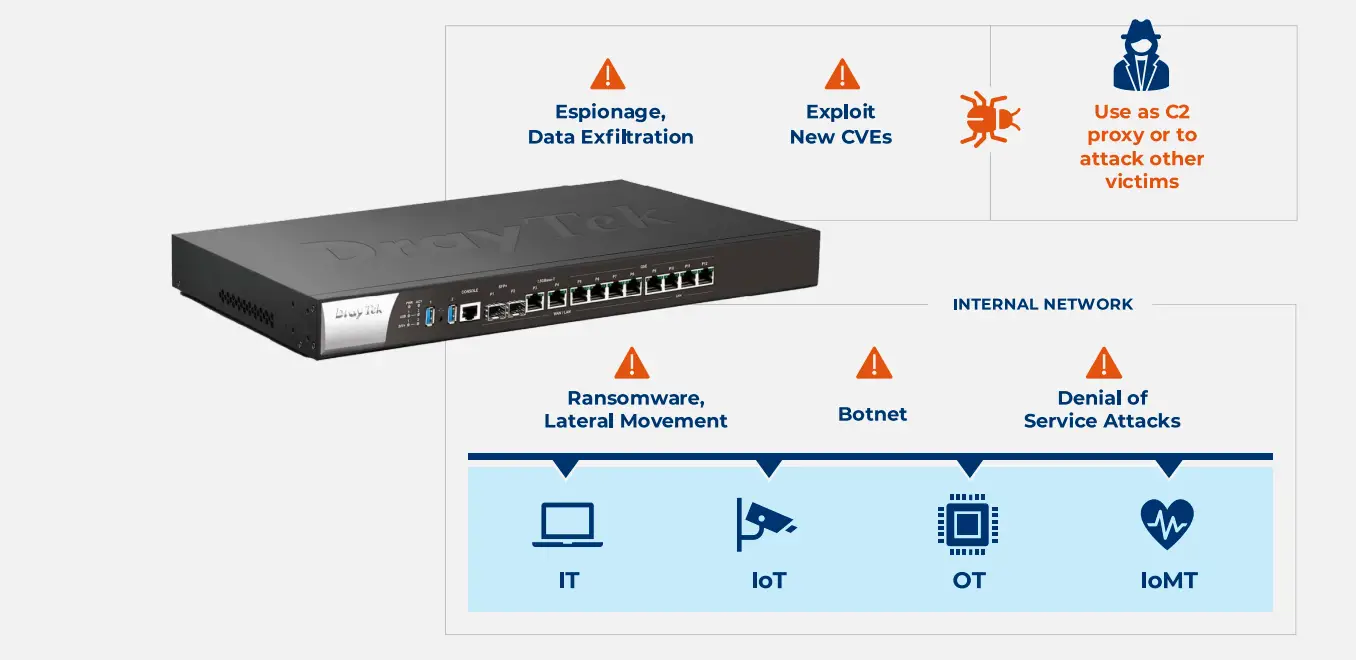
Potential attack scenarios | Image: Forescout
Experts from Forescout have uncovered 14 vulnerabilities in DrayTek routers, potentially allowing malicious actors to gain full access to these devices and use them as entry points into the networks of large enterprises and private households. Among the identified issues, two are rated as critical, nine as high risk, and three as medium.
The most severe threat is a buffer overflow vulnerability (CVE-2024-41592) in the router’s web interface function GetCGI(), which could lead to a denial-of-service (DoS) or remote code execution (RCE). Another critical vulnerability (CVE-2024-41585) risks operating system command injection into the binary file recvCmd, used for communication between the host and guest OS.
Below is the comprehensive list of discovered vulnerabilities:
- CVE-2024-41589 (CVSS: 7.5): Utilization of identical administrator credentials across the system (including both guest and main OS). Compromising these credentials could result in complete system takeover.
- CVE-2024-41591 (CVSS: 7.5): The web interface contains the page doc/hslogp1_link.htm, which accepts HTML code via the content parameter in the query string and displays it without filtering, leading to a cross-site scripting vulnerability.
- CVE-2024-41587 (CVSS: 4.9): The web interface allows customization of a welcome message for each user. Insufficient input validation permits the injection of arbitrary JavaScript code, creating a stored cross-site scripting vulnerability.
- CVE-2024-41583 (CVSS: 4.9): The web interface enables setting the router’s name, displayed on various pages. Due to inadequate input validation, it is possible to inject arbitrary JavaScript code.
- CVE-2024-41584 (CVSS: 4.9): The login page wlogin.cgi in the web interface accepts the sFormAuthStr parameter for CSRF protection. This parameter’s value is displayed on the corresponding web page without filtering, allowing limited JavaScript code injection.
- CVE-2024-41592 (CVSS: 10): The GetCGI() function of the web interface, which processes HTTP request data, has a buffer overflow vulnerability when handling query string parameters.
- CVE-2024-41585 (CVSS: 9.1): The binary file recvCmd, used for data exchange between the main and guest OS, is susceptible to operating system command injection attacks.
- CVE-2024-41588 (CVSS: 7.2): CGI pages /cgi-bin/v2x00.cgi and /cgi-bin/cgiwcg.cgi in the web interface are vulnerable to buffer overflows due to the absence of length checks on query string parameters when using the strncpy() function.
- CVE-2024-41590 (CVSS: 7.2): Multiple CGI pages in the web interface exhibit buffer overflow vulnerabilities owing to insufficient validation of data passed to the strcpy() function. Exploitation requires valid credentials.
- CVE-2024-41586 (CVSS: 7.2): The web interface page /cgi-bin/ipfedr.cgi is vulnerable to stack overflow when processing excessively long query strings.
- CVE-2024-41596 (CVSS: 7.2): Several buffer overflow vulnerabilities in the web interface arise from the lack of checks when processing CGI form parameters.
- CVE-2024-41593 (CVSS: 7.2): The ft_payloads_dns() function in the web interface contains a heap buffer overflow vulnerability due to an error in the length argument of the _memcpy() call, potentially leading to buffer overrun and memory corruption.
- CVE-2024-41595 (CVSS: 7.2): Multiple CGI pages in the web interface lack boundary checks during read and write operations related to various interface settings, which can cause denial-of-service conditions.
- CVE-2024-41594 (CVSS: 7.6): The web server backend for the web interface uses a static string to initialize the random number generator in OpenSSL for TLS, potentially leading to information leakage and man-in-the-middle (MitM) attacks.
Forescout’s analysis revealed that approximately 704,000 DrayTek routers have an open web interface, rendering them easy targets for attacks. The highest concentrations of these devices are in the United States, Vietnam, the Netherlands, Taiwan, and Australia.
Following responsible disclosure of the vulnerabilities, DrayTek released patches for all identified flaws, including critical ones and those affecting devices that have reached end-of-life status. Experts urgently recommend updating device firmware and disabling remote access to the router’s web panel if it is not in use.
Related Posts:
- DrayTek Router 0day Vulnerability
- Critical vulnerability in Synology Router Manager
- CISA Issues Alert: Three Actively Exploited Vulnerabilities Demand Immediate Attention