated data. All of a sudden “google.com” could be pointing to “13.33.33.37” instead of Google’s actual IP address.
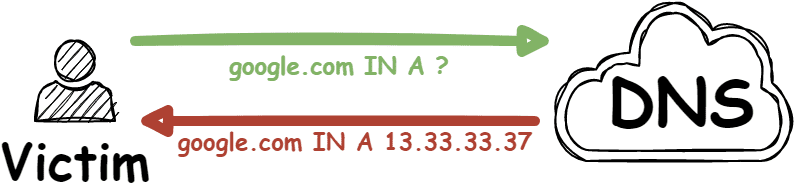
The consequences of such DNS vulnerabilities range from bypassing e-mail spam protections to compromising entire systems. For example, in some cases, it’s possible to take over a fully patched WordPress instance “just” by manipulating the DNS resolution.
Now, to check for vulnerabilities in the DNS name resolution, the DNS Analysis Server comes into play.
A more in-depth look at DNS security and the inner workings of the DNS Analysis Server can be found here and here.
How do I know if a DNS setup is vulnerable?
The various analysis methods of the analysis server check for requirements of DNS attacks.
If all requirements for a DNS attack are fulfilled, the attack should be practically possible.
Currently, the DNS Reset Checker can be used to test for 2 DNS attacks:
- Kaminsky attacks
- IP fragmentation attacks
What exactly are their attack requirements, one might ask. Here’s a summary of some main requirements:
- Kaminsky attacks:
- Low/No random distribution of source ports
- No usage/enforcement of DNS security features (DNS SEC, DNS cookies, 0x20 encoding, etc.)
- IP fragmentation attacks:
- The DNS resolver of the web application accepts IP-fragmented DNS responses
- No usage/enforcement of DNS security features (DNS SEC, etc.)
- Maximum EDNS buffer size larger than 1232
For example, if the DNS infrastructure is vulnerable to Kaminsky attacks, you might see the following scatter plot via the log analyzer:
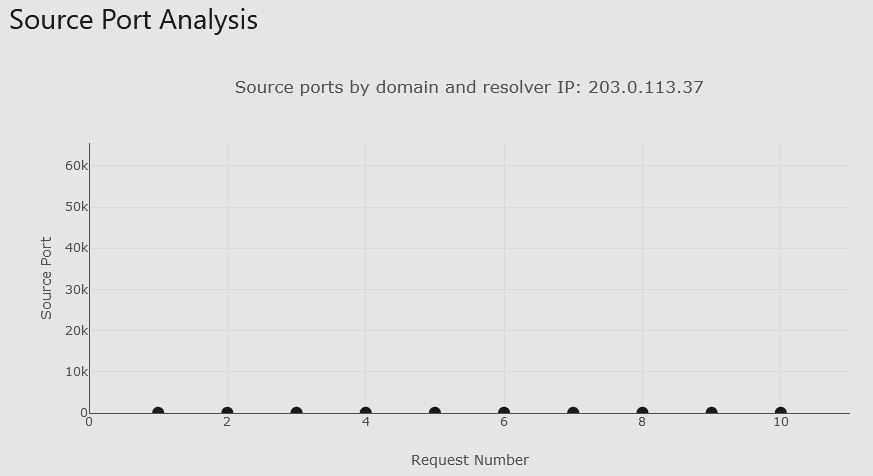
In this case, only port 53 was used as the source port by the DNS resolver.
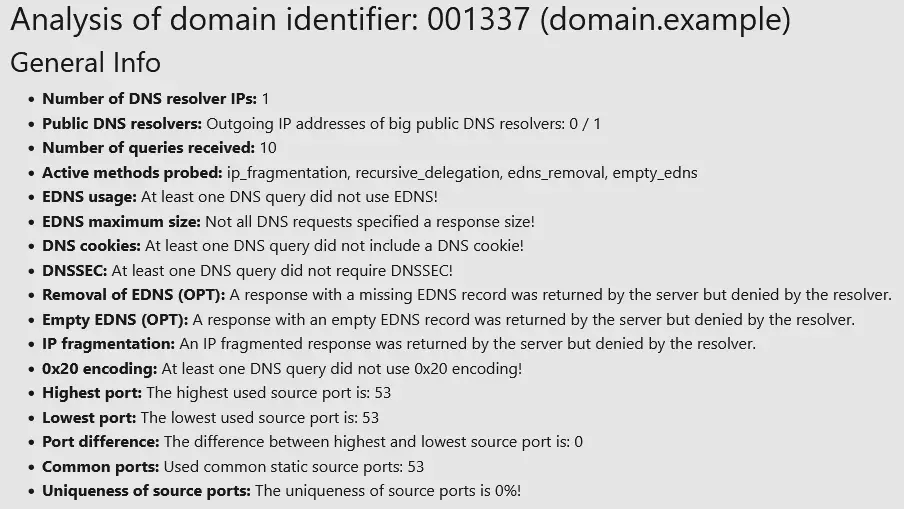
The other requirements mentioned can be checked by reading the “General Info” section of the log analyzer output or by analyzing the dns_log.txt log entries directly.
As already mentioned, for a more in-depth look at this topic check out this and this blog post.
Install & Use
Copyright (c) 2022 Login