
Image: Ironscales
In 2024, phishing attacks have taken on a new and dangerous form, utilizing Rich Text Format (RTF) files in creative and highly deceptive ways. According to a recent report by Audian Paxson from IRONSCALES, there has been a significant increase in phishing campaigns using RTF files, with over 6,755 attacks detected and blocked in March alone. But what makes these attacks particularly dangerous is the combination of outdated file formats and tricks designed to fool even the most security-conscious users.
These phishing attacks typically present themselves as businesslike emails, often disguised as invoice reconciliations. What sets them apart is the personalization of the file names, which are customized to match the recipient’s domain. This simple detail gives the victim a false sense of security. As Paxson explains, “the assumption that an attachment bearing their organization’s domain name must be safe” is exactly what attackers are exploiting.
Once the recipient opens the attached RTF file, they are met with a cleverly hidden threat. Inside these files lies a URL, often disguised to appear as though it’s leading to a trusted domain like microsoft.com. However, by using the @ symbol, attackers trick the recipient into clicking a malicious link. For instance, a URL like https://microsoft.com@malicious-site.com/invoice.pdf won’t take the victim to Microsoft’s website—it redirects them to a dangerous, malware-laden destination.
Paxson highlights three main tactics used by attackers in these campaigns:
- RTF File Use: Attackers are leveraging the RTF format, which has been around for decades and doesn’t trigger the same red flags as other attachment types like .exe or .zip files. Many email security filters overlook RTF files, allowing these phishing emails to slip through.
- Attachment Personalization: By including the target company’s domain name in the file name, attackers create a false sense of legitimacy. Victims are more likely to open these files, believing they are safe.
- URL Obfuscation with the @ Symbol: Attackers use the @ symbol to create a seemingly legitimate URL, tricking users into clicking on it. The actual destination, however, is a malicious website.
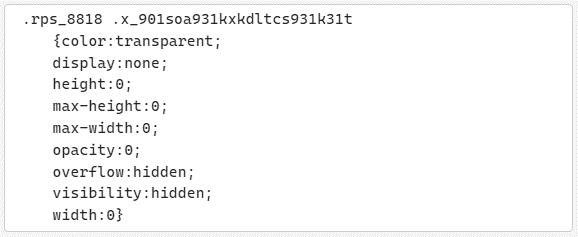
What makes these phishing attacks even more dangerous is the use of hidden CSS and obfuscation techniques. Attackers are embedding invisible text into emails using CSS properties like display: none and color: transparent, making the content harder for security filters to detect. Zero-width spaces, which are invisible to the user but break up important text strings, further confuse automated detection systems. As Paxson notes, “this invisible text doesn’t show up for the recipient but exists in the email’s HTML, where it can help attackers bypass security filters.”
Paxson recommends several best practices:
- Train Employees: Ensure that staff members are trained to spot suspicious file names and check URLs for unusual characters like the @ symbol.
- Don’t Trust File Names Alone: Attackers are exploiting the use of domain names in file attachments to make them appear legitimate. Always verify with the sender before opening any unexpected attachments.
- Be Cautious with RTF Files: RTF files are rarely used in modern workflows. If you receive one, especially in an unexpected context, approach with caution
Related Posts:
- Microsoft Warns of Sophisticated Identity Phishing Campaigns Misusing File Hosting Services
- Exploit toolkit CVE-2017-8759: Microsoft .NET Framework RCE