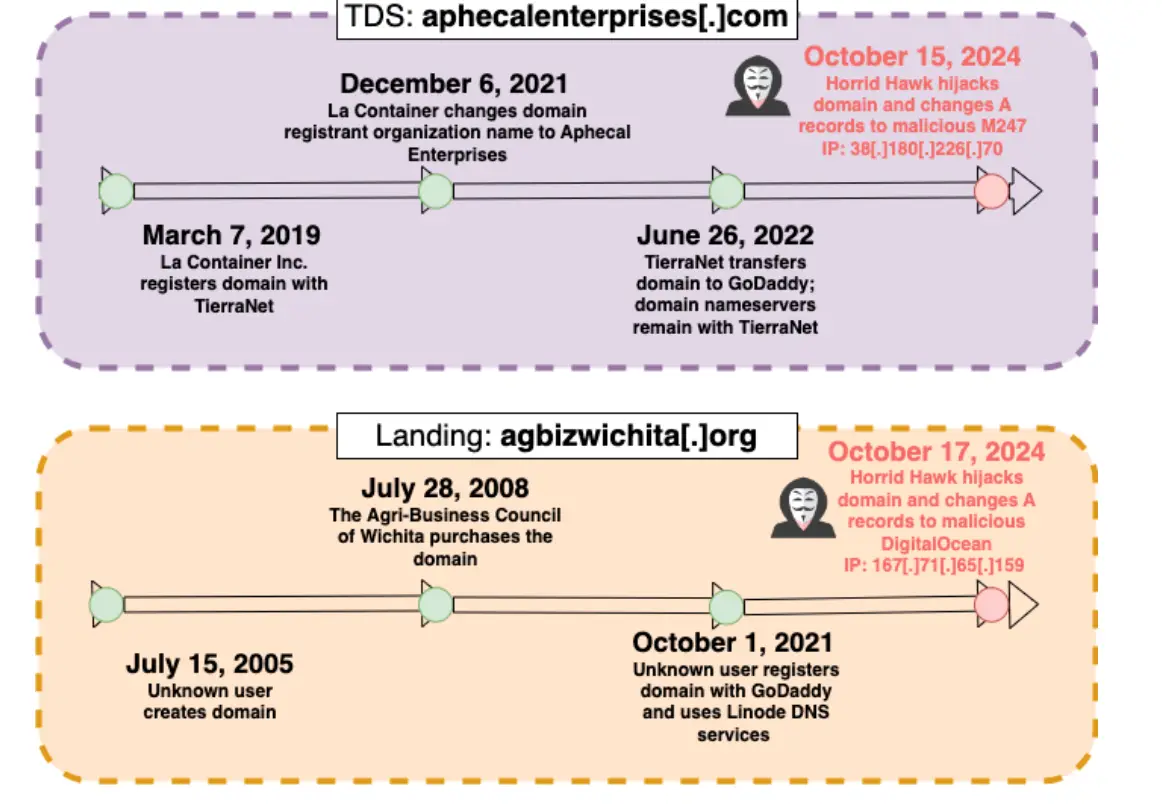
Domain hijacking timeline of aphecalenterprises[.]com (TDS) and agbizwichita[.]org (landing page domain) | Image: Infoblox
A recent report from Infoblox Threat Intel sheds light on an underreported yet pervasive cyber threat: the “Sitting Ducks” attack, a domain hijacking technique that has enabled cybercriminals to weaponize trusted domains for malicious campaigns. The report estimates that over 1 million domains are potentially vulnerable, with 70,000 already confirmed hijacked. This attack vector has been exploited by multiple threat actors, each using hijacked domains to fuel phishing, malware, and fraud schemes.
“Hijacking domains using a ‘Sitting Ducks attack’ remains an underreported topic in the cybersecurity community,” states the report. “However, the prevalence of these attacks and the risk to organizations are much broader than initially reported.”
The “Sitting Ducks” attack preys on a vulnerability known as “lame delegation,” where a domain’s name server points to an incorrect authoritative name server. This misconfiguration allows attackers to seize control of the domain and its DNS records.
“Once a victim domain is compromised,” the report warns, “it allows the actors to set up attack infrastructure capable of evading existing detections. The positive reputation of the hijacked domains enables them to be seen by security controls as safe or benign, which then allows users to connect to the compromised and weaponized site.”
Infoblox’s research uncovered alarming statistics: over 800,000 vulnerable domains were identified, with approximately 70,000 already hijacked. These compromised domains are then weaponized for various malicious purposes, including:
- Malicious Traffic Distribution: Threat actors, such as the “Vacant Viper” group, leverage hijacked domains to bolster their traffic distribution systems, spreading malware, spam, and other malicious content.
- Phishing Campaigns: Actors like “Hasty Hawk” utilize hijacked domains to host convincing phishing pages, often mimicking legitimate brands like DHL or charitable organizations.
- Investment Fraud: The “Horrid Hawk” group employs hijacked domains in elaborate investment fraud schemes, luring victims with promises of lucrative government programs.
The Infoblox report emphasizes the ease with which these attacks can be executed and the difficulty in detecting them. The lack of official recognition for “lame delegation” as a vulnerability further contributes to the problem.
The report concludes with a call to action, urging domain holders, registrars, and DNS providers to take proactive steps to prevent “Sitting Ducks” attacks. Proper configuration and vigilance are crucial in mitigating this growing threat.
Related Posts:
- Domain Takeover: 35,000+ Victims of Sitting Ducks Attack
- Unit 42 Research Exposes GootLoader’s Sophisticated Sandbox Evasion Tactics
- Divulge, Dedsec, and Duck: The Rise of Advanced Stealer Malware