DONOT APT Group Targets Pakistan’s Maritime and Defense Sectors in New Campaign
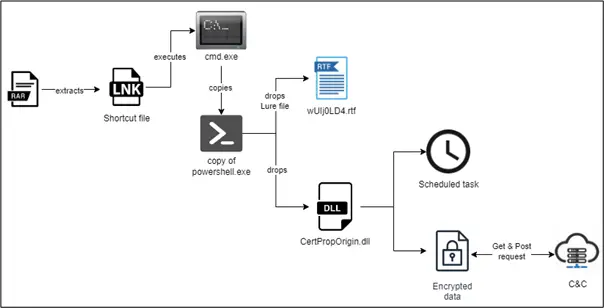
A recent report from Cyble Research and Intelligence Labs (CRIL) has exposed a new campaign orchestrated by the Advanced Persistent Threat (APT) group DONOT, also known as APT-C-35. This campaign targets Pakistan’s maritime and defense manufacturing sectors with an arsenal of advanced tactics, including malicious .LNK files and enhanced encryption methods.
DONOT, active since 2016, is notorious for targeting government and military entities across South Asia. In this latest campaign, the group has shifted its initial infection vector from malicious Office files to .LNK files disguised as Rich Text Format (RTF) documents. These files, often delivered via spam emails, lure victims into triggering a chain of malicious activities.
“When the user clicks to execute, it triggers cmd.exe and powershell.exe to run additional malicious commands,” CRIL’s report notes. This process loads a stager DLL malware, establishes persistence via scheduled tasks, and communicates with a Command and Control (C&C) server to execute further actions.
The campaign appears to focus on Pakistan’s manufacturing industry, particularly companies linked to maritime and defense operations. For example, one lure document impersonates Karachi Shipyard & Engineering Works, a prominent defense contractor. By exploiting sector-specific themes, DONOT APT group aims to infiltrate critical organizations supporting national security.
The group’s approach demonstrates a significant evolution in their tactics:
- Dynamic Encryption:
Unlike previous campaigns that relied on simple XOR keys, this operation employs advanced encryption methods to obfuscate payloads and evade detection. - Scheduled Persistence:
A scheduled task ensures the stager DLL runs every five minutes, maintaining a foothold on infected systems. - C&C Communication:
The malware communicates with its primary server using encrypted POST requests, transmitting unique device identifiers and configuration data. A randomly generated backup domain serves as a fallback for C&C communication. - System Reconnaissance:
Before delivering additional payloads, the malware collects detailed system information, including disk space and installed security software, to optimize its attack.
The campaign showcases DONOT’s adaptability. “The shift in how decryption keys are handled and the collection of system information before payload delivery indicate a more sophisticated approach,” the report emphasizes.
CRIL has released a comprehensive threat-hunting package, including YARA and Sigma rules, to help organizations detect and mitigate this campaign. These tools are crucial for identifying the malicious PowerShell commands and suspicious scheduled tasks employed by DONOT.




