DRAKVUF v1.0 releases: Black-box Binary Analysis
DRAKVUF
Introduction
It is a virtualization-based agentless black-box binary analysis system. DRAKVUF allows for in-depth execution tracing of arbitrary binaries (including operating systems), all without having to install any special software within the virtual machine used for analysis.
Hardware requirements
DRAKVUF uses hardware virtualization extensions found in Intel CPUs. You will need an Intel CPU with virtualization support (VT-x) and with Extended Page Tables (EPT). DRAKVUF is not going to work on any other CPUs (such as AMD) or on Intel CPUs without the required virtualization extensions.
Supported guests
- Windows 7 – 8, both 32 and 64-bit
- Windows 10 64-bit
- Linux 2.6.x – 4.x, both 32-bit and 64-bit
Malware analysis
DRAKVUF provides a perfect platform for stealthy malware analysis as its footprint is nearly undetectable from the malware’s perspective. While DRAKVUF has been mainly developed with malware analysis in mind, it is certainly not limited to that task as it can be used to monitor the execution of arbitrary binaries.
Changelog v1.0
Support added to build DRAKVUF with the Meson build system, increasing the speed with which the project can be built.
Several new plugins contributed by the community:
- SprayMon #1397
- CallbackMon #1380
- HideVM #1499
- PTraceMon #1514
- EBPFMon #1517
- UnixSocketMon #1521
- ETWMon #1553
Installation
- Clone the repo: https://github.com/tklengyel/drakvuf.git
- Install all DRAKVUF binaries by running make install after you have built it as described on http://drakvuf.com
- Install additional packages: apt-get install screen apache2 tcpdump vlan openvswitch-switch
- Configure Apache2 by editing /etc/apache2/apache2.conf and change the default folder to /malware_processing and remove “Indexes” from the options. Once done editing, restart Apache: /etc/init.d/apache2 restart.
- Add an OVS bridge to be used by the analysis clones: ovs-vsctl add-br xenbr1
- Edit tools/clone.pl and change the configuration options to match your setup, including LVM VG name and bridge name (if you choose something else other then xenbr1).
- Configure your VM as you see fit, determine what PID you want to use for hijacking and save the domain using xl save, then restore it with xl restore -p -e.
- Start a screen session with logging enabled to run dirwatch: screen -L -d dirwatch [config options]. Config options required are:
Usage
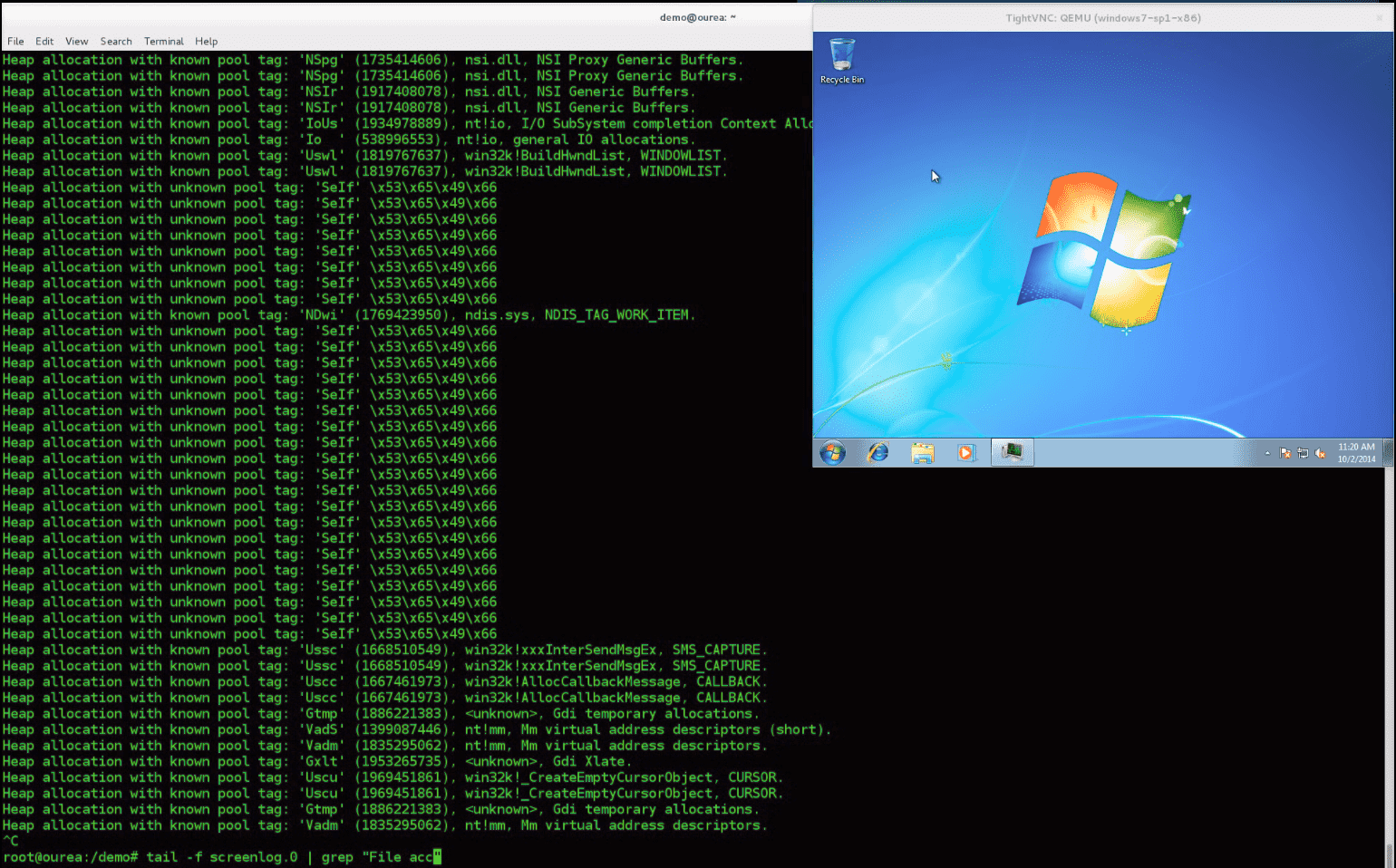
Demo
DRAKVUF (C) 2014-2016 Tamas K Lengyel
Source: https://github.com/tklengyel/