
The security company Doctor Web is issuing a warning to all computer users saying that a new type of Trojan horse is spreading through YouTube. The Trojan is designed to steal files and other sensitive information from infected computers, and the attacker can use this information to hijack victims’ social networking sites or other online service accounts.
This Trojan was detected by Doctor Web as Trojan.PWS.Stealer.23012. It was developed using the Python programming language. The target of infection is a computer running Windows operating system.
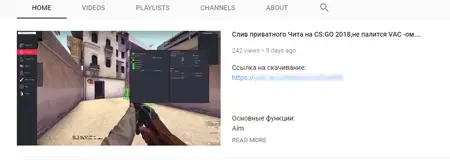
Doctor Web said that the distribution of the Trojan horse began on March 23, 2018, and continues to this day. The link for downloading malicious applications was published by the attacker in the comment section of the YouTube video, and most of the videos were content promoting the “plug-in” of a game.
In fact, this is a popular and commonly used method of malware distribution. The content of the YouTube video is mainly used to demonstrate the specific effects of using “plug-ins” in these games. For most gamers, this is undoubtedly full of allure.
According to Doctor Web, the malicious link points to the Yandex.Disk server (a disk drive from Russia) from which victims can download a .rar compressed file. There is no doubt that the aforementioned Trojan Trojan.PWS.Stealer.23012 is included. In order to persuade the victim to click on the link, the attacker also creates a number of fake YouTube accounts to post “praise.”
DoctorWeb stated that Trojan.PWS.Stealer.23012 will collect the following information after it is started on the infected computer:
- cookies stored by the Vivaldi, Chrome, YandexBrowser, Opera, Kometa, Orbitum, Dragon, Amigo, and Torch browsers;
- saved logins/passwords from the same browsers;
- screenshot.
In addition, it also dumps files containing the following extensions from the Windows desktop, including .txt, .pdf, .jpg, .png, .xls, .doc, .docx, .sqlite, .db, .sqlite3, . Bak, .sql, and .xml.
After completing the information collection, Trojan.PWS.Stealer.23012 will save all the collected information to the C:/PG148892HQ8 folder and then package and compress it into a file named “spam.zip”. It will eventually be sent to the server controlled by the attacker.
Source, Image: Dr.Web