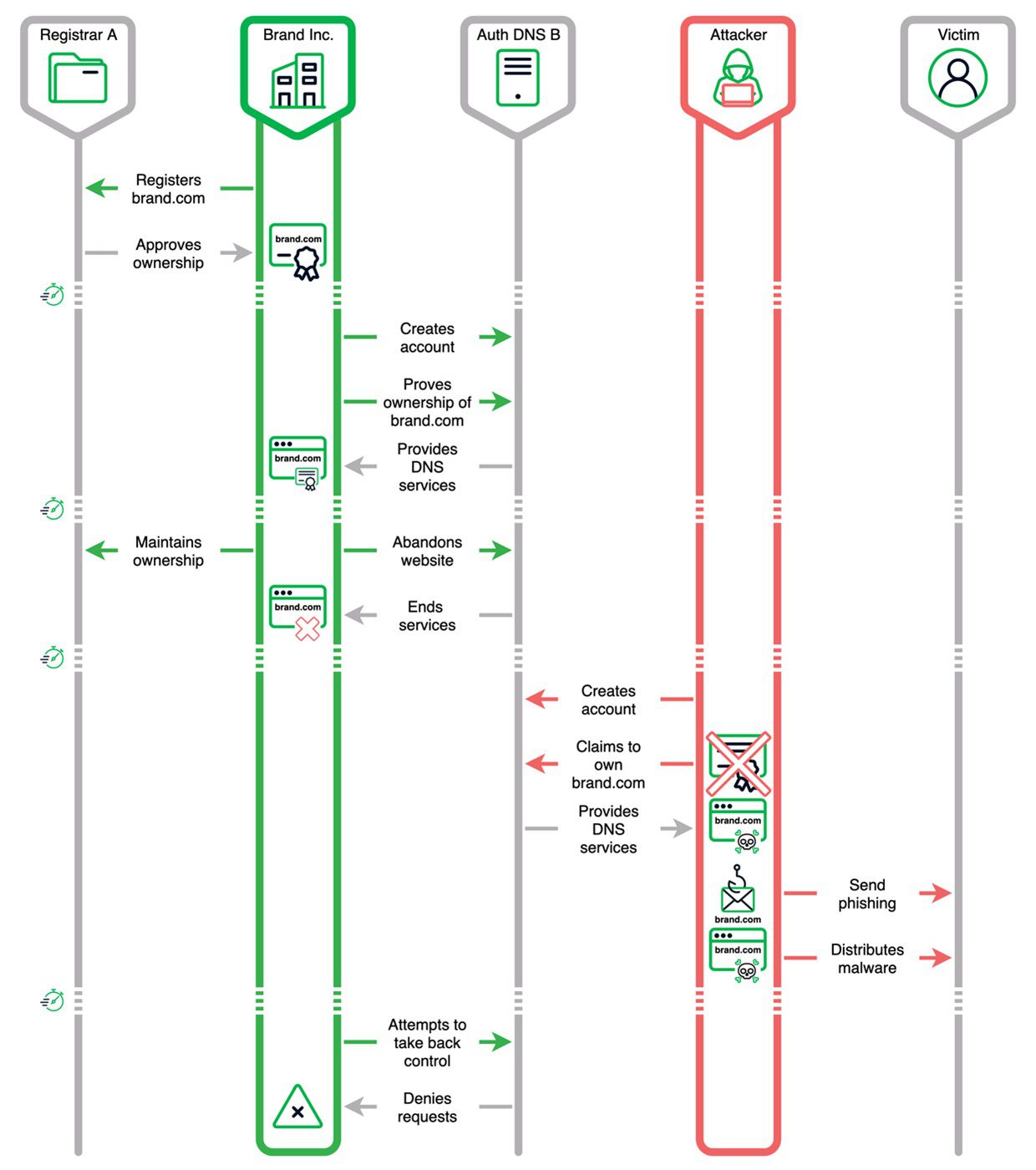
Cybercriminals have seized over 35,000 registered domains using an attack researchers have dubbed “Sitting Ducks.” This method allows attackers to capture domains without accessing the owner’s account with the DNS provider or registrar.
In the Sitting Ducks attack, cybercriminals exploit configuration flaws at the registrar level and insufficient ownership verification by DNS providers. Researchers from Infoblox and Eclypsium have identified that this attack method could potentially compromise over a million domains daily.
Numerous cybercriminal groups have employed this method for years to disseminate spam, perpetrate fraud, deliver malware, conduct phishing, and steal data. The issue was first documented in 2016 by Matthew Bryant, a security engineer at Snap.
Several conditions must be met for the attack to succeed: the domain must use or delegate authoritative DNS services to a provider different from the registrar; the authoritative DNS server must be incapable of resolving requests; and the DNS provider must allow domain claims without ownership verification.
When these conditions are met, attackers can seize the domain. Variations of the attack include partially incorrect delegation and redirection to another DNS provider. If the DNS services or web hosting for the target domain expire, the attacker can claim the domain by creating an account with the DNS provider.
Infoblox and Eclypsium have observed numerous instances of Sitting Ducks exploitation since 2018 and 2019. During this period, more than 35,000 domain takeovers have been recorded using this method. Typically, cybercriminals held the domains for a short duration, but in some cases, domains remained under the attackers’ control for up to a year.
Several hacker groups are known to use this attack:
- Spammy Bear — seized GoDaddy domains in late 2018 for spam distribution.
- Vacant Viper — has annually captured around 2,500 domains since December 2019 for the 404TDS system, which spreads IcedID and creates C2 domains for malware.
- VexTrio Viper — has used domains since early 2020 for a mass traffic distribution system aiding SocGholish and ClearFake operations.
Some domains were successively captured by multiple groups, using them for phishing, spam distribution, and creating malware distribution networks.
Domain owners are advised to regularly check their DNS configurations for incorrect delegations, especially for older domains. Registrars, in turn, should conduct proactive checks and notify owners of issues. Regulators and standardization bodies must develop long-term strategies to address DNS vulnerabilities and require DNS providers to take active measures to mitigate the risk of Sitting Ducks attacks.
Related Posts:
-
Chinese Hackers Accused of Spying on German Cartography Agency
-
Apple Open-Sources Homomorphic Encryption for Enhanced Data Security