dr_checker: Soundy Vulnerability Detection Tool for Linux Kernel Drivers
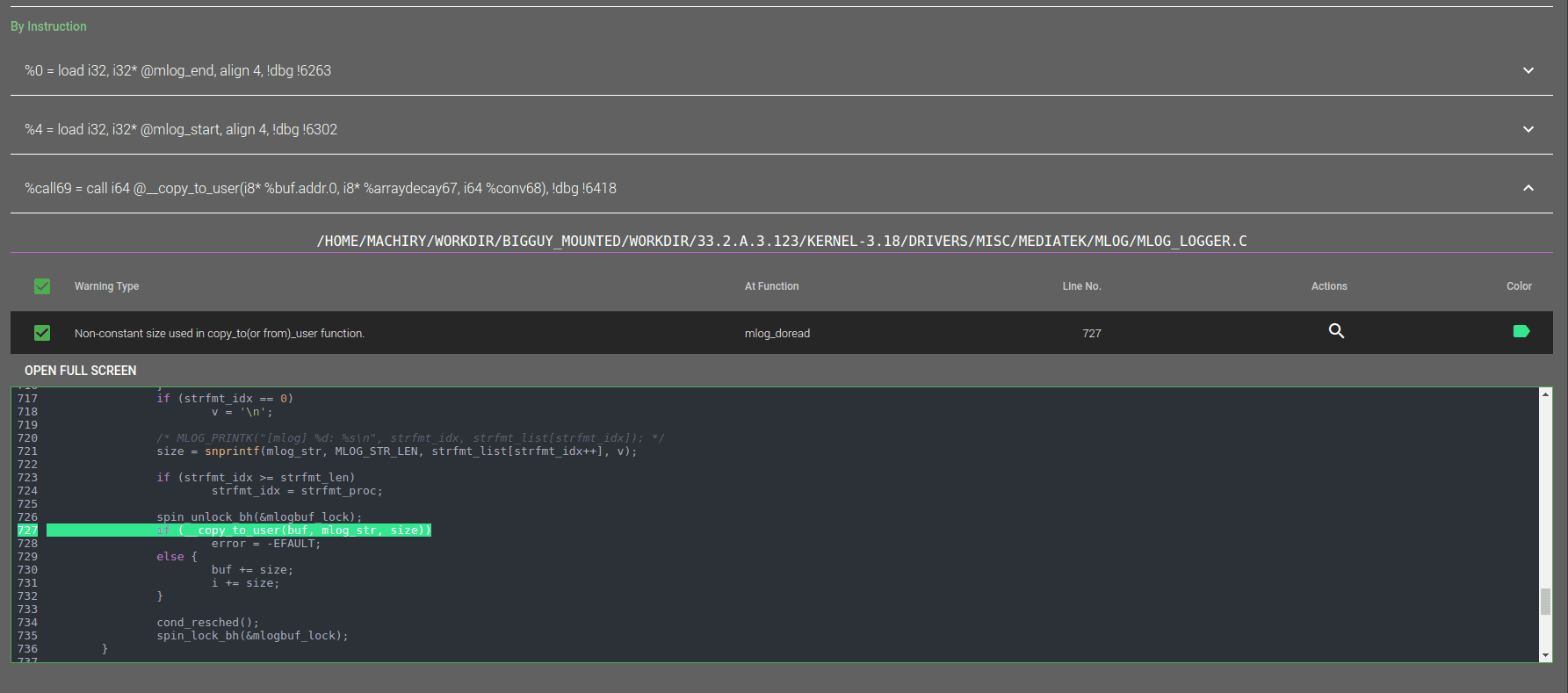
DR.CHECKER: A Soundy Vulnerability Detection Tool for Linux Kernel Drivers

1. Setup
Our implementation is based on LLVM, specifically LLVM 3.8. We also need tools like c2xml to parse headers.
First, make sure that you have libxml (required for c2xml):
sudo apt-get install libxml2-dev
Clone the repo:
git clone https://github.com/ucsb-seclab/dr_checker.git
Next, We have created a single script, which downloads and builds all the required tools.
2. Building
This depends on the successful completion of Setup. We have a single script that builds everything, you are welcome.
3. Running
This depends on the successful completion of Build. To run DR.CHECKER on kernel drivers, we need to first convert them into llvm bitcode.
3.1 Building kernel
First, we need to have a buildable kernel. Which means you should be able to compile the kernel using regular build setup. i.e., make. We first capture the output of make command, from this output we extract the exact compilation command.
3.1.1 Generating output of make (or makeout.txt)
Just pass V=1 and redirect the output to the file. Example:
NOTE: DO NOT USE MULTIPLE PROCESSES i.e., -j. Running in multi-processing mode will mess up the output file as multiple process try to write to the output file.
That’s it. DR.CHECKER will take care from here.
3.2 Running DR.CHECKER analysis
There are several steps to run DR.CHECKER analysis, all these steps are wrapped in a single script helper_scripts/runner_scripts/run_all.py How to run:
The script builds, links and runs DR.CHECKER on all the drivers, as such might take considerable time(45 min-90 min). If you want to run DR.CHECKER manually on individual drivers, refer standalone
Tutorial
Copyright (c) 2015, The Regents of the University of California
Source: https://github.com/ucsb-seclab/