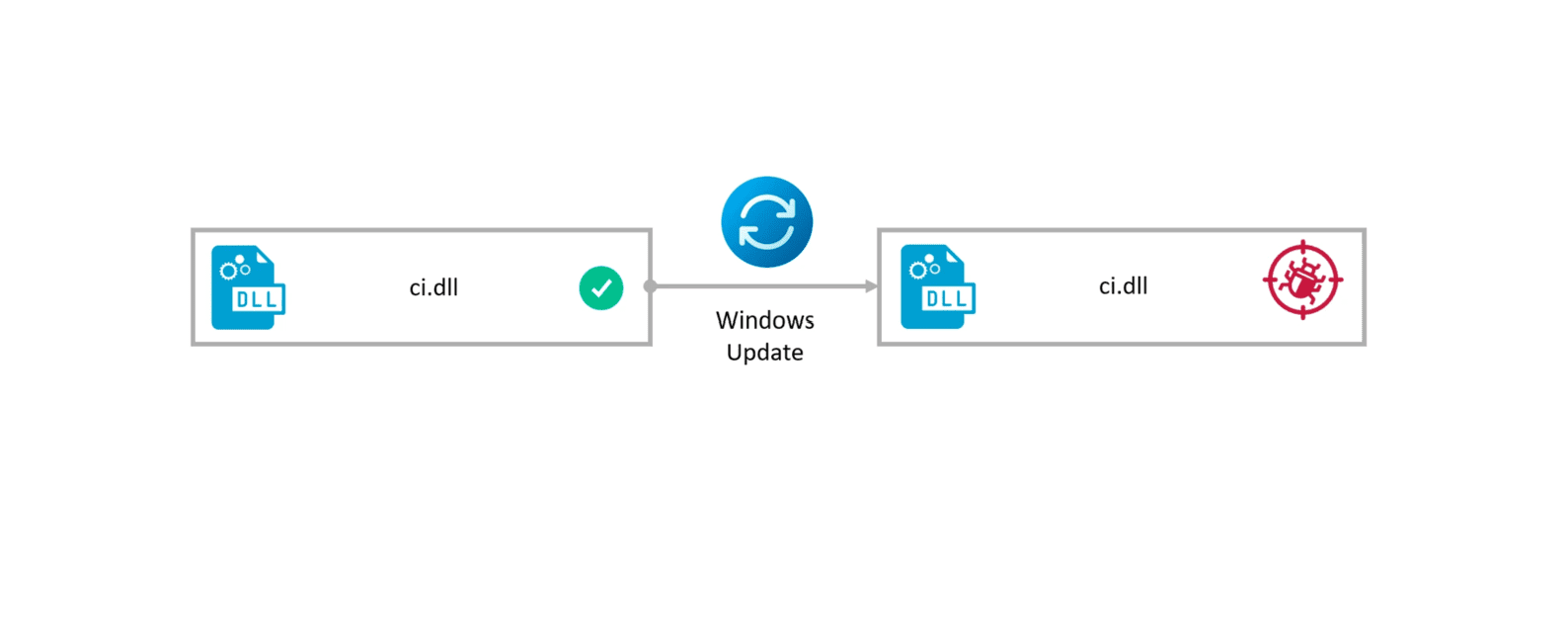
Downgrading only ci.dll to its unpatched version works well against a fully patched Windows 11 23h2 machine | Image: SafeBreach
SafeBreach specialist Alon Leviev has discovered that attackers can exploit outdated Windows kernel components to bypass critical protections, such as Driver Signature Enforcement, enabling the installation of rootkits even on fully updated systems. This attack method is possible through interception of the Windows Update process, allowing vulnerable, obsolete components to be installed on an updated system without altering its status.
Leviev has also developed a tool called Windows Downdate, which enables a customized rollback, rendering a “fully updated” system susceptible to previously patched vulnerabilities. Leviev stated that he could reactivate previously mitigated vulnerabilities, effectively undermining the concept of a “fully updated” Windows system. This technique has been termed a Downgrade Attack.
Using this approach, the researcher identified a new vulnerability, CVE-2024-21302 (CVSS score: 6.7), which allows privilege escalation on Windows devices, including virtual machines and other features. Microsoft quickly addressed this vulnerability, as it breached the so-called “security boundary.” However, the method of intercepting updates remains unchanged, as it is not classified as a direct security violation.
Despite the fix, the flaw remains hazardous, as intercepting the update process allows attackers to reintroduce old issues into the system. One of the attack targets is the Driver Signature Enforcement (DSE) feature, which typically prevents unsigned drivers from running. By reinstating a vulnerability in DSE, a hacker can load malicious drivers into the system, concealing their actions while bypassing Windows security mechanisms.
The researcher also demonstrated that other Windows security features, such as Virtualization-Based Security (VBS), can be circumvented by modifying registry keys. If VBS is not configured for maximum security, crucial files like SecureKernel.exe can be replaced with vulnerable versions, allowing attackers to bypass protections and manipulate system components. Microsoft has protections at the UEFI level, though enabling them requires additional configuration. Full protection is only available with VBS enabled alongside mandatory UEFI lockdown.
Microsoft has responded, stating that it is developing updates to address these vulnerabilities and creating mechanisms to block outdated VBS system files. However, precise release dates for the fixes are not provided, as extensive testing is needed to prevent system failures and compatibility issues.
Related Posts:
- CVE-2024-21302, CVE-2024-38202: Zero-Day Vulnerabilities Expose Windows Systems to “Unpatching” Attacks
- AgentTesla and Beyond: McAfee Reveals Diverse VBS Malware Tactics
- The Monero crypto-currency mining activity affects more than 30 million users worldwide