Recently, routers made by DrayTek, a Taiwanese company, were exposed to the 0day vulnerability. An attacker could use the vulnerability to modify the DNS configuration on some routers. Then, through a man-in-the-middle attack, the user was redirected to a phishing website to steal data. More than 800,000 devices are expected to be affected.

In May 2018, we became aware of new attacks against web-enabled devices, which includes DrayTek routers. The recent attacks have attempted to change DNS settings of routers.” reads the security advisory.
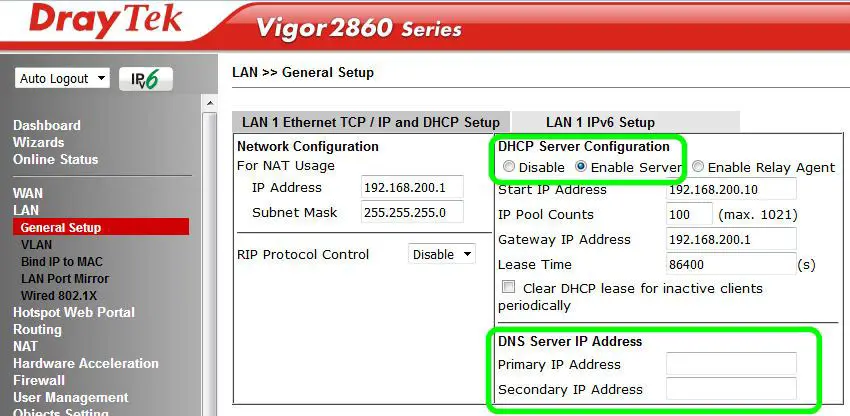
” If you have a router supporting multiple LAN subnets, check settings for each subnet. Your DNS settings should be either blank, set to the correct DNS server addresses from your ISP or DNS server addresses of a server which you have deliberately set (e.g. Google 8.8.8.8). A known rogue DNS server is 38.134.121.95 – if you see that, your router has been changed.
Affected version
- Vigor120 version < 3.8.8.2
- Vigor122 version < 3.8.8.2
- Vigor130 version < 3.8.8.2
- VigorNIC 132 version < 3.8.8.2
- Vigor2120 version < 3.8.8.2
- Vigor2132 version < 3.8.8.2
- Vigor2133 version < 3.8.8.2
- Vigor2760D version < 3.8.8.2
- Vigor2762 version < 3.8.8.2
- Vigor2832 version < 3.8.8.2
- Vigor2860 version < 3.8.8
- Vigor2862 version < 3.8.8.2
- Vigor2862B version < 3.8.8.2
- Vigor2912 version < 3.8.8.2
- Vigor2925 version < 3.8.8.2
- Vigor2926 version < 3.8.8.2
- Vigor2952 version < 3.8.8.2
- Vigor3220 version < 3.8.8.2
- VigorBX2000 version < 3.8.8.2
- VigorIPPBX2820 version < 3.8.8.2
- VigorIPPBX3510 version < 3.8.8.2
- Vigor2830nv2 version < 3.8.8.2
- Vigor2820 version < 3.8.8.2
- Vigor2710 version < 3.8.8.2
- Vigro2110 version < 3.8.8.2
- Vigro2830sb version < 3.8.8.2
- Vigor2850 version < 3.8.8.2
- Vigor2920 version < 3.8.8.2
Solution
1. Update the firmware immediately, or upgrade immediately after the available updates are released.
Updated link: https://www.draytek.co.uk/support/downloads
Before upgrading, back up your current configuration for future recovery (System Maintenance -> Configuration Backup).
2. Check the DNS and DHCP settings on the router. If you have a router that supports multiple LAN subnets, check the settings for each subnet. Currently, a known malicious DNS server is 38.134.121.95.
3. If the router has enabled remote access, disable it when it is not needed, and use access control lists as much as possible. If you have not yet updated the firmware, disable remote access.
4. Always use a secure connection (SSL/TLS1.2) for the router. Disable non-SSL/TLS connections.
Source, Image: Draytek