
Cyber attackers are increasingly exploiting DNS tunneling as a covert means to conduct malicious activities, evade detection, and exfiltrate data. Palo Alto Networks‘ latest report highlights emerging threats and campaigns utilizing DNS tunneling techniques that evade traditional security measures. DNS, a cornerstone of the internet, is often left unmonitored, making it a prime target for attackers. According to the report, “DNS tunneling leverages the DNS protocol to encode data within DNS queries and responses,” allowing attackers to bypass security systems unnoticed.
The report explains that attackers first infect a client system with malware capable of stealing sensitive data. Once compromised, the data is embedded within subdomains and transmitted through DNS queries. This malicious communication is routed through recursive DNS servers, indirectly connecting infected devices with attacker-controlled authoritative DNS (aDNS) servers. As the report states, “DNS tunneling can achieve stealthiness because recursive DNS servers enable indirect communications between client systems and attacker-controlled authoritative DNS servers.”
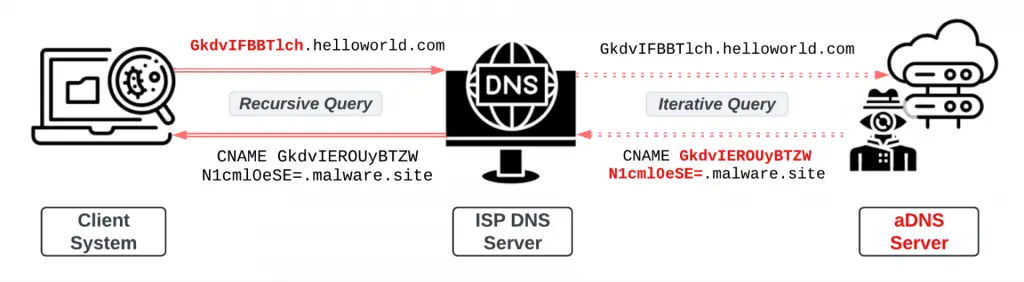
Notably, Palo Alto Networks uncovered four new campaigns leveraging DNS tunneling, each with unique methods for payload delivery, infrastructure management, and targeting.
1. FinHealthXDS: Targeting Finance and Healthcare
One of the most sophisticated campaigns identified is FinHealthXDS, which used 12 domains to deliver commands via a customized DNS beaconing format for Cobalt Strike, a popular penetration testing tool often misused by attackers. The report highlights how the campaign exploits DNS A records and TXT records to exfiltrate data from finance and healthcare organizations. “In this campaign, attackers use the xds prefix to indicate command request queries and transmit malware instructions using customized DNS query formats.”
2. RussianSite: Targeting Education and Government
The RussianSite campaign stood out for its wide use of over 100 domains, all leveraging the same Russian IP address (185.161.248[.]253). Targeting sectors such as higher education, government, and public infrastructure, this campaign utilized consistent DNS configurations and domain registration patterns, which facilitated its detection. The campaign’s reliance on a centralized DNS infrastructure enabled efficient management of its tunneling operations.
3. 8NS: Trojan-Driven Attacks
The 8NS campaign demonstrated how malware such as the Hiloti trojan can exploit DNS tunneling for persistent communication. All six domains used in this campaign shared the same DNS configurations and a DNS server IP address (35.205.61[.]67), underscoring how attackers achieve redundancy and control with consistent infrastructure. The report also details the campaign’s “use of eight NS records with identical A records, a unique pattern that aided in identifying this tunneling campaign.”
4. NSfinder: Luring Victims with Fake Websites
The final campaign, NSfinder, exploited over 50 domains, all of which followed a consistent naming pattern combining three-word phrases with the word “finder.” This campaign targeted victims through fake websites designed to lure users into entering sensitive information, such as credit card details. The attackers behind NSfinder also used malware like IcedID to steal data and inject malicious code. The report concludes that “the ns500 tokens found in the campaign provide a unique fingerprint for tracking future attacks.”
The DNS tunneling threat continues to evolve, and Palo Alto Networks’ detection methods highlight the importance of identifying correlations between tunneling domains. By focusing on attributes such as DNS configurations, payload encoding, and domain registration, security teams can detect new campaigns and protect critical infrastructures. The discovery of campaigns like FinHealthXDS, RussianSite, 8NS, and NSfinder is just the beginning. As the report states, “These attributes enable us to identify significant clusters among the tunneling detection results so that we can discover the emerging tunneling campaigns.”
Related Posts:
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- Fake Palo Alto Tool Delivers Sophisticated Malware in Middle East Cyberattack
- A New Set of Tools for Cyber Espionage: Targeting the Middle East, Africa, and the US