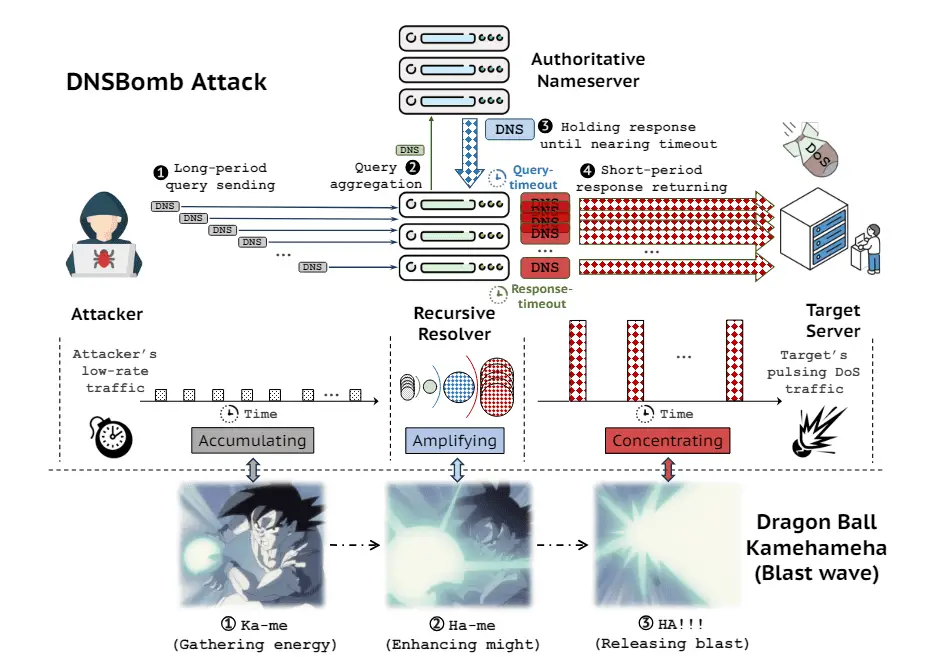
Researchers from Tsinghua University have unveiled a potent new method for launching distributed denial-of-service (DDoS) attacks, dubbed DNSBomb (CVE-2024-33655). This innovative attack weaponizes DNS (Domain Name System) traffic to overwhelm and disrupt online services, marking a significant evolution in the DDoS landscape.

DNSBomb cleverly repurposes a two-decade-old attack concept: the TCP pulse attack. These attacks utilize short, intense bursts of traffic to degrade or disable target systems. DNSBomb takes this strategy to the next level by exploiting modern DNS software and infrastructure.
By sending a steady stream of specially crafted DNS queries, attackers can trigger a cascading effect that amplifies the traffic exponentially. This results in a massive pulse of DNS data that floods the target, causing significant disruptions to services relying on DNS resolution – which is practically everything on the internet.
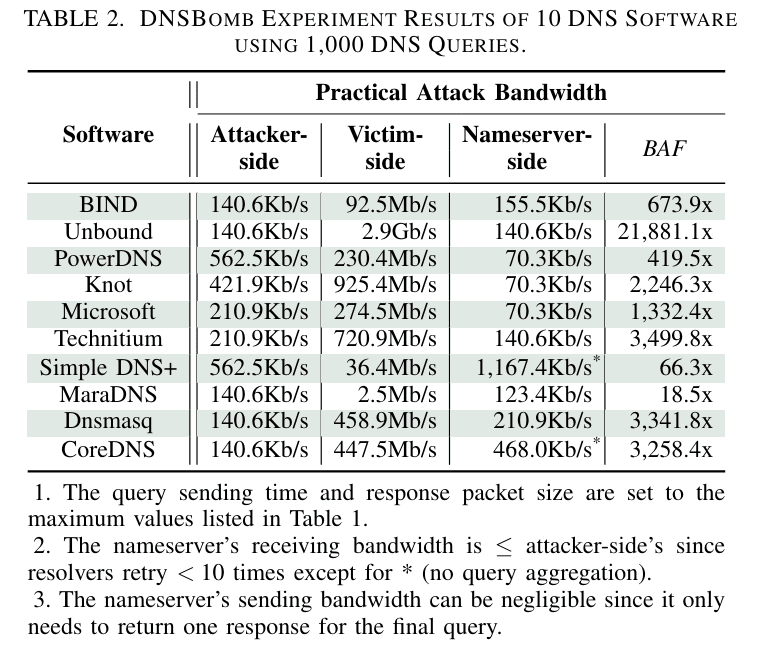
In their tests, researchers deployed DNSBomb against 10 common DNS programs and 46 public DNS services. They achieved an attack power of up to 8.7 Gbps, with the initial DNS traffic amplified by a staggering 20,000 times its original size. The attack results in complete packet loss or significant degradation of service quality on both stateless and stateful connections (TCP, UDP, and QUIC).
The study authors highlighted that any system or mechanism capable of aggregation, such as DNS and Content Delivery Networks (CDNs), can be exploited to create pulsing DoS traffic. The gravity of this new attack method has prompted immediate action.
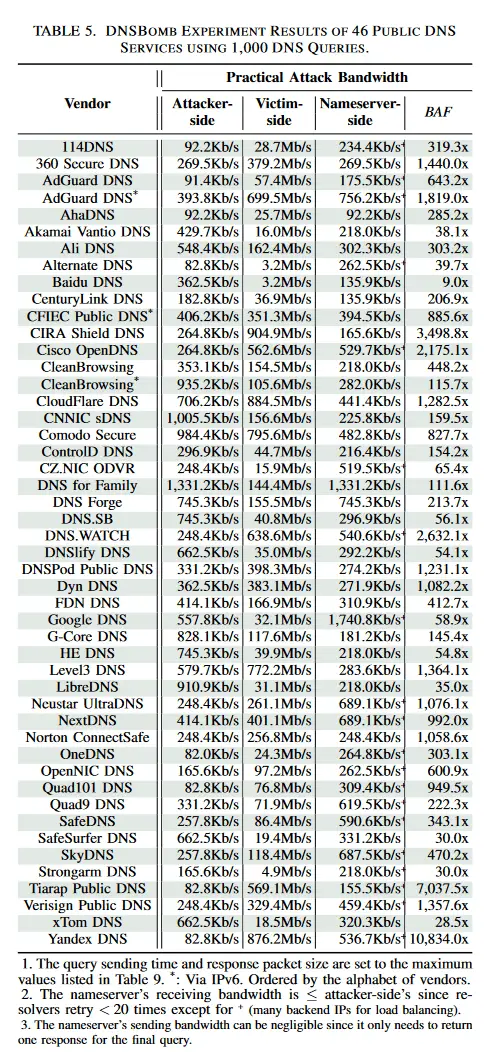
The scientists have alerted all affected parties, with 24 organizations already working on fixes or having released patches. Among the impacted entities are some of the world’s leading DNS providers. The DNSBomb issue has been assigned the primary CVE identifier CVE-2024-33655, along with several other identifiers related to specific DNS solutions:
- Knot: CVE-2023-49206
- Simple DNS Plus: CVE-2023-49205
- Technitium: CVE-2023-28456, CVE-2023-49203
- MaraDNS: CVE-2023-49204
- Dnsmasq: CVE-2023-28450, CVE-2023-49207
- CoreDNS: CVE-2023-28454, CVE-2023-49202
- SDNS: CVE-2023-49201
For those seeking more detailed information, the researchers plan to disclose their findings at the IEEE Symposium on Security & Privacy, which is being held in San Francisco this week. This event will provide a platform for a deeper dive into the technicalities of DNSBomb and the necessary countermeasures to mitigate this sophisticated DDoS threat.