domainhunter: Checks expired domains, bluecoat categorization, and Archive.org history
Domain Hunter
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used previously for benign purposes and were properly categorized can be purchased for only a few dollars. Such domains can allow a team to bypass reputation based web filters and network egress restrictions for phishing and C2 related tasks.
This Python-based tool was written to quickly query the Expireddomains.net search engine for expired/available domains with a previous history of use. It then optionally queries for domain reputation against services like Symantec WebPulse (BlueCoat), IBM X-Force, and Cisco Talos. The primary tool output is a timestamped HTML table style report.
Features
- Retrieve the specified number of recently expired and deleted domains (.com, .net, .org primarily) from ExpiredDomains.net
- Retrieve available domains based on keyword search from ExpiredDomains.net
- Perform reputation checks against the Symantec WebPulse Site Review (BlueCoat), IBM x-Force, Cisco Talos, Google SafeBrowsing, and PhishTank services
- Sort results by domain age (if known)
- Text-based table and HTML report output with links to reputable sources and Archive.org entry
Report Header Reference
- Domain: Target Domain
- Birth: First seen on Archive.org
- Entries: Number of entries in Archive.org
- TLDs Available: Top level top available
- Bluecoat Categorization: Bluecoat category
- IBM-xForce Categorization: IBM-xForce category
- WatchGuard: Watchguard reputation
- Namecheap: Link to namecheap.com
- Archive.org: Link to archive.org
Installation
git clone https://github.com/threatexpress/domainhunter.git
pip3 install -r requirements.txt
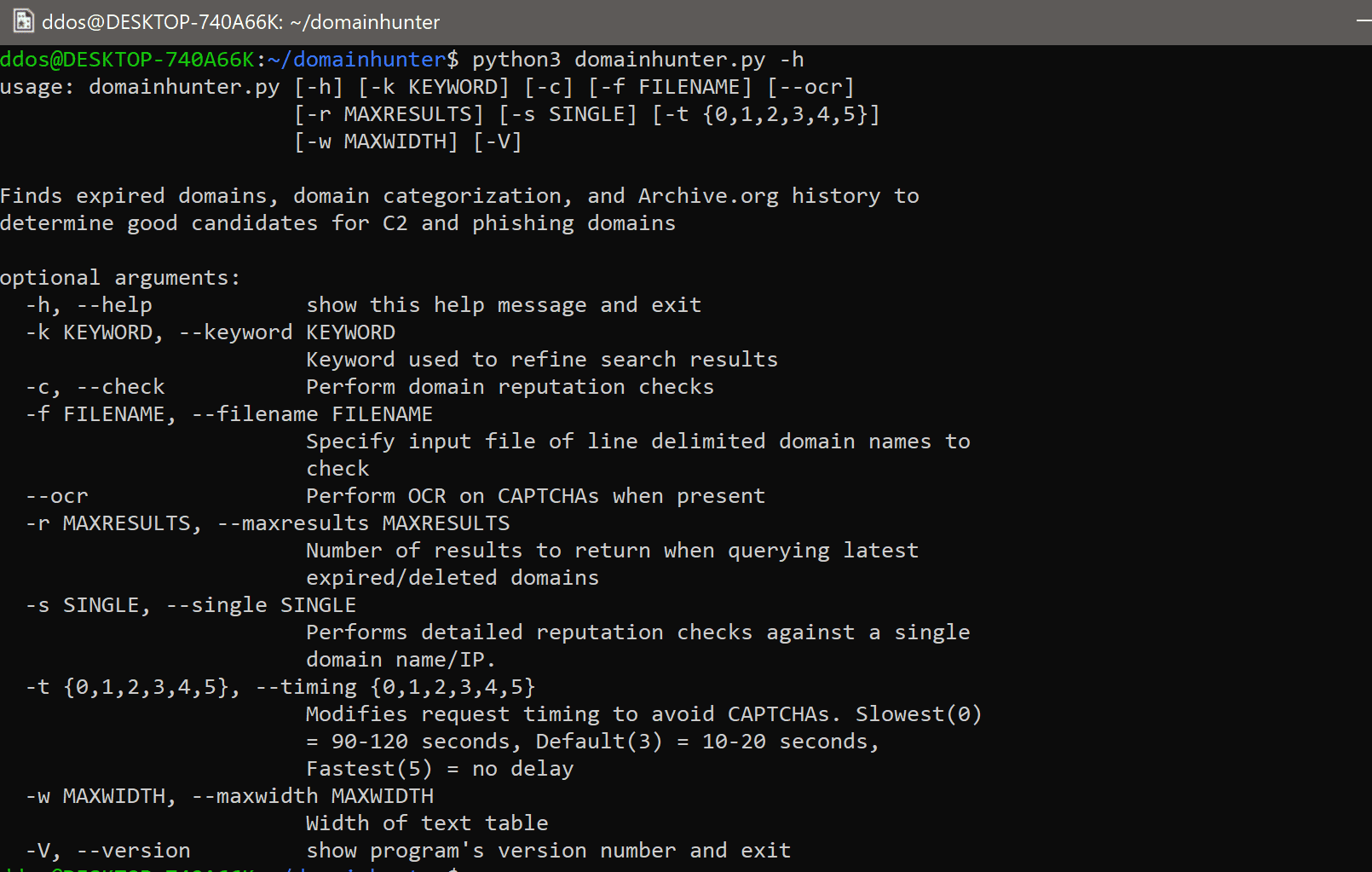
Usage
Copyright (c) 2017, Joe Vest, Andrew Chiles
All rights reserved.
Source: https://github.com/threatexpress/





